The Digital Operational Resilience Act (DORA) came into force in the European Union on January 16, 2023. Enforcement began on January 17, 2025.
The DORA regulation affects the financial sector, aiming to standardize frameworks and procedures, improve transparency, and bolster security to make the sector more resilient to growing threats. We look at what DORA is, what companies it affects, what is required for compliance, and more.
What is DORA, the Digital Operational Resilience Act?
The Digital Operational Resilience Act (DORA) is an active regulation in the European Union, affecting entities in the financial sector in all EU member states.
The aim of the regulation is to mitigate any severe operational disruption and strengthen IT security in the EU financial sector, including for banking, insurance, and investment firms.
This includes both resisting threats and recovering from any incidents that may occur. The DORA law also harmonizes existing rules for the financial sector governing operational resilience.
20 different types of financial entities and information and communications technology (ICT) third-party service providers are affected by the regulation.
Just in Germany, over 3,600 companies will be required to comply with DORA, so its effects will be felt widely in the EU financial sector.
What is digital operational resilience?
What does digital operational resilience actually mean? What does it require of the people actually working in the financial sector, and what are these companies’ responsibilities for their operations, partners, customers, and regulators?
DORA’s definition of digital operational resilience reads:
“…the ability of a financial entity to build, assure and review its operational integrity and reliability by ensuring, either directly or indirectly through the use of services provided by ICT third-party service providers, the full range of ICT-related capabilities needed to address the security of the network and information systems which a financial entity uses, and which support the continued provision of financial services and their quality, including throughout disruptions.”
Why is DORA necessary?
Like many other industries, the financial sector is highly reliant on technology — a reliance that continues to grow — and much of that technology that enables a wide variety of functions and services is provided by third parties.
The more “moving parts” that are required in business operations, as with using many third-party service providers, the greater the number of security risks and points of potential failure there are in case of attack.
Companies operating in the financial sector — including the third-party service providers — also need access to increasingly large volumes of often sensitive data.
This means that in addition to protecting their operations and information confidential to their business dealings, these companies also need to protect their customers’ and partners’ data and privacy as that data moves through the financial ecosystem. The DORA regulation also dovetails closely with laws like the GDPR as a result.
The interconnected nature of the financial sector, reliance on third-party providers and technology, and the amount of data in motion all increase vulnerability to cyber attacks and other security risks.
Especially if there are any issues with communications, procedures that may contradict each other, issues with bureaucracy, security gaps, non-standard systems or tools, etc. And the frequency of attacks on the financial sector that can exploit these possible issues is increasing.
If these vulnerabilities are exploited, the damage and disruption would immediately affect financial companies and their customers, but could also cross industries, borders, and even spread into the broader European economy.
So strong resilience in financial digital operations is increasingly critical. That means clear expectations for maintaining security and consistency in operations, frameworks for organizations to follow, procedures in case of incidents, stringent regulation of third-party providers, and other requirements.
How is ICT risk defined in DORA?
Cyber threats can come from innumerable sources today, and that will only increase as technology continues to advance. For the purposes of the regulation, DORA defines ICT risk as:
“…any reasonably identifiable circumstance in relation to the use of network and information systems which, if materialised, may compromise the security of the network and information systems, of any technology dependent tool or process, of operations and processes, or of the provision of services by producing adverse effects in the digital or physical environment.”
What are ICT services and ICT third-party service providers?
As noted, companies in the financial sector increasingly rely on technology, which is also increasingly supplied by external partners and vendors. These external entities are the third-party information management and communications (ICT) service providers.
The DORA law defines ICT services as:
“…digital and data services provided through ICT systems to one or more internal or external users on an ongoing basis, including hardware as a service and hardware services which includes the provision of technical support via software or firmware updates by the hardware provider, excluding traditional analogue telephone services.”
DORA defines an ICT third-party service provider simply as, “an undertaking providing ICT services”.
What areas of ICT does DORA cover?
DORA covers six key areas of the financial sector, helping ensure an in-depth and holistic approach to digital security.ICT risk management: Principles and requirements for an ICT risk management framework
ICT third-party risk management: Risk monitoring for third-party providers and key contractual provisions
Digital operational resilience testing: Basic and advanced testing
ICT-related incidents: General requirements for handling security incidents and reporting of major incidents to competent authorities
Information sharing: Exchange of information and intelligence on cyber threats
Oversight of critical third-party providers: Framework and oversight body for critical ICT third-party providers
As noted in a 2025 PWC whitepaper on DORA, digital operational resilience has five main pillars, which closely reflect DORA’s key areas of focus.
- An ICT risk management framework
- ICT-related incident management, classification, and reporting
- Digital operational resilience testing
- An ICT third-party risk management and oversight framework
- Information sharing on cyber threats
Who enforces DORA?
The DORA law will be overseen and enforced by European Supervisory Authorities (ESA), established by the European Parliament and Council. The ESA includes three organizations:
- European Banking Authority (EBA)
- European Insurance and Occupational Pensions Authority (EIOPA)
- European Securities and Markets Authority (ESMA)
ESA responsibilities are closely linked to the operational pillars, and center around introducing and maintaining coordination and compliance with DORA across the EU financial sector to strengthen transparency and accountability. Responsibilities include:
- Developing and harmonizing technical standards and guidelines for ICT risk management
- Incident reporting
- Testing frameworks
- Oversight of critical third-party ICT service providers
- Monitoring compliance
- Facilitating cooperation between national competent authorities
- Maintaining registers of significant ICT incidents and critical third-party ICT providers
On January 17, 2024, the ESAs published the first set of technical standards under DORA. These aimed at “enhancing the digital operational resilience of the EU financial sector by strengthening financial entities’ Information and Communication Technology (ICT) and third-party risk management and incident reporting frameworks.”
These joint final draft technical standards include:
- Regulatory Technical Standards (RTS) on the ICT risk management framework and simplified ICT risk management framework
- RTS on criteria for the classification of ICT-related incidents
- RTS to specify the policy on ICT services supporting critical or important functions provided by ICT third-party service providers (TPPs)
- Implementing Technical Standards (ITS) to establish the templates for the register of information
What are national competent authorities (NCA) under DORA?
National competent authorities (NCA) are regulatory bodies that each EU Member State designates to oversee and enforce compliance with DORA’s requirements within their jurisdiction. Germany’s primary NCA is the Federal Financial Supervisory Authority (BaFin), Ireland’s is the Central Bank of Ireland, and so on.
The NCAs work with the ESAs, so some responsibilities overlap, though each NCA only covers one country, and the ESAs are responsible for all of the EU.
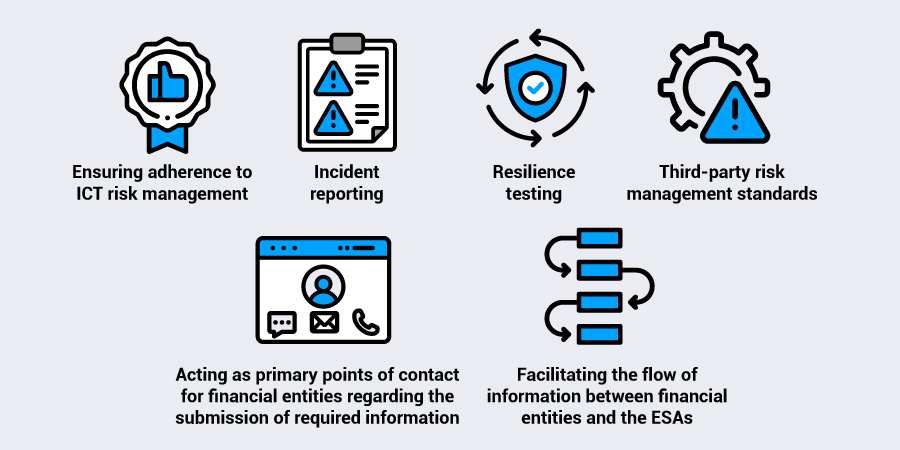
The NCAs have a variety of responsibilities for supervising entities in the financial sector, including:
- Ensuring adherence to ICT risk management
- Incident reporting
- Resilience testing
- Third-party risk management standards
- Acting as primary points of contact for financial entities regarding the submission of required information
- Facilitating the flow of information between financial entities and the ESAs
Regulation and oversight of third-party ICT service providers under DORA
Because of the prevalence of third-party providers and technology in use in the EU financial sector, unsurprisingly there is a lot of coverage in DORA for managing those relationships, tracking and securing their operations, and mitigating risks.
Identifiers for third-party ICE service providers
One DORA requirement is that third-party ICT service providers be identifiable via a specific ID. Such IDs enable regulators and financial institutions to track third-party ICT providers, which helps to mitigate risks of relying on external partners, ensure accountability, and enable better decision-making for operational risk management.
There are two options for these organizational identifiers.
Legal Entity Identifier (LEI) is a 20-character alphanumeric code that can uniquely identify legal entities that are involved in financial transactions. It enhances transparency as it is a standardized and globally recognized means of identification. It is part of the Global LEI System (GLEIS).
European Unique Identifier (EUID) is a European-specific identifier that is primarily used in the EU’s business registry system. While recognized within Europe, it is not globally recognized or interoperable like the LEI.
What are critical ICT third-party service providers under DORA?
Some ICT third-party service providers are more important or pose a greater risk if compromised than others. The ESA will be identifying and designating critical ICT third-party service providers in the financial sector. The designation will be based on information from the companies that use these services.
Those designated will be companies providing services with functions that are critically important as part of the financial industry’s backbone. They will be subject to enhanced regulatory scrutiny and oversight.
How can the EU financial sector comply with DORA?
DORA is already in effect and being enforced, so companies shouldn’t be scrambling to comply at this point. Compliance requirements and oversight will evolve, however, as regulatory bodies publish additional guidelines and more critical third-party providers are identified.
There are a number of actions and best practices companies can focus on for compliance.
- Develop and adopt a robust framework for ICT risk management: Create and maintain strong comprehensive processes to identify, monitor, and mitigate risks, and update them regularly as technologies, partners, and cyber threats evolve.
- Strengthen third-party risk management: Review existing ICT providers and contracts to ensure DORA’s provisions are covered and enforced. Maintain detailed records of all third-party partner and vendor relationships and how they intersect with operations.
- Implement robust programs for resilience testing: Create plans for and regularly rest digital operational resilience to assess, analyze, and optimize capabilities and responses.
- Optimize incident reporting mechanisms: Develop clear workflows to identify, address, and report ICT-related incidents. Review and update them regularly.
- Foster collaboration and information-sharing: Connect with other companies and peers in the industry to discuss concerns, insights, innovations, threats, and best practices.
How Usercentrics helps financial entities with regulatory compliance
To support financial entities, as an ICT service provider, Usercentrics’ consent management platform adheres to the highest standards of security, data protection, and availability. We regularly review these standards, which enables customers that are financial entities to comply with DORA.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.