Cloud computing is essential for businesses around the world, with estimates of 94% of all companies worldwide using cloud computing in some form.
But as adoption grows, so do security risks. Data breaches, misconfigurations, and compliance failures are increasingly common. Each cloud infrastructure has its own vulnerabilities, and without the right protections, sensitive data could be exposed.
A cloud service provider’s security measures can make all the difference for your defense against cyber threats. Choosing the wrong one could lead to legal trouble, financial losses, and reputational harm.
Here’s how to protect your data in the cloud.
What is cloud compliance?
Cloud compliance means that businesses meet legal, regulatory, and security requirements when using cloud-based systems.
Cloud security and compliance require following industry standards and relevant regulations for data storage, access control, and risk management. Below, we’ll delve into how these laws dictate how businesses must handle, store, and protect sensitive data in the cloud.
For example, just as businesses must follow local zoning laws to operate in a specific location, organizations must also comply with cloud regulations to keep data secure and confidential within a given region. This involves navigating a mix of local, national, and international regulations and industry standards. It’s important to make sure your cloud service provider (CSP) doesn’t put you at risk of violating any of these compliance requirements.
Why is cloud compliance essential?
Cloud data compliance is more important than just following regulations. It’s about trust, security, and business continuity. Companies store vast amounts of sensitive data in the cloud, from customer details to proprietary business information. Without proper cloud security compliance, this data becomes vulnerable to breaches, leaks, and unauthorized access.
Noncompliance can lead to severe penalties, legal consequences, and financial losses. Beyond legal risks, failing to comply can erode customer trust. A single compliance failure can cause reputational damage that can take years to repair.
Cloud compliance related regulations
The cloud powers essential business capabilities — from data analytics and automation to customer management and operations — but it comes with regulatory responsibilities. Whether you’re handling customer profiles, financial records, campaign data, compliance reporting, or consumer behavior tracking, cloud compliance plays an important role across departments, not just for IT.
For instance, marketing teams need to understand these global regulations as they directly impact how you can collect, store, use, and transfer customer data in the cloud. These requirements affect everything from email marketing and analytics to personalization and customer segmentation.
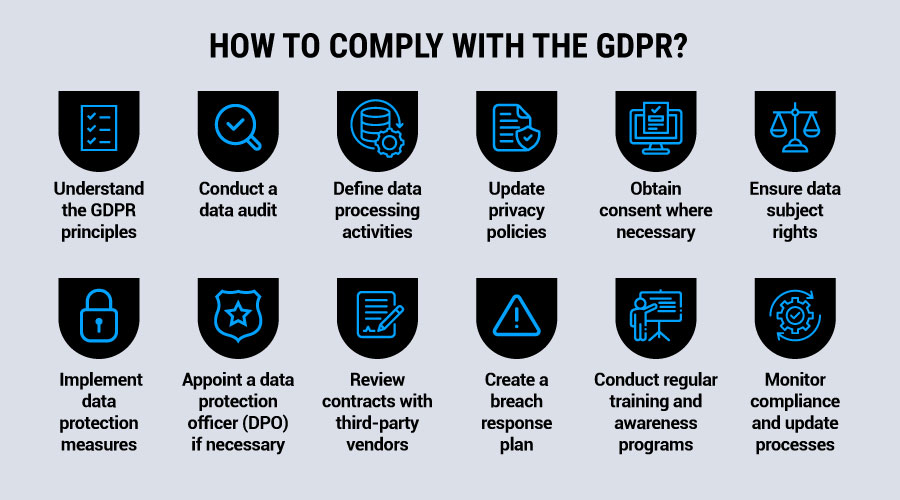
GDPR cloud compliance
The General Data Protection Regulation (GDPR) is one of the most strict and comprehensive data protection laws in the world. It applies to any business, regardless of location, that processes the personal data of EU citizens. It aims to give individuals more control over their data while holding businesses accountable for how they collect, store, and use that information. The GDPR also has strict requirements for how data can be transferred internationally, which is often relevant when companies use cloud services.
For companies leveraging the cloud, GDPR cloud security compliance standards require:
- Data protection by design and default: Cloud services must be built with privacy in mind so that data is protected at every stage.
- Encryption and anonymization: Sensitive data should be encrypted or anonymized to minimize risks in case of a breach.
- Strict access controls: Only authorized personnel should have access to personal data, with role-based permissions and authentication mechanisms.
- Data subject rights: Businesses must provide users with rights such as access to their data, the ability to correct inaccuracies, and, in some cases, the right to have data erased.
- Cloud vendor accountability: If your company uses third-party cloud providers, you must ensure that those providers are also GDPR-compliant, often through data processing agreements (DPAs).
California Consumer Privacy Act and cloud compliance
The California Consumer Privacy Act (CCPA) grants the state’s residents more transparency and control over their personal data. Businesses that collect data from California consumers must:
- Provide clear disclosures about data collection and usage
- Offer an opt-out mechanism to prevent data from being sold, shared, or used for profiling or targeted advertising
- Enable users to request access to, modify, or delete their personal information
Cloud providers that process data for CCPA-covered businesses must implement reasonable security measures to protect consumer information.
Federal Risk and Authorization Management Program
The Federal Risk and Authorization Management Program (FedRAMP) is a US government framework that establishes security standards for cloud service providers working with federal agencies.
Designed to achieve a high level of cybersecurity, FedRAMP requires cloud providers to undergo a rigorous security assessment before they can offer services to government entities.
It also requires cloud providers to implement standardized security controls based on the NIST 800-53 framework, which covers encryption, identity management, and incident response.
For cloud providers seeking to work with federal agencies, FedRAMP certification is a critical requirement that demonstrates a commitment to strong cybersecurity practices.
Health Insurance Portability and Accountability Act
The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for protecting healthcare data in the United States. Cloud providers handling electronic Protected Health Information (ePHI) must implement strong security measures, including encryption, access controls, and audit trails.
Covered entities, such as healthcare providers and insurers, must also have their cloud vendors sign Business Associate Agreements to confirm compliance.
Payment Card Industry Data Security Standard
Any business processing credit card transactions must comply with the Payment Card Industry Data Security Standard (PCI DSS), which outlines stringent security requirements for cloud-stored payment data.
This includes maintaining a secure network, encrypting cardholder information, and conducting regular security assessments.
Cloud security compliance standards
When selecting cloud services and solutions, look beyond basic regulations to consider important industry security standards.
For example, ISO 27001 is a widely recognized benchmark for data protection excellence. Cloud providers with this certification maintain comprehensive security measures and conduct regular risk assessments. Their data stays protected through ongoing monitoring and strong safeguards.
SOC 2 certification is another recognized security certificate. To earn it, cloud services are evaluated across five essential areas: security, reliability, data processing, confidentiality, and privacy. When a provider meets SOC 2 standards, it demonstrates their commitment to protecting customer information through strict internal controls.
Choosing tools with these certifications offers clear benefits: better data protection, reduced compliance risks, and enhanced customer trust. These standards help ensure you’re partnering with providers who take security seriously.
Cloud compliance framework and governance
Cloud compliance frameworks and governance are important for organizations using cloud services to keep their operations secure and aligned with regulations.
These frameworks offer clear guidelines for managing cloud environments, which help businesses address security risks and stay up to date with changing regulations. Organizations meet both legal and industry standards by following rules for how data is collected, stored, and processed. A strong framework includes compliance with regulations, security measures, risk management, and clear governance practices.
Governance involves defining roles, creating policies, and managing cloud resources to minimize security risks and stay legally compliant. This often means setting up a team that focuses on developing policies, checking compliance, and managing resources in the cloud.
For example, centralizing monitoring enables organizations to track performance, security, and compliance all in one place, so it’s easier to identify and correct issues. Automating tasks can also improve efficiency and reduce mistakes.
By encouraging a culture of responsibility and regularly checking for risks, organizations can keep their cloud operations secure, compliant, and aligned with business goals. This helps prevent data breaches and legal issues, and enables smooth cloud operations overall.
Common cloud security compliance challenges
Marketing teams often face unique challenges when it comes to cloud compliance. The pressure to deliver personalized experiences while protecting customer privacy can be a difficult balance.
One major challenge is managing multiple cloud-based marketing tools, each with its own security requirements. From email marketing platforms to analytics tools, maintaining consistent compliance across systems can be overwhelming.
Sharing data with agencies and vendors adds another layer of complexity. When you’re collaborating with external partners, especially if they are located internationally, maintaining compliance becomes even more crucial, and more challenging.
Lastly, legacy systems and new cloud solutions are not always fully compatible. This can create security gaps that put your customer data at risk. And, as marketing technology evolves rapidly, keeping up with changing compliance requirements becomes an ongoing challenge.
Cloud security compliance requirements and best practices
You can achieve success in cloud compliance by following proven best practices that protect your data without hampering your marketing efforts.
Encryption
Modern encryption is your first line of defense against data breaches. Always encrypt sensitive customer data, whether it’s contact information, behavior tracking, or purchase history. Doing so means that even if unauthorized access occurs, the data remains unreadable and protected.
Access controls
Access controls are the backbone of cloud security. This feature helps ensure that only the right people can access sensitive data.
Begin by creating user roles that align with job functions and by managing permissions based on specific needs. Then, regularly review user access to help identify any discrepancies before they become security risks.
Security assessments
Regular security assessments help identify vulnerabilities before they can be exploited. This includes vulnerability scanning to find system weaknesses as well as penetration testing, which tests your defenses by simulating real-world attacks.
Additionally, configuration reviews help ensure your systems are set up correctly, with the right security settings in place. They help to both identify misconfigurations and ensure compliance with security standards.
Multi-factor Authentication (MFA)
Multi-factor authentication (MFA), also called two-factor authentication (2FA) adds an extra layer of protection by requiring multiple forms of verification. This might include a password or passcode, a time-based one-time password (TOTP), or even biometric verification.
Whatever measure you choose, it’s important to implement it for all accounts with administrative access. MFA significantly reduces the chances of unauthorized logins.
Privacy by design
Build privacy best practices into your marketing processes from the start. This means considering data protection at every stage, from campaign planning to execution. For example, when designing a new lead generation form, consider what data you really need, how it may be transferred to partners, and how you’ll protect it.
Principle of least privilege
Only give team members access to the data they need for their specific role. For instance, your social media manager might not need access to customer payment information, while your email marketing specialist might not need access to website analytics.
Zero Trust architecture
Adopt a “never trust, always verify” approach to security. This means requiring authentication for every user and device that tries to access your marketing systems, regardless of their location or network connection.
Continuous monitoring and auditing
Regular security checks help identify and address potential issues before they become problems. Set up automated monitoring systems that alert you to unusual activity, and conduct regular audits of your marketing technology stack.
Cloud compliance solutions and tools
The right tools can make cloud compliance management possible internally. Here’s what you need to know about key solutions.
Cloud-native security platforms
Cloud-native security platforms provide comprehensive security features designed specifically for cloud environments. Look for solutions that offer real-time monitoring, automated compliance checks, and integrated threat detection. They should seamlessly integrate with your current tech stack while providing clear visibility into your security status.
Compliance automation tools
Automation takes the heavy lifting out of compliance management. These tools can continuously monitor your systems, automatically document compliance efforts, and alert you to potential issues. This helps maintain security while letting your marketing team focus on creating campaigns.
Third-party auditing services
Regular external audits provide an independent assessment of your compliance status. These services can identify gaps in your security measures and recommend improvements. They’re particularly valuable when dealing with complex regulations like the GDPR or CCPA.
Secure your cloud to secure your data
Cloud compliance is about protecting what matters: your business, your customers, and your reputation. With the right approach and tools, you can use the cloud safely and keep data secure.
By following these guidelines and implementing appropriate security measures, your company can confidently leverage cloud technologies while maintaining compliance. Remember, comprehensive security practices not only protect your data but also build trust with your customers.


