The European Union (EU) has some of the world’s most stringent data privacy laws with the General Data Protection Regulation (GDPR) and ePrivacy Directive. The long proposed ePrivacy Regulation would have brought changes to data protection and cookie consent and broadened the scope of which organizations would have been impacted.
As of early 2025, however, the data privacy landscape in the EU has changed significantly from the one regulators were planning for in prior decades. We look at what the ePrivacy Directive is, how data privacy and processing are protected today, and what the future looks like.
What is the ePrivacy Directive (ePD)?
The EU ePrivacy Directive (sometimes known as the “cookie law”) was enacted in 2002 and updated in 2009. It specifically addresses privacy issues in electronic communication.
The ePD mandates:
- Confidentiality of communication over public networks
- Prior user consent for cookie use
- Setting guidelines for the security of electronic communication services
- Regulation of direct marketing practices
Cookie consent banners became more prominent after the ePrivacy Directive’s enactment, as they are a practical way to provide required notifications about data collection and use, and to obtain explicit and granular consent from users on websites, apps, or other connected platforms.
Read about optimize cookie banners now
The ePD is required to be incorporated into national laws of EU member states, leading to variations in enforcement across the Union. It is not a pan-EU regulation, however, like the General Data Protection Regulation (GDPR).
In November 2023, the European Data Protection Board (EDPB) issued new guidelines that widened the scope of technologies covered under the directive.
Who does the ePrivacy Directive apply to?
The ePD applies to organizations that provide electronic communications services or process personal data from EU residents. The groups that the ePD primarily applies to include:
Businesses that process personal data: Whether they are located in or outside the EU, companies engaged in digital marketing, tracking via cookies, or otherwise using digital means to collect personal data via websites or other digital services.
Third parties using tracking technologies: Any third parties, like social media platforms, advertisers, or analytics providers, that use cookies or other tracking technologies on websites or apps to track user behaviors or activities.
Electronic communications services providers: Like internet service providers (ISP), telephone service providers, or public communications networks, which enable electronic communications and collection of personal data.
Website operators: For sites that use cookies or other tracking technologies to collect information about site visitors, customers, etc.
What actions does the ePrivacy Directive prohibit?
The ePD includes a number of specific prohibitions to protect users’ privacy rights:
- Any interception, storage, monitoring, scanning, or otherwise surveilling of electronic communications data by anyone other than the end users (unless expressly permitted by the regulation)
- Use of tracking technologies for non-technically necessary purposes without obtaining explicit consent
- Gaining access to information stored on a user’s terminal equipment (e.g. phone or computer) without their consent
- Sending unsolicited electronic communications or spam, covering unsolicited emails, text messages, and automated calling systems
- Processing metadata derived from electronic communications (such as location data, call times, and recipient information) without user consent or another legal basis
How has the ePrivacy Directive been updated?
Article 5(3) of the ePrivacy Directive provides that before a company or website can store information on or get information from a user’s device (like a computer or smartphone), they must obtain prior consent from the user.
Under the Guidelines 2/2023 on the Technical Scope of Article 5(3) of ePrivacy Directive, the European Data Protection Board (EDPB) expanded the ePD’s application for storing or accessing information on a user’s device.
The EDPB adopted a wide reading of what constitutes terminal equipment (like smartphones or personal computers) and the nature of information, suggesting that many digital tracking methods will require prior consent unless they are necessary for delivering a requested service.
The guidelines specifically address the use of several modern tracking technologies that have become prevalent in digital marketing and online tracking.
URL and pixel tracking
Tracking pixels are tiny images embedded in websites or emails, linked to a server. When an email containing a tracking pixel is opened or a web page with a tracking pixel is visited, it allows the server to record the action and capture details, such as the time the email was opened, the IP address of the recipient, and the type of device used. URL tracking links to websites help identify where visitors come from.
Local processing
Sometimes, websites use APIs to access information stored on a user’s device, such as location data. If processed information is made available over the network, it is considered gaining access to stored information under ePD guidelines.
Tracking based on IP address only
Some technologies rely only on the collection of the IP address for the tracking of users. If the IP address originates from the terminal equipment of the user, Article 5(3) of the ePrivacy Directive would apply.
Internet of Things (IoT) reporting
Under ePD guidelines, companies require user consent for data collection and processing by devices connected directly or indirectly to the internet. This applies to smart devices like fridges or fitness trackers, whether they send data directly or through another device like a smartphone.
Unique Identifier
Unique Identifiers (UID) are special codes that are attached to a user’s online data to signify that it belongs to the user. It often comes from persistent personal data, or personal information that doesn’t change much over time, such as email addresses, usernames or account IDs, or date of birth.
UIDs are used to recognize users across different websites or apps. When a website tells a user’s browser to send this data, it’s accessing information on the device and invokes Article 5(3) of the ePD.
What is the ePrivacy Regulation (ePR)?
The proposed ePrivacy Regulation was a legal framework that was intended to update and replace the existing ePrivacy Directive, giving it jurisdiction across the EU.
The primary focus of the proposed ePrivacy Regulation was to enhance privacy protections in electronic communications beyond traditional telecommunications providers, including the text, images, speech, videos, and metadata. The proposed regulation would also have covered communication services like instant messaging applications, VoIP services, and email.
Who would the ePrivacy Regulation have applied to?
The ePrivacy Regulation would have applied to any business processing data in connection with any form of online communication service, using online tracking technologies, or engaging in electronic direct marketing, including both natural and legal persons involved in electronic communication.
Examples of organizations to which the ePR would have applied:
- Website owners
- Owners of apps that have electronic communication as a component
- Natural or legal persons sending direct marketing communications
- Telecommunications companies
- Messaging service providers (e.g. WhatsApp, Facebook)
- Internet access providers (e.g. a café providing open Wi-Fi access)
- Providers of machine-to-machine communications (Internet of Things)
What happened to the ePrivacy Regulation?
The proposal to expand the ePD and implement the ePR dates back to 2017. The plan was to make it a full regulation to complement the GDPR to protect privacy and personal data in electronic communications in the EU. The ePR would also have had extraterritorial scope. However, the process was delayed for quite some time.
The ePR was officially withdrawn by the European Commission on February 5, 2025 after legislators could not reach agreement on the plan and it was noted that the proposal was growing increasingly dated. The Commission noted that, after years of delays, “The proposal is outdated in view of some recent legislation in both the technological and the legislative landscape.”
Did any law replace the intended ePrivacy Regulation?
The ePrivacy Directive’s guidelines remain in place for EU member states. Also, European Commission spokesman Thomas Regnier has noted that the Digital Services Act (DSA), which came into effect in November 2022, provides a “strong framework to ensure a high level of privacy, especially for minors (Article 28)”.
Among other functions, the DSA regulates use of personal data for advertising. Platforms must obtain prior consent from EU audiences to use their data for advertising. The DSA also bans the use of minors’ data for targeted advertising and prohibits the use of data categorized as sensitive, such as health information or religious or political views, for ads as well in most cases.
Do all cookies require consent under the ePrivacy Directive?
No, under the ePrivacy Directive, cookies that are “strictly necessary” for the delivery of a service explicitly requested by the user do not require consent. These cookies are essential for the basic functioning of the website or to provide the service the user has directly requested, including the following kinds of cookies and uses:
- Maintaining the state of a user’s activities on a website during a browsing session, such as maintaining logged-in status, or the contents of an ecommerce shopping cart
- Supporting security features and to help identify and prevent security risks
- Remembering information entered by the user, such as username, language, or region, to provide a more personalized experience
Read about GDPR and cookies now
While these cookies are exempt from the consent requirement, you are still expected to inform users about the use of such cookies, typically via a cookie and/or privacy policy.
Read about cookie policy now
How does the ePrivacy Directive compare to the GDPR?
The GDPR and ePrivacy Directive share several similarities, including:
- Passed by the European Parliament and Council
- Goal of aligning data privacy laws across the EU
- Apply to processing and protection of personal data of individuals residing in the EU, with extraterritorial scope
- High fines for noncompliance
There are, however, some major differences between the two regulations, which are outlined in the table below.
| GDPR | ePrivacy Directive | |
|---|---|---|
| Scope | Applies to the processing of EU residents’ personal data, irrespective of the technology used. | Focused on the processing of personal data and metadata in electronic communications. |
| Definition | “Personal data” means any data that can be used to identify someone. | Data from “electronic communications” means any data that is communicated electronically, whether or not it can be used to identify someone. |
| Reach | Narrower than the ePD, but still applies to all EU residents and organizations that collect and use their personal data. | Broader than the GDPR since it includes non-identifying personal data, but also applies to all EU residents and organizations that collect and use their personal data. |
| Purpose | To protect the personal data of EU residents, providing them with greater control over their personal information and ensuring that their data is processed securely, transparently, and with explicit consent by organizations. | To ensure privacy and confidentiality in electronic communications involving EU residents, specifically regulating tracking technologies, digital marketing, and the security of users’ communications data. |
| Types of data | Covers any personal data, whether it is electronic or in hard copy format. | Covers only “electronic” communications data, not hard copy data. |
| Lex specialis | GDPR is the less specific law when it comes to electronic communications. Because of this, the ePrivacy Directive takes precedence over the GDPR in electronic communications cases. | The ePrivacy Directive is more specific than the GDPR regarding electronic communications, so takes precedence in cases centering around electronic communications. |
| Applicability | Any controller or processor that collects and/or uses personal data of EU residents. Data controllers are those who decide why and how personal data should be processed, e.g. a company you buy from online. Data processors are the ones doing the actual data processing for the controller, e.g. the payment processor that completes the credit card transaction. | Businesses employing electronic communications that process personal data; third parties using tracking technologies; electronic communications services providers; website, app, or other connected platform operators. |
| Who has rights and protections | Natural persons | Natural and legal persons (i.e. organizations, companies, etc.) |
| Date in force | May 25, 2018 | July 31, 2002 (ePrivacy Regulation proposal withdrawn February 5, 2025) |
When will the ePrivacy Regulation come into force?
The ePrivacy Regulation was initially intended to come into effect alongside the GDPR on May 25, 2018, but was not adopted. The EU Council published a draft, finalized on February 10, 2021, which was then in negotiations between the Council and European Parliament.
If the draft had been approved, it would have passed into law in all 27 EU member states, and there would have been a two-year period before the regulation would be enforced.
As the ePrivacy Regulation has been abandoned by the European Commission, the future status of the regulation or replacement legislation is seriously in doubt.
What are the penalties for ePrivacy Directive violations?
Penalties for ePD violations are levied by data protection authorities of individual EU member states, and a variety of fines have been imposed for breaching cookie consent rules.
The ePD uses the same tiered system for fines as the GDPR, so EUR 10 million or two percent of annual global turnover (whichever is greater) for first-time or less severe infractions, or EUR 20 million or four percent of annual global turnover (whichever is greater) for repeated or more serious infractions.
Additionally, individuals who suffer material or non-material damage as the result of a violation of the ePD have the right to compensation from the organization that committed the violation.
France’s CNIL has levied a number of large fines against large tech platforms — including Google, Facebook (Meta), Amazon, and Tiktok — for ePD violations, in some cases repeatedly over several years.
What is the future of EU privacy regulation and data protection?
The ePrivacy Directive is aging rapidly, as is the GDPR. When the ePD was last updated in 2009, the iPhone was only two years old and TikTok was years away.
The EU has since passed a number of laws to protect consumers and data privacy from various angles, but the challenge of creating regulations that remain valid for many years and also reflect rapidly changing business and technology landscapes remains constant.
Laws like the DSA and Digital Markets Act (DMA) also aim to protect personal data in part, and privacy is built into regulations that are peripherally related, like the AI Act. Decisions by the European Court of Justice also provide valuable information to guide enforcement.
With or without the ePrivacy Regulation, transparency and valid consent remain central to regulatory compliance (in the EU and around the world), building trusted and long-term customer relationships, and developing your Privacy-Led Marketing strategy.
Usercentrics CMP is automatically updated to help you stay compliant with evolving privacy regulations that are relevant to your business without requiring a lot of manual intervention. Notify your users, provide consent choices, and show your respect for customers’ privacy every day.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.
Marketers, designers, and developers need high quality data to deliver optimal online experiences and grow their businesses. A lot of that data comes from your audience and their activities on your website.
To collect that data in a way that respects data privacy laws and users’ privacy means that you need to be transparent and provide consent options. Laws like the GDPR and CCPA require you to inform people about what data you collect, how you use it, and what their rights are.
Different laws in different regions also require you to obtain user consent before collecting data, or provide granular options about what data uses that users can accept or decline, or enable them to opt out of various data uses.
Not to mention that there are an increasing number of business requirements for companies that rely on important platforms like Google’s to provide proof of consent if your company uses them for advertising, analytics, and other key marketing functions.
Smart consent management strategy with Webflow and Usercentrics enables you to meet data privacy requirements, build trust with your audience, and protect your marketing efforts and growing business.
Provide clear information and user-friendly consent options that match your brand and that are customized to where your users are located.
We look at why you need a Webflow cookie banner, how it benefits your data privacy compliance and marketing performance strategies, and how to set it up. Support customer-friendly Privacy-Led Marketing and Webflow cookie consent.
Why your Webflow website needs a cookie banner
Let’s look at why having a Webflow cookie consent banner on your website is so important for your business. Then we’ll cover the setup process.
No disruption to your Google services campaigns
Google Ads campaigns are popular among Webflow website owners for generating traffic, especially with retargeting. Government regulations aren’t the only requirements business owners need to navigate today. Large tech platforms that many businesses rely on are also implementing and enforcing privacy-centric policies.
Setting up Webflow cookie consent via Usercentrics CMP and displaying a user-friendly and privacy-compliant consent banner enables you to maintain access to Google services that your business relies on. This includes key features like Google Ads’ personalization and remarketing.
Usercentrics CMP is Gold Tier certified with Google’s CMP Partner Program, and comes with Google Consent Mode v2 built in. Start collecting and signalling compliant consent right from implementation.
Get the required consent information from your users, securely store it for regulatory requirements, and signal it via Consent Mode to Google Services. This controls the firing of tags for ads, analytics, and other services to comply with user consent requirements for users in the US, EU, and around the world.
With Google Tag Manager, it’s easy to get up and running with Usercentrics CMP on your Webflow website.
Embrace Privacy-Led Marketing
Marketing performance strategy and optimization is already a full-time job, but it grows more complex every day.
Marketers have to stay abreast of evolving privacy regulations, changes in tech platforms’ policies and functions, the expectations of customers and prospects, and more.
The risks of data breaches and other privacy violations go far beyond just fines and legal penalties.
They can irreparably damage your brand reputation and customers’ trust. They can require time- and resource-consuming remediation activities, like ongoing audits. And they can discourage potential new customers, partners, investors, and advertisers.
Your Webflow cookie consent banner can be a powerful tool, especially combined with a clear Webflow cookie policy, to enable you to achieve and automate privacy compliance, and maintain access to the business platforms you rely on.
Plus, you keep your customers happy that their privacy concerns are being addressed. Which means higher long-term engagement and more valuable data to boost your marketing efforts.
Steps to add a cookie banner to your Webflow website
We will walk you through the steps to ensure you have the accounts and access you need, and that your tags are set up to respond to consent signals correctly.
Set up your Google Tag Manager account
The easiest and most streamlined way to set up and control services on your Webflow website is by using Google Tag Manager to conditionally load scripts.
If you have a Google Tag Manager account already, you’re all set to get started. If not, create one for free.
Once your account is active, you can use it to set up Usercentrics CMP and to configure the tags that require user consent. Next we’ll cover the Usercentrics CMP setup and customization, then later we’ll get back to Webflow and how to add the CMP to your account.
You can refer to our Usercentrics CMP setup guide as well.
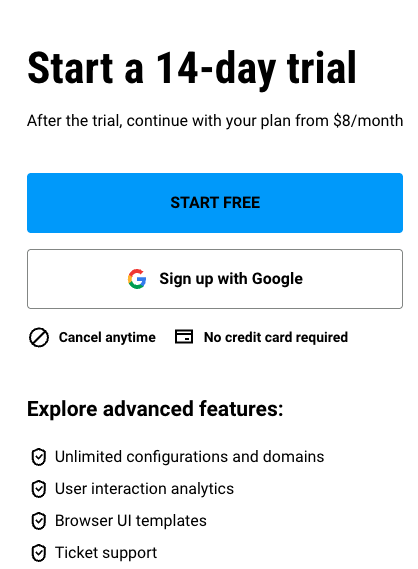
Sign up for your Usercentrics account
Go to the Free Trial page, then click the Usercentrics Web CMP tab. Click START FREE to get started with your 14-day free trial by providing the required information to set up your
Usercentrics account.
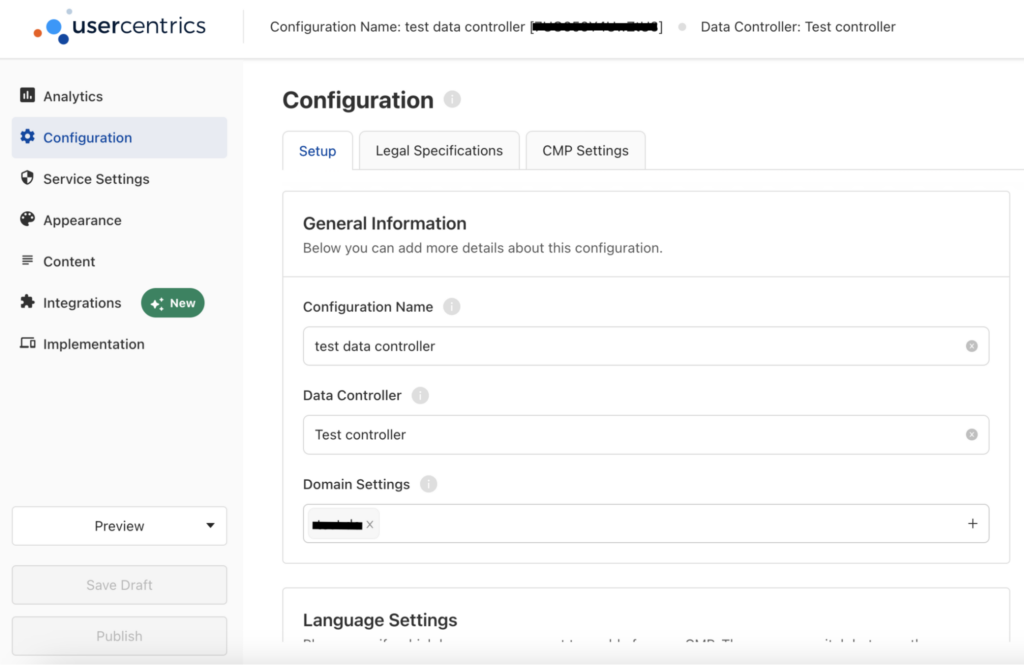
Configure your banner in the Usercentrics Admin Interface
Once your new account is set up (or you’re logged in if you already have an account), it’s time to set up your configuration. In the Admin Interface, click Configuration. This section is where you’ll add information about your domain (your Webflow site), where you’ll display the banner, your language preferences, and more.
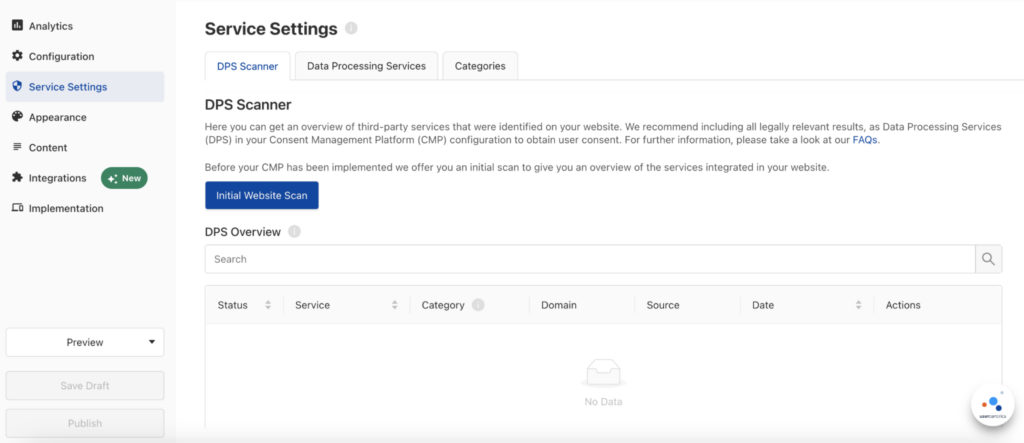
Initial website scan
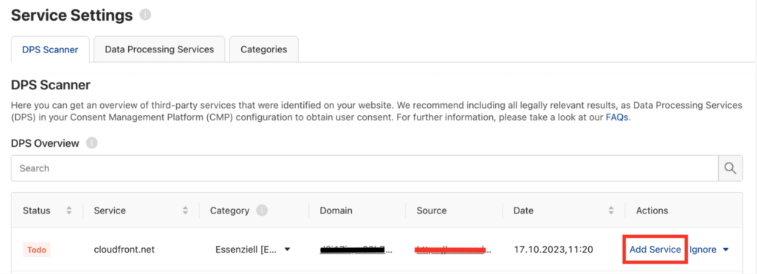
In the Admin Interface, click Service Settings, then click the Initial Website Scan button to start the first scan of your Webflow website. This will detect the cookies and trackers (Data Processing Services, or DPS) that are in use.
Once the scan is completed, it will generate your scan report, which you can see under the DPS Overview.
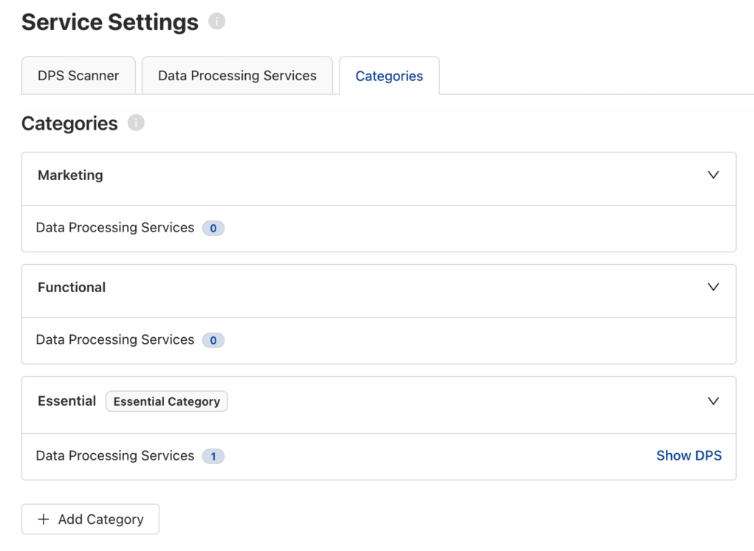
Categorize the Data Processing Services
Usercentrics CMP will automatically categorize the DPS for you that were detected in the initial scan. Essential, Functional, and Marketing are included by default. You can edit the classifications, or manually categorize anything that comes up as unclassified. You’ll do that under Service Categories, which includes predefined categories or enables you to define your own.
Add the Data Processing Services
Use the list of DPS from the initial scan report to add all the relevant cookies and other trackers in use on your website. Click Add Service to the right of each DPS listing in the Admin Interface.
This will add them to the CMP, enabling users to access and control their consent preferences by category. Your list of DPS can also be added to your Cookie Declaration.
Note: Scripts for the DPS may need to be adjusted to enable blocking until consent is obtained. Get more information in our guide.
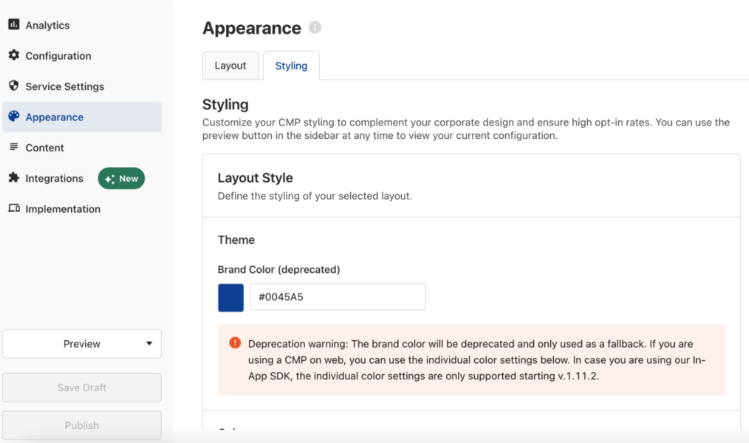
Customize the appearance of your consent banner
Click the Appearance tab to get started customizing how your consent banner will look. Under the Styling tab you can adjust the brand styling, fonts, logos, and more.
Under the Layout tab you can customize the settings for the banner’s first and section layer settings and the Privacy Trigger. That’s a shortcut that visitors can use to update their consent preferences on future visits to your website.
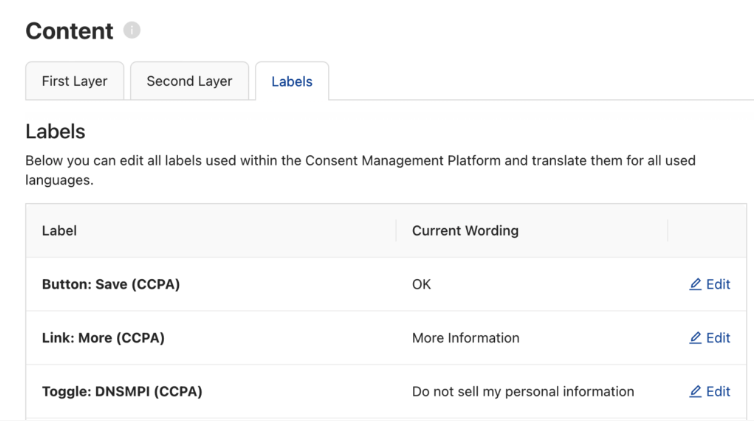
Click the Content tab to start customizing the text, links, and other elements that users will see and read on your consent banner. Usercentrics CMP supports 60 languages, and you can customize the banner here for relevant legal frameworks, like the “Do Not Sell Or Share My Personal Information” link required by the CCPA.
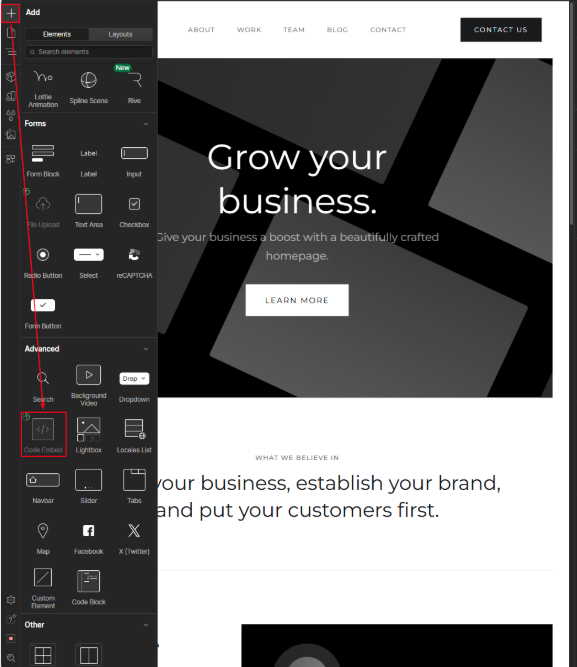
Implement the Usercentrics CMP on your Webflow website
Now you will add the Google Tag Manager snippet to your Webflow website. Please note that you will need a Basic, CMS, or Business Webflow account in order to be able to add scripts to your Webflow website.
Login to your Webflow account and ensure that you are in Design mode. You can select this at the top left of the menu. Click the + button to open up the menu of options you can add, then scroll down to the Advanced section. Click on Code Embed.
Add your Google Tag Manager snippet. You must replace “GTM-XXXXXX” in the last line with your own Google Tag Manager Container ID.
If you exclusively use Google Tag Manager to load third-party scripts, remember to configure them to require “additional consent” so cookies will be set without prior consent if that regulatory requirement is relevant to your business and website.
<!-- Google Tag Manager -->
<script>(function(w,d,s,l,i){w[l]=w[l]||[];w[l].push({'gtm.start':
new Date().getTime(),event:'gtm.js'});var f=d.getElementsByTagName(s)[0],j=d.createElement(s),dl=l!=’dataLayer’?’&l=’+l:”;j.async=true;j.src=
‘https://www.googletagmanager.com/gtm.js?id=’+i+dl;f.parentNode.insertBefore(j,f);
})(window,document,’script’,’dataLayer’,’GTM-XXXXXX’);</script>
<!– End Google Tag Manager –>
Monitor your cookie and tracker usage regularly
The Usercentrics CMP runs a daily website scan and automatically sends the report to your inbox when it’s complete. We recommend regularly checking your scan report to make sure all the cookies and other tracking technologies in use on your site are correctly classified and have a purpose description.
Marketing operations evolve quickly, so this is one way to stay ahead and make sure only the cookie categories that your users have consented to are activated. The scanner also automatically updates your Cookie Declaration to accurately reflect your Webflow website’s cookie usage.
Usercentrics CMP helps protect your business and grows with you
Usercentrics CMP makes it easy for you to meet regulatory requirements no matter where you do business. Keep your customers informed about your data processing and their privacy rights to build trust.
Also stay on top of the cookies and other tracking technologies that you’re using to collect data, so you can provide accurate information and valid consent options, and compliantly control your data collection and use. Build a Privacy-Led Marketing strategy that scales.
In just a few steps, you can set up a cookie banner on your Webflow website that looks great, is user-friendly, and helps protect your business. Check out our opt-in optimization whitepaper for more information about optimizing user experience and consent rates.
Show customers that you respect their privacy, get the high quality marketing data you need, and get automated peace of mind regarding your legal obligations.
Companies rely on data to create more personalized customer experiences, improve their products, and gather information about target audiences and their preferences. However, data protection laws, tech platforms’ policies, and guidelines are evolving around the world.
Consent management must be done thoughtfully to meet consumer expectations, legal requirements, and tech integration specifications. Otherwise, brands risk hefty fines, loss of data, and damage to their reputations and customers’ trust.
Still, compliant consent management is achievable. In this guide, we dive into everything you need to know about how to obtain, manage, and signal consent in a way that enables compliance with data privacy requirements and business specifications, and still delivers a great user experience. We also explain how a consent management platform can simplify this process.
What is consent management?
At its core, consent management is about providing ecommerce customers, website visitors, app users, and others with clear choices to agree to or decline the collection and use of their personal data on websites, apps, and other connected platforms.
It also requires documenting and securely storing the information once users agree to share it. For companies, customer consent management is a critical component of achieving data privacy compliance and maintaining customer trust.
What is the difference between consent and preference management?
While they might seem like similar concepts, consent management and preference management serve different purposes. Ideally, both concepts work together to enable great customer experience.
Consent management is primarily about obtaining legal permission to collect and use personal data, as required by privacy regulations, and, increasingly, by tech platforms’ policies. It involves users opting in or out of data collection and processing for specific purposes, an exercise of their rights under legal mandates and the requirements of platforms companies rely on for advertising, analytics, and more.
Preference management, on the other hand, enables users to customize their experience and communication preferences with a company. This might include choosing email frequency or communications topics of interest.
While consent management focuses on the legal aspects of data collection and usage, preference management is more about enhancing the user’s experience and personalization. It’s also a great source of zero-party data, which is highly sought by companies for marketing functions because it comes directly from the customer.
Typically, consent management is implemented through cookie banners and opt-in forms, whereas preference management is facilitated via preference centers or account settings. Both practices aim to give users more control over their interactions with a company, but they address different aspects of user engagement and data handling. The ultimate goal is holistic — to enhance marketing operations and provide better personalized experiences driven by both user consent and preferences.
Global consent management laws
Consent management laws are regulations that dictate how businesses must collect, handle, and manage the consent that individuals provide for access to their personal data. Depending on the laws in place where the business operates or their customers are located, requirements may affect all businesses, only those of a certain size, or those engaged in certain types of data handling.
General Data Protection Regulation (GDPR)
Probably the most influential consent management law of the “modern era” of data privacy was introduced in 2018 in the European Union. The General Data Protection Regulation requires companies to ask for permission before collecting or processing the personal information of EU residents if they monitor people or offer them goods or services.
Consent management, in the context of the GDPR, refers to the process of obtaining, recording, and managing user consent for the collection and use of personal data. Key aspects of GDPR consent management include:
- Explicit consent: Users must actively opt-in to data collection and processing
- Specificity: Consent must be specific to each purpose for which data is collected
- Informed consent: Users must be clearly informed about what data is being collected and how it will be used
- Freely given: Consent cannot be coerced or bundled with other terms
- Withdrawable: Users must be able to withdraw their consent as easily as they gave it
European Data Protection Board (EDPB)
The European Data Protection Board’s guidelines for consent, published in 2020, align with the GDPR consent requirements.
The European Data Protection Board is an independent European body that is responsible for ensuring consistent application of data protection rules across the European Union and European Economic Area (EEA), and promoting cooperation among EU Member States’ national data protection authorities.
The EDPB was established with the General Data Protection Regulation (GDPR) and issues guidelines, recommendations, and binding decisions to harmonize data protection enforcement, resolve disputes, and ensure that individuals’ rights to privacy and data security are upheld across the EU.
Data privacy regulations around the world
Since the GDPR’s enactment, consent management has become an integral part of data privacy compliance, and several other data privacy laws have been passed and implemented, including the following.
- The Digital Markets Act (DMA), which requires designated “gatekeeper” platforms to obtain explicit user consent before collecting or using personal data for certain purposes, such as online advertising or combining data from different services.
- Both the California Consumer Privacy Act (CCPA) its amendment, the California Privacy Rights Act (CPRA) in the United States require businesses to obtain explicit consent from consumers before collecting or using sensitive personal information. This can include precise geolocation data, racial or ethnic origin, or biometric information. Additionally, the CPRA mandates that businesses provide clear and conspicuous methods for consumers to opt out of the sale or sharing of their personal information. Methods may include placing a “Do Not Sell or Share My Personal Information” link on business websites.
- The Brazilian Lei Geral de Proteção de Dados / General Data Protection Law (LGPD) states that consent must be “free, informed and unambiguous.” In other words, it must be given voluntarily, after receiving clear information, and through a specific, unequivocal action. The law requires that consent be obtained for a specific purpose, that users can revoke consent at any time, and that special provisions are in place for obtaining consent for processing children’s data.
- Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) requires organizations to obtain meaningful consent from individuals before collecting, using, or disclosing their personal information. Consent is considered valid only if it is reasonable to expect that individuals understand the nature, purpose, and consequences of the personal data processing.
- China’s Personal Information Protection Law (PIPL) requires that consent for processing personal information must be voluntary, explicit, and informed. Individuals must have a clear understanding of the purpose, method, and scope of data processing. Additionally, the law mandates separate consent for processing sensitive personal information, sharing data with third parties, and transferring data overseas.
- Japan’s Act on the Protection of Personal Information (APPI) recognizes that consent is necessary for specific circumstances, such as when handling sensitive personal information or transferring data to third parties. However, it does not require consent for all personal data processing activities.
While each law is different, you may notice a common theme: each regulates consent management as part of its requirements.
How to collect consent: Two different consent models
There are two main types of consent that companies need to be aware of. Depending on relevant laws or policies, these determine how organizations obtain permission from individuals to use their personal data.
Opt-in consent
Also known as explicit or prior consent, opt-in consent requires users to actively give their permission before or at the time when any non-essential cookies are set or personal data is otherwise collected. This method typically involves clicking an “Accept” or “Allow” button. It is designed to comply with strict data protection regulations like the GDPR.
Opt-out consent
Also known as implied consent, opt-out consent operates on the assumption that the law allows cookies to be set or other data collection mechanisms to be used by default unless the user specifically takes steps to opt out. Typically, however, laws with this consent model require users to be able to easily opt out of data use for various purposes, like targeted advertising, at any time.
The opt-out consent model is generally not compliant with stricter data protection laws like the GDPR. The United States is currently the most known for using this model for its data privacy regulations, and employs it in state-level data privacy regulations to date.
Even in opt-out consent models, there are usually some forms of data that do require prior consent. Typically, these include sensitive data and data belonging to children.
What consent management involves at every stage of its lifecycle
Many organizations assume consent management begins and ends with cookie consent banners, but in reality it involves much more. Organizations must handle consent throughout its entire lifecycle — from when users first give consent to storing their choices, enabling users to withdraw or update their consent, and eventually deleting records when necessary.
Here are the key aspects of consent lifecycle management:
- Obtaining user consent: To start, organizations must clearly inform users about what data is being collected, how it will be used, and who will have access to it, among other information. Explicit consent must be freely given, specific, informed, and unambiguous. This also includes making consent easy to understand, offering granular choices (e.g. different permissions for analytics, marketing, or third-party data sharing), and ensuring users can make changes or revoke consent later.
- Recording consent: Organizations must keep detailed records of when and how consent was obtained, along with any changes to preferences over time. Maintaining records should include storing the exact consent text users agreed to, tracking timestamps, and logging any updates to consent.
- Managing consent: Users must have easy ways to review, modify, or withdraw consent at any time. This means providing simple tools for them to access their settings and update consent and preferences when there are changes to data processing activities or policies.
- Enforcing consent: Customer data must only be collected and processed according to the specific consent users have given. Organizations must prevent tracking that goes against user consent or legal requirements or cease tracking as soon as possible per legal requirements if a user revokes consent.
- Auditing and compliance: Maintaining a clear audit trail of consent activities and being able to supply the information is critical for demonstrating compliance with regulations like the GDPR and responding to data subject access requests (DSARs) (aka data subject requests).
- Updating and renewing consent: When data collection practices change, organizations may need to obtain updated consent from users. If an organization starts using data for a new purpose, changes or begins to work with new technologies or vendors or updates policies, they must notify users and give them the chance to accept or decline new terms.
- Consent expiration and deletion: Some regulations require consent to be refreshed or re-obtained periodically. Organizations must respect expiration dates when applicable and delete or anonymize data when consent is withdrawn or no longer valid or the purposes for data processing have been fulfilled.
What is a consent strategy?
A consent strategy is the approach an organization takes to obtain, manage, and apply user consent for data collection and processing. It determines how the organization requests consent, what choices they provide users, and how they balance compliance with data privacy laws, user experience, and data collection needs.
While consent strategy and consent management may seem similar, they serve different functions.
Consent management focuses on the operational aspects of handling consent, such as obtaining, storing, and updating consent throughout its lifecycle. It focuses on technical and legal details, such as logging consent records and providing opt-in or opt-out mechanisms.
In contrast, a consent strategy is the overarching approach that guides an organization’s decisions about how to handle consent. It aims to meet regulatory requirements while supporting business objectives and maintaining a positive user experience. This strategy influences various aspects of consent management, including:
- Determining whether to implement opt-in or opt-out consent models based on legal requirements and business needs
- Deciding how to present consent choices to users, including consent banner design, the wording of consent requests, and their placement on websites or apps
- Striking a balance between maximizing compliance and trust while still gathering valuable zero-party and first-party data for marketing and analytics
Types of consent strategies and their impact
Different consent strategies shape how businesses collect data, engage with users, and comply with regulations. Some prioritize strict adherence to privacy laws, while others focus on minimizing user friction. To balance these factors, many organizations adopt a hybrid approach. What strategy you choose will affect data collection, marketing performance, and user experience.
- High-control consent strategy: Prioritizes regulatory compliance and privacy rights with strict opt-in mechanisms and granular control. This strategy builds trust but may reduce data collection and marketing reach.
- Low-friction consent strategy: Minimizes disruptions with simplified consent requests, often using opt-out mechanisms where permitted. It supports data collection and marketing efforts but may risk noncompliance with strict regulations, potentially leading to fines and reputational damage. It may also adversely affect user trust.
- Hybrid: Adapts consent mechanisms based on regional laws and business needs. It balances compliance, data collection, and user experience. However, it does require careful implementation to avoid confusion for global users. Tactics that can be beneficial include contextual consent.
| User experience | Data collection | Marketing performance | |
|---|---|---|---|
| High-control | – Provides users with granular choices and transparency- May increase friction and bounce rates- Builds trust through respect for privacy | – Yields smaller but higher quality datasets- Enables purpose-specific data collection | – Higher engagement rates (so more data) for users who actively opt in- Improved email open rates and conversion rates |
| Low-friction | – Minimizes disruption to user journey and simplifies consent process for users- Users may feel less in control of their data, which can impact trust- Lack of transparency can reduce perceived privacy protection | - Gathers larger volumes of data- Higher risk of inaccurate or false information- Enables extensive data collection across multiple categories | – Larger addressable audience for marketing- Lower engagement rates due to less targeted data |
| Hybrid | – Tailored experience based on user location- Demonstrates compliance efforts to users | – Optimizes data collection within legal limits- Varied data quality and quantity by region- May add complexity to data management without a robust consent management platform (CMP) | – Balances reach and compliance across regions- Enables region-specific marketing strategies- Requires careful segmentation for campaigns |
Why is consent management important?
In many countries, consent management is a legal requirement, and failing to manage user consent preferences properly can lead to significant fines and legal challenges. Beyond regulatory obligations, it also affects business operations. Organizations that do not meet consent signaling requirements when doing business in regions like the EU that require it may lose access to advertising revenue from platforms like Google’s.
Giving users control over their personal data also leads to better business outcomes. It directly improves customer trust, marketing effectiveness, and operational efficiency.
Consumers are increasingly aware of how their data is used, and many make purchasing decisions based on privacy practices. A 2024 Cisco survey found that 75 percent of consumers will not buy from organizations they don’t trust with their data. Implementing a strong consent management process helps to build credibility with users by demonstrating a company’s commitment to privacy.
Explicit, opt-in consent enables businesses to respect customer preferences and increase the likelihood of being trusted with more data, enabling highly personalized marketing and a better user experience.
When consumers actively choose to share their data, the resulting information tends to be more accurate and valuable than data gathered via passive methods. This higher quality data reflects genuine interests and behaviors, and leads to better insights, more effective marketing strategies, and improved customer satisfaction.
Consumers who agree to receive marketing messages and choose their preferred formats and topics are more likely to engage and convert. Their consent signals direct interest in the brand, which naturally leads to stronger leads and improved conversion rates.
Targeting only consenting users who have expressed interest in specific products or services can also make marketing campaigns more cost-efficient. This approach means businesses can allocate their budgets more effectively, improve ROI, and optimize future campaigns based on clearer customer insights.
Perhaps most importantly, a consent-based approach also strengthens brand reputation. Consumers increasingly avoid companies they don’t trust. Providing customers with control over their personal data helps build loyalty and long-term relationships.
What is a consent management platform (CMP)?
A consent management platform (CMP) is a software solution designed to help organizations collect, manage, and store user consent in compliance with data protection regulations such as the EU’s GDPR, California’s CCPA/CPRA, and Brazil’s LGPD.
A CMP like Usercentrics CMP makes it easier to obtain legally compliant user consent through mechanisms like customized and branded cookie banners with multi-language support, and the use of A/B testing to increase your opt-in rates. This approach supports transparent consent collection while enabling users to easily modify or revoke their choices.
Comprehensive consent management solutions also track and record consent preferences, and provide a centralized repository that organizations can use to demonstrate compliance in the case of a regulatory audit. Or, if a user submits a data subject access request for a copy of their personal data, including their consent history.
By automating and streamlining consent management, CMPs not only help businesses adhere to legal requirements but also enhance user trust by giving individuals greater control over their personal data.
How does a consent management platform work?
A consent solution like Usercentrics CMP helps businesses manage the entire lifecycle of personal data while meeting consent requirements.
When a user visits a website, Usercentrics CMP displays a customizable consent banner or popup that informs visitors about data collection and provides consent options. The second layer of the banner is commonly where users can access more detailed information about the types of data being collected, how it will be used, third parties that may have access to it, and other required notifications.
Users can then manage their cookie consent by accepting or rejecting different categories of data collection and processing. For example, cookies for marketing, analytics, and other purposes.
Once a user gives consent, the Usercentrics CMP records and stores this information securely in a central repository. This enables proof of compliance in the case of a regulatory audit. Our platform also communicates these consent preferences to other systems and any third-party vendors involved in data processing, such as analytics tools or advertising partners.
For example, Usercentrics CMP integrates with the latest version of Google Consent Mode to signal user preferences to Google services. This enables organizations to align their consent collection processes with widely used platforms and tools.
Usercentrics CMP also enables up to date and ongoing user consent management. The scanner automatically detects and blocks cookies before user consent is obtained, and regularly scans your website to keep cookie lists up to date.
How CMPs automate compliance
CMPs automate compliance by handling key aspects of consent management, from regulatory adherence to integration with marketing and analytics tools. These are some important elements of effective automation.
- Regulatory compliance: Automatically scans for and detects cookies and trackers in use so notifications and consent options are accurate. Maintains audit logs and consent records, so businesses can demonstrate compliance with privacy laws like the GDPR, CCPA/CPRA, and LGPD if audited.
- Integration with existing tools: Automatically syncs consent signals across systems like Google Consent Mode, Meta Pixel, Google Tag Manager, CRM systems, email marketing platforms, and analytics tools.
- Tag and script management: Dynamically blocks cookies and tracking scripts until valid consent is obtained where legally required, supporting privacy compliance and protecting data integrity.
- Cross-platform functionality: Manages consent across websites, apps, and other connected platforms, providing users with a consistent and automated consent process.
- Analytics and reporting: Tracks consent trends, opt-in rates, and compliance status in real-time, helping businesses adjust their practices in line with user preferences.
CMPs automate the most labor-intensive compliance activities, helping businesses reduce errors, improve efficiency, and adapt to fast-changing privacy requirements.
How to choose the right CMP for your company?
Choosing the right CMP depends on your company’s specific needs, industry, and regulatory environment. Consider the following factors.
- Regulatory compliance support: Does the CMP align with privacy laws relevant to your business (e.g. GDPR, CCPA), stay up to date, and maintain auditable consent records?
- Integration compatibility: Can the CMP connect seamlessly with tools like Google Consent Mode, email marketing platforms, and CRM systems?
- Customization and scalability: Does the platform offer flexible branding, language localization, and support for multiple domains to match your user base?
- Ease of implementation: Does the CMP offer no-code deployment options for simpler setups and/or developer-friendly features for advanced customization?
- Analytics and insights: Does the CMP provide reports on interactions, opt-in rates, consent trends, and other metrics to refine your consent strategies?
- Pricing structure: Do the pricing model and plans align with your budget and operational scale?
Your company may only need to comply with one regulation for now. For instance, if you have a simple website and an audience or customer base located in a limited area (e.g. only in the region covered by the GDPR).
In that case, many CMPs can get the job done, and a number of them offer basic features for free. Still, be sure to check the CMP’s functionality against the requirements of relevant regulations, frameworks, or business stipulations, like the latest ones from Google.
Larger organizations will likely require more robust and scalable functionality, multi-regulation and language support, and full customization and branding options. An enterprise-grade consent management platform that offers advanced features, customization options, extensive integrations, and seamless scalability might be a better fit.
These enterprises likely need to achieve compliance with multiple regulations across many sites and platforms, and so have more complex needs than smaller organizations.
Usercentrics CMP and consent management
Usercentrics understands how important privacy is to both you and your customers, but also that you need data for marketing operations. That’s why our solution can help you organize and oversee the entire consent management lifecycle.
Usercentrics provides more than 2,200 legal templates to save time and resources and make it easier to set up the processes your company needs for compliance. Our platform also offers a Preference Manager that easily integrates into the Usercentrics CMP.
From obtaining compliant consent to staying up to date with in-use cookies and evolving regulations, Usercentrics simplifies and streamlines the consent management process.
It’s not just companies that consumers do business with online that collect and use personal data. Data brokers — also known as information brokers — access, aggregate, and sell huge amounts of personal data. This often happens without the knowledge or consent of the individuals the data belongs to, but is done legally.
Data is big business, too. The data brokerage market value is nearly USD 434 billion for 2025. We look at what data brokers do, how they obtain personal data and what they do with it, what laws they have to comply with, and what people can do if they don’t want data brokers to have their information.
What are data brokers?
Data brokers are companies that collect, analyze, aggregate, and sell consumer data. This data is collected from a variety of sources, including individuals’ online activities, social media platforms, forms and surveys, financial transaction records, and public records.
These companies often perform various kinds of aggregation, augmentation, analysis, and repackaging of data. The result can be valuable consumer profiles and packages of data that are sold to other organizations ranging from ad networks to law enforcement.
Who do data brokers sell data to?
Depending on the types of data and how it’s analyzed and processed, a wide variety of organizations and industries purchase the data that brokers sell, including:
- Marketers and advertisers: e.g. using purchasing history, online behaviors, and demographic details for highly targeted ad campaigns
- Employers and recruiters: e.g. using employment history, financial records like credit scores, and social media activity to perform background checks and help enable hiring decisions
- Fraud prevention and cybersecurity companies: e.g. using email and phone usage, IP addresses, and device “fingerprints” (unique IDs) to investigate and identify fraud or authenticate user identities
- Health and pharmaceutical companies: e.g. using health-related search or purchasing history and fitness tracker data to perform research and market healthcare products
- Financial institutions: e.g. using spending habits, loan histories, credit health indicators, and income estimates to assess credit risks and target financial products like mortgages
- Insurance companies: e.g. using medical history, lifestyle choices, vehicle ownership and driving records, and property records to assess risks and determining insurance policy pricing
- Retail and real estate companies: e.g. using household income, purchasing history, real estate search history, and property ownership history to identify potential home buyers and target advertising
- Government agencies and law enforcement: e.g. using purchasing behavior, social media activity, geolocation and mobile tracking, and public records for surveillance, investigations, and public safety initiatives
- Politicians and campaign staff: e.g. using online search histories, social media interests, political affiliation, and voter registration records to target potential voters with personalized political messages and ads
How do data brokers get your information?
Data brokers can collect information from public sources, like property ownership, business registration, or voter registration information. They can also obtain information from a wide variety of online sources and individuals’ activities.
Information that data brokers obtain from users’ online activities
Data brokers collect a lot of digital personal data, especially from everyday user activities. For example, via cookies and other tracking technologies they can collect data on people’s search and browsing histories, time spent on sites and pages, and ecommerce activities like purchases or abandoned carts.
Activities people voluntarily participate in online, often for some incentive, are also a great source of data. For example, contests and giveaways, surveys and quizzes, and reviews or feedback forms for products and services can all deliver detailed identifying information, demographic data, and insights on preferences and habits.
Information that data brokers obtain from mobile apps use
From apps brokers can track location from GPS, purchases, and habitual activities. From connected devices (Internet of Things) ranging from fitness trackers to computerized systems in cars, there’s a wealth of information about activities, preferences, locations, and more.
Information that data brokers obtain from financial transactions
Financial transactions are protected by a number of regulations, but data brokers still have access to a wide variety of data sources. These include purchase histories from retailers and loyalty card programs, credit card use trends (like how often people buy online), anonymized and aggregated data about consumer spending habits, and information about subscription services (e.g. streaming media services or meal plans).
Information that data brokers obtain from healthcare activities
Health information is also heavily regulated, but data brokers can still legally access information about health-related search queries, revealing health interests, concerns, or diagnoses. They obtain data about health status from fitness trackers and other monitors, and they can obtain health-related purchasing information, like about medications, supplements, or assistive devices.
Information that data brokers obtain from third parties
Data brokers don’t always collect or process personal data themselves. Often they purchase data collected by others from their customers. These entities include:
- Ecommerce platforms
- Streaming media services
- Marketing agencies
- Apps publishers (e.g. health, fitness, gaming)
In some cases this data is anonymized before sale, but it can still provide valuable information about demographics, volumes or frequencies of purchasing or use, etc. In some cases, however, data brokers can cross-reference data and be able to re-identify individuals.
Information that data brokers obtain from data breaches
In addition to all the more publicly available sources, plenty of information can be obtained on the dark web, which is where vast amounts of data from data breaches tends to end up. These data sets can include specific types of data, like names, email addresses, or credit card numbers, up to extensive customer profiles with a lot of sensitive personal information.
Given the frequency of data breaches, it can be possible to obtain and match data from multiple breaches to create rich profiles of breach victims’ personal information, which can be used for fraudulent activities or re-sold.
Do data brokers have to get consent?
In many cases, no, particularly in the United States, data brokers do not need explicit or informed consent from the individuals’ whose data they collect and use. This is in part because publicly available data does not typically require prior consent.
Additionally, some data is exempt because it has been anonymized, and some companies include data sharing clauses in their terms of service, which users have to agree with to access a service, make a purchase, etc., but often do not read in detail.
It also depends on the jurisdiction. For example, in the European Union, explicit and informed consent is required from individuals before their data is collected, per the General Data Protection Regulation (GDPR) and other laws.
However, in the United States, for the states that have privacy laws to date, in most cases personal data can be collected and used without needing to obtain prior consent, unless the data subject is a child. The main legal requirement is that data subjects be informed about data processing and their rights.
Types of data for which data brokers would likely need to obtain consent under various laws include the following:
- Financial and/or credit data (US: Fair Credit Reporting Act)
- Health and medical data (US: Health Insurance Portability and Accountability Act)
- Children’s data (US: Children’s Online Privacy Protection Act)
- Personal data protected under regional privacy laws (US: CCPA/CPRA and others, EU: GDPR and others)
There can be loopholes in regulatory requirements as well. For example, websites and apps that track health and fitness data are not subject to HIPAA, and social media platforms may not verify that users are over the age of 13, so may collect and sell children’s data without legally required parental consent.
How do data brokers make money?
Data brokers make their money from selling the data they collect, or insights that can be gleaned from analyzing the data. Often they sell to other types of companies or organizations, but sometimes they sell data to other data brokers.
Data can be sold in several different ways. The most straightforward is bulk sales of data to advertisers, marketers, and other companies. The more timely, well organized, and detailed the data is, the more data brokers can charge for it.
Data brokers can also maintain continually updated databases, and sell access to the data they contain on a subscription basis. These subscriptions are particularly valuable to marketers for targeting advertising, for financial institutions to do risk assessments, or for companies that need live or near-live geolocation data.
Data brokers can also make data more valuable by combining data from multiple sources and analyzing and segmenting it.
Combining individuals’ preferences and activities, purchase histories, and other sources, data brokers can create detailed profiles and groups, like people who regularly enjoy luxury travel, or people of a certain age and education level who are likely to vote for a specific political party.
Data brokers can also make well-educated predictions from data and spot burgeoning trends, selling that information rather than the data that produced them. This can also be highly valuable for brands and marketers.
Brokers’ databases are also used in paid partnerships, like with ad networks and social media platforms, via direct platform integrations. Data brokers provide detailed consumer profiles via the databases, and advertisers pay for access to this information.
The more targeted the information, the more they pay, and the broker makes a fee or commission from the ad network. This information is then used to show highly targeted ads to platform users.
Beyond the business world, data brokers can also sell data to government agencies and law enforcement. This can include location data, biometrics like facial recognition data, social media activity, and other personal information these entities can gain access to through private contractual agreements.
Organizations that require high levels of security can also purchase tools from data brokers, which are powered by personal data. For example, banks, cybersecurity companies, and retailers may be interested in tools to improve identity verification and fraud detection to cut down on credit card fraud, and banks can use them to authenticate loan applicants.
Why are data brokers legal?
Data brokers’ operations are legal for a number of reasons. The most direct one is that some data they collect and use is publicly available to anyone, so the average person could collect and analyze it the same way data brokers do.
Another reason is that there are loopholes in some privacy laws and other relevant regulations, which enable data brokers to access and process various kinds of personal data.
Some laws intended to protect data and individuals’ privacy are also aging rapidly and may no longer adequately protect privacy rights and personal data in a world where technology continues to evolve rapidly. Legislation rarely proceeds as fast as the tech industry, and in the US, specifically, there is a patchwork of federal and state-level regulation.
In some cases, individuals do provide consent for collection and use of their data. They just may not know it if they don’t make a habit of reading Terms of Service and other relevant documents. Or they may have consent fatigue and just click “Accept” without reading further because they want to access a website, complete a purchase, or other function.
Also, as we noted at the beginning of the article, it’s a highly lucrative industry and the data is extremely valuable to a lot of entities. Some companies — in addition to the data brokers themselves — make a lot of money from the flow of personal data (the volume of which is always increasing).
This means many companies, agencies, etc. have strong incentives to lobby for continued access to data from as many sources and for as many uses as possible.
What data privacy laws regulate data brokers?
There aren’t many laws that explicitly regulate data brokers, but their activities are included in a variety of laws with varying jurisdictions and covering various industries. Some of these include the following.
Federal US laws regulating data brokers
The United States doesn’t have any federal laws explicitly regulating data brokerage. However, it is covered under operational requirements of certain industries, specific audiences whose data brokers may collect and use, and other factors. These are the most important US federal laws regulating data brokers:
- Fair Credit Reporting Act (FCRA)
- Federal Trade Commission (FTC) Act
- Health Insurance Portability and Accountability Act (HIPAA)
- Children’s Online Privacy and Protection Act (COPPA)
State-level US laws regulating data brokers
To date, only some states have data privacy laws passed or enacted, and the US does not have a federal privacy law. Data brokerage is covered under some state-level data privacy laws, but a few states also have laws that more directly target these businesses.
- California Consumer Privacy Act (CCPA) / California Privacy Rights Act (CPRA)
- Data Broker Registration Statute (California)
- Virginia Consumer Data Protection Act (VCDPA)
- Colorado Privacy Act (CPA)
- Connecticut Data Privacy Act (CTDPA)
- Nevada Privacy of Information Collected on the Internet from Consumers Act (NPICICA) and Amendment SB-260
- Vermont Data Broker Law
International laws regulating data brokerage
Some international data privacy laws are more stringent than US laws, and cover any entity collecting or processing personal data to offer goods and services or to monitor individuals. As a result, data brokers are covered under these broader regulations.
- European Union
- Canada
- Australia
- Brazil
- India
- Japan
How do you remove data from data brokers?
Data brokers collect personal information from such a wide variety of sources, and many consumers are not even aware that it’s happening. As a result, it may seem daunting to try and get your data removed from their databases. But there are several ways to go about it.
You can approach the data removal process manually, and personally request removal of your data from individual data brokers. It’s free to do so, but requires completing forms, verifying your identity, and sending emails, so will cost you in time spent.
There are paid data removal services that will do the legwork for you. Some focus on specific types of sites and services; others tout their ability to remove data from dozens of brokers. These are typically subscription services that regularly monitor and have your data removed.
Beyond the brokers themselves, personal information can appear in search engine results. Companies like Google do provide tools to request removal of your data.
Under the GDPR, European residents have the “right to be forgotten”, though that isn’t necessarily the case elsewhere.
However, individuals can request removal of personal information that appears online, like phone numbers or addresses, whether on websites or search results, for example if doxxing has occurred (the publishing of private and/or identifying information about an individual online, typically with malicious intent).
This requires contacting the search engine company or website owner to request data removal, and may not be a fast process. (Privacy laws that provide deletion rights do typically include a time frame within which requests must be acted upon.)
How to prevent data brokers from accessing your data?
Data brokers can’t sell your data if they don’t have it, and there are a few ways to prevent or limit the personal data you create online.
Adjust privacy settings in web browsers and on social media accounts. Remove or limit the tracking they perform on your activities. Use search engines that center privacy and use less or no tracking. On mobile phones, disable app tracking for iOS or Android, and decline when new apps ask if they can initiate tracking.
As the old saying goes, “if something is free, you are the product”. So expect that free apps or services will be tracking and collecting your data and very likely monetizing it. This can include everything from fitness trackers to VPNs to weather apps.
There are privacy-focused apps and services for just about all functions we perform online, from instant messaging to email to browsing. You may want to make the switch.
When you do need to provide personal data, e.g. when signing up for services, you can use specific and generic credentials. For example, create email accounts, potentially from a temporary email service, that’s separate from your main account. Use that to complete an ecommerce purchase as a “guest” or to sign up for newsletters.
Depending on where you live, you may also have access to free phone numbers so you don’t have to provide your real one. You can use one of those when it’s for a purpose where you won’t actually need to be contacted by phone.
How Usercentrics helps you protect your personal data and privacy
For individuals, it’s important not to ignore consent banners on websites. Depending on where you live, you may see them a lot, but taking a moment to interact with them and read important information means you can then make informed decisions and can decline consent for many kinds of tracking.
Or, if you live in a jurisdiction like a US state where prior consent is not required but there is a privacy law in place, you likely have access to a mechanism on websites where you can opt out of specific uses of your personal data, like for targeted advertising.
For companies, respect your customers and relevant laws regarding access to and sale of personal data. Building trusted relationships with your audience is the best way to obtain high quality data for marketing and other business-critical purposes. Use a consent management platform for transparency and to enable granular consent decisions.
Usercentrics enables companies to create user-friendly consent banners for websites, apps, and other connected platforms that match company branding and provide legally required information and consent options to users. Achieve and maintain privacy compliance with regulations around the world, and build trust with users.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.
Increasing regulation, consumer demand, and the influence of big tech companies have all required mobile developers and web publishers to prioritize and adopt data privacy compliance and consent management practices. The real driver, however, is your company’s bottom line.
The rise of data protection laws and the requirements they set out mean that consumers are increasingly aware that if they’re not paying to use a product, their data is the real price.
As they’ve become more informed about how their data is collected and used by developers and publishers, consumers are more inclined to walk away from businesses with data privacy practices they don’t trust, understand, or agree with.
The mobile app, game, and web publishing industries have already had to adjust to how they manage consumers’ data privacy expectations over the past few years while also figuring out compliance requirements for new data privacy regulations. There’s no sign that this will change any time soon. Let’s take a look at the challenges developers and publishers are currently facing.
What is data privacy?
Data privacy involves the processes around the collection and use of digital personal information, including data that can be used to identify an individual, and the need to do so responsibly.
For companies, it relates to the policies and processes that enable users to control how their information is collected, used, processed, and shared in line with relevant data privacy laws. It also creates a framework for how companies can access and use personal data, including sharing and transfers to third parties or other countries.
Data privacy for app, game, and web publishers
App, game, and web publishers have to comply with major data privacy regulations like the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) the same as other companies that process personal data do.
The nature of the data collected from mobile app users can be sensitive in nature, including health or financial information. This means app, game, and web publishers must ensure high levels of security and transparency around their data collection and usage practices. When personal data is categorized as sensitive by privacy regulations, extra restrictions on usage and security requirements are levied on entities accessing it.
Biggest challenges for managing sensitive data
Data management presents a variety of complexities for developers and publishers that have to balance user experience, technical performance, data privacy requirements, and monetization demands.
1. Privacy-first mobile app marketing strategies make consent critical
Obtaining user consent for collecting personal data in apps and games has evolved from a mere formality to a central pillar of development and marketing operations.
This is a result of increasing global awareness about the control and protection of data, as well as the growing coverage of protections from privacy regulations. On top of this, pressure from business sources like premium advertisers and platforms like Google is increasing. These players now insist on proof of consent to enable access to high value inventory or their tools, making consent a direct driver of monetization and ongoing revenue.
Privacy by design is especially important in the mobile context, as UI restrictions and user impatience require a seamless consent process to ensure a positive experience. This approach will not only help you to attract and grow a dedicated audience to drive revenue generation, but also help you to avoid regulatory violations while meeting critical partner requirements.
The Digital Markets Act, Google Consent Mode, and consent signaling requirements
The Digital Markets Act (DMA) also brings major changes to European digital markets. It places new data privacy responsibilities on seven designated gatekeeper companies — Alphabet, Amazon, Apple, Booking.com, ByteDance, Meta, and Microsoft — which have billions of mobile users among them.
To achieve DMA compliance, these companies must ensure that third-party advertisers and developers using their platforms also get valid user consent and signal it to the gatekeepers. Google’s updated EU user consent policy and Google Consent Mode v2 are great examples of this.
Consent Mode introduces various consent signaling parameters that control whether user data can be processed via Google tags and used for advertising or personalization. This requires using a Google-certified consent management platform (CMP) into which Consent Mode v2 is integrated. Consent information is collected from users via the CMP, and communicated to Google services via Consent Mode.
Learn more: Usercentrics CMP supports Google Consent Mode V2
The TCF 2.2, Google, and publishers
The IAB’s latest version of the Transparency and Consent Framework, the TCF v2.2, launched in May 2023 and brought a number of changes to mobile advertising.
The update excludes “legitimate interest” as a legal basis for data processing. This means it’s now mandatory for app publishers to capture consent for both cookie use and mobile identifiers in order to deliver personalized and non-personalized ads.
Google now also requires publishers using its products — including Google AdSense, Ad Manager, or AdMob — to use a Google-certified CMP that integrates with TCF v2.2 when serving ads to users in the EU, EEA, UK, and Switzerland.
2. Cross-device and cross-platform tracking for compliance and user experience
Users want seamless, personalized online experiences while also maintaining total control over the data they share and what companies are allowed to do with that data.
One of the biggest challenges here is that it’s increasingly common for users to have multiple devices, engage with apps across all of them, and want these platforms to “talk” to one another so that they don’t have to provide their information or consent multiple times. This also has to be handled securely.
Managing data privacy and consent across devices becomes more complex as more platforms are introduced. Especially since operating systems can change and considering that all of our apps come from different publishers with different technical capabilities and different levels of dedication to data privacy.
App publishers often need to develop sophisticated mechanisms to track users across devices and recognize their consent preferences on all platforms, all while respecting user privacy and the requirements of one or more data privacy regulations.
Under many privacy laws, apps also need to enable users to change or withdraw previously given consent at any point, which must immediately be respected across devices and apps, including by third parties processing data for publishers.
3. Artificial intelligence introduces another layer of complexity
Artificial intelligence (AI) is becoming integral to mobile apps, and the resulting increase in automated decision-making and targeted profiling is raising privacy concerns.
As a result, some data privacy laws require explicit user consent or clear opt-out options around automated decision-making and disallow it to be used on children’s or sensitive personal data.
The EU AI Act, which came into force in June 2024, is an example of this type of regulation. It introduces comprehensive rules for AI usage in the EU and applies to the providers and developers of AI systems that are marketed in the region. It aims to safeguard consumers while still encouraging innovation.
The AI Act categorizes different uses and risk levels posed by AI and prohibits AI practices that pose unacceptable risks — like manipulative techniques or exploiting vulnerable groups — and requires that high-risk applications be registered, documented, and submitted for regular compliance checks.
As a result of the AI Act and other data privacy regulations, publishers must ensure that their EU-based users are fully informed and have control over AI-driven processes in their applications.
This includes communicating transparently with users to inform them whether AI tools or algorithms are being used, what the purposes are, what data they use, the decisions that they might drive, and who might have access to the resulting information.
Publishers must also give users the option to opt out of all AI decision-making, especially when privacy regulations require an opt-in model for the use of AI tools.
4. Tighter controls over third-party data sharing
Historically, publishers could collect extensive user information and engage in data selling without obtaining consent from data subjects. Users typically weren’t aware of who had access to the information that was collected or how it was used.
Even now, although users see notices that request consent to share their information with “trusted partners,” it’s often unclear who these partners are and how they might use the information in question.
For example, some companies have hundreds of third-party partners and additional parties are sometimes nested in services like marketing cookies. As a result, they can only be uncovered by deep scanning, which makes them virtually invisible to the average user.
To comply with regulations like the GDPR and CCPA, publishers must now ensure that they have the necessary data processing agreements (DPAs) in place with any third parties that will be able to access the data collected by publishers.
Under most data privacy laws, the controller — the company arranging for the data processing — is responsible for the actions of third-party processors, hence the importance of DPAs to provide a framework for how processing and data protection must be conducted.
As privacy regulations tighten up globally, app and game developers and web publishers will need to become far more careful and strategic about managing consent, but also about which third parties, including advertisers, have access to their users’ data. In the EU and US, authorities have explicitly called out apps as a market that would be experiencing an increase in regulatory scrutiny.
The difficulty for publishers and developers is that these detailed consent requests may deter users from agreeing to tracking, especially if they have to scroll through a long list of companies they’ve never heard of but will then have access to their data.
One solution is to put more rigorous vetting practices in place for third-party partners and advertisers. This might include evaluating their compliance with various regulations and ensuring that their consent policies and mechanisms are detailed enough to meet the “informed” requirement of many laws’ conditions for valid consent.
5. Mobile app privacy compliance goes global
Gartner has predicted that 75% of the world’s population will have data privacy protections by the end of 2024. Data privacy is no longer a niche crusade by a few organizations or governments. Some regions, like in the EU, have multiple laws to protect consumers and their right to privacy.
Data privacy laws usually protect residents of the region where they’re enacted and are extraterritorial. For example, the GDPR puts requirements in place for the handling of EU residents’ data for all businesses, regardless of whether the business is based in the region.
This global reach has enormous potential implications for mobile apps and games. Users can be located anywhere, so developers may need to comply with multiple regulations to stay on the right side of the law.
While tools like geolocation can help developers to display the correct information and consent options to users based on their location, it’s still potentially a piecemeal approach. Robust and flexible data privacy frameworks that can be adapted to regional, national, or industry-specific laws and policies therefore become essential.
These frameworks enable publishers to focus on their core business while being able to adapt their data privacy and consent operations as laws change. This is especially crucial for smaller businesses, which may lack the significant targeted technical or legal expertise required for constantly maintaining data privacy compliance.
Read about in-game consent now
6. User tracking and profiling for personalization
Publishers and developers that want to personalize in-app, in-game, and web experiences will need to leverage user tracking and profiling. This involves collecting data directly from your users, including online behaviors and preferences, to ensure the content they see is tailored to their interests.
However, major data privacy laws significantly impact how you’re able to do this while still respecting user privacy. Here, techniques like behavioral fingerprinting and progressive profiling can help you identify browsing patterns and collect data incrementally to gain valuable insights while adhering to these regulations.
Read about Google additional consent now
7. Adhering to the Children’s Online Privacy Protection Act (COPPA)
Children are an especially vulnerable population, making their data more sensitive and requiring it to have greater protection than the average app, game, or website user. Pretty much all data privacy laws categorize children’s data as sensitive by default and require prior consent from a parent or guardian before it can be collected.
The age range that defines a child varies by law, so under some laws consent must be obtained by the young person rather than a parent or guardian.
This adds a layer of complexity for developers and publishers, who must obtain verifiable parental consent under the US federal law COPPA when collecting personal information from children under the age of 13.
Some recent enforcement actions highlight the importance of compliance with the Act:
- Microsoft: In June 2023, Microsoft was fined USD 20 million for collecting personal information — including names, email addresses, and phone numbers — from children who signed up for Xbox accounts without parental consent.
- ByteDance: The company behind TikTok has been subjected to multiple investigations for collecting biometric data from users without verifiable parental consent.
- Snap Inc: Snapchat has been scrutinized for its data collection practices related to children. The Federal Trade Commission (FTC) in the US investigated the platform for failing to inform parents about the data it collected from children under 13.
- Meta: The FTC has conducted several investigations into Facebook and Instagram for collecting personal information from children without parental consent after allowing children under the age of 13 to create accounts on the platforms.
Read about mobile app CMP now
Biggest data privacy issues to watch out for
Developers and publishers working in the mobile space face some critical data privacy challenges. However, with the right knowledge and tools, you can gather and use data in a way that increases trust with consumers and positively impacts your bottom line.
Privacy-led marketing strategies also enable obtaining high quality data directly from users, helping to ensure consent and build more desired and personalized experiences that boost engagement and revenue long-term.
Staying compliant with privacy laws
Failure to stay up to date with data protection laws’ requirements and security best practices can lead to data breaches and leaks, which can result in lawsuits, hefty financial penalties, and significant damage to brand reputation.
In addition to these direct costs, it’s likely that your company will incur indirect costs such as a decreased revenue due to loss of customer trust and potential business opportunities.
Here are some of the global data privacy laws that app, game, and website developers and publishers should keep an eye on and maintain compliance with:
- General Data Protection Regulation (GDPR): Requires companies that collect and handle the data of EU residents to obtain users’ explicit, informed consent before any data collection takes place.
- ePrivacy Directive (ePD): Complements the GDPR and regulates the use of cookies and tracking technologies as well as the confidentiality of electronic communications.
- California Privacy Rights Act (CPRA): Expanding and amending the CCPA, this protects the personal data of California residents by requiring companies to disclose data collection practices, and provide opt-out opportunities, including a “Do Not Sell Or Share My Personal Information” link.
- Personal Information Protection and Electronic Documents Act (PIPEDA): Governs how private companies can collect, use, and disclose Canadian residents’ personal information.
- Washington My Health My Data Act: Protects highly sensitive health data, making it critical for apps that collect health, fitness, and wellness information.
- Protection of Personal Information Act (POPIA): Regulates the processing of personal information by public and private bodies in South Africa.
- Lei Geral de Proteção de Dados (LGPD) : Safeguards the personal information of Brazilian residents by regulating how it may be collected and processed.
Keeping track of changes to these and other data privacy laws can be difficult and expensive for teams that don’t have the in-house legal and technical expertise required to achieve and maintain compliance.
Using a CMP like Usercentrics CMP can help developers and publishers achieve and maintain privacy compliance by providing tools to manage user consent in a way that aligns with the latest requirements as they come into effect. Displaying a consent banner also demonstrates respect for users’ data privacy to build trust.
Visibility over collection, usage, and sharing of data
Developers and publishers that want to achieve and maintain compliance with data privacy laws need to create visibility around how an app, game, or web platform collects, uses, and shares data.
This can be done by providing users with detailed information about your data collection and data handling practices, which should be communicated via consent notices within your application or game, or on your website.
Access control to personal data
Proper access controls are necessary to protect both employee and consumer data within apps, games, and web platforms.
To adhere to the GDPR and other data privacy laws, companies must implement controls to limit access to authorized personnel only. This includes using role-based access controls and multi-factor authentication, as well as conducting regular access reviews to maintain data security. Such monitoring and technical controls also need to include third parties that may access the data.
Securing data across multiple devices
The rise of remote work has presented some challenges for securing data. Employees now often access company platforms from various devices, increasing the risk of data breaches.
To reduce the risk of leaks and ensure that data subjects’ personal information is safeguarded across all access points, developers and publishers must implement additional security measures, like end-point security solutions and robust monitoring.
Best practices for data privacy in apps, games and web publishers
There are a few key best practices that developers and publishers should follow to ensure that their personal data collection and access practices meet the requirements of data privacy laws.
- Data minimization: Collect only the data that’s necessary for your operations and ensure it’s used for specified and legitimate purposes.
- User consent management: Use a CMP to handle user consent efficiently and reliably with automated functionality to remain compliant with evolving privacy laws.
- Third-party management: Ensure that third-party vendors comply with your internal data privacy policies and external regulations.
- Data encryption: Encrypt data to protect it from unauthorized access and breaches.
- Security audits: Conduct regular audits to identify and remedy vulnerabilities with your app, game, or web platform.
- Regular software updates: Keep all software up to date with the latest security patches to protect it against new threats.
- Data breach response plan: Develop and maintain a data breach response plan to enable speedy and effective response to data leaks.
Key to data privacy for apps, games, and web publishers
Data privacy regulations, user expectations, and business requirements have made user consent a necessity.
Savvy publishers understand that embracing data privacy and consent management can in turn drive acquisition of quality user data, downloads, long-term customer loyalty, monetization strategies, and revenue growth.
Developers and publishers that adopt a privacy-first approach when building their apps, games, and web platforms are protecting their operations from fines and other penalties, now and in the future.
What’s more, they understand that this approach can help them streamline operations so they can easily adapt to frequent changes in the technical and legal landscape and continue to generate revenue through advertising, subscriptions, and in-app purchases.
To take a privacy-first approach to collecting and managing user data, turn to Usercentrics CMP. It’s a flexible and scalable platform that helps you manage user consent across websites, apps, and mobile games so you can achieve and maintain data privacy compliance.
Your consent banner is one of the first interactions users have with your website. A well-designed consent experience can enhance trust, improve engagement, and align with evolving privacy regulations. By optimizing how and when users provide consent, you create a transparent, user-friendly experience that supports both compliance and customer relationships.
Make every interaction count
A poorly designed or intrusive consent banner can frustrate users and drive them away, negatively impacting engagement and conversions. In contrast, a clear and intuitive banner helps users understand their choices, and ultimately build confidence in your brand.
Download the checklist today to refine your consent strategy, improve user experience, and better align with global privacy standards.
The growing popularity of blockchain technology is transforming how we approach data privacy and consent management.
Blockchain consent management provides a secure and transparent solution that empowers users to control their personal data. By leveraging the properties of blockchain technology, it provides an accountable and efficient way to handle permissions to access personal data.
This shift represents not just an upgrade in technology from previous consent management options, but a fundamental change in how we think about data privacy and control.
What is blockchain consent management?
Blockchain consent management provides a way to handle user data permissions securely and transparently. It’s a digital system that gives users control over how their personal information is used online. It acts like a customizable, trackable permission slip, enabling individuals to decide exactly what data to share, with whom, and for what purpose.
Unlike traditional agreements that rely on more broad, potentially vague consent, this system offers more precision.
Every consent action, like granting or withdrawing permission, is securely recorded on a blockchain ledger. A blockchain ledger is like a shared digital spreadsheet that exists simultaneously on many computers.
Everyone has the same updated information, and no single person can change it without everyone else knowing.
This means that the records are tamper-proof and easy to track. Companies can only access data if the user explicitly allows it. This helps organizations meet the requirements of privacy regulations, like the General Data Protection Regulation (GDPR), while giving users greater control.
Furthermore, the blockchain’s distributed ledger supports transparency and accountability, while smart contracts — known as self-executing digital agreements — automatically enforce consent rules. These “if/then” rules trigger actions only when specific conditions are met.
For example, a smart contract could automatically block a marketing company from using your personal data if you withdraw consent, instantly removing their access rights. When you update your preferences, the contract immediately enforces your wishes, preventing unauthorized data usage without requiring manual intervention.
This system reduces human error and simplifies compliance by helping to ensure data access happens only when the user’s requirements are fulfilled.
Blockchain consent management versus traditional consent management systems
Traditional consent management systems are like filing cabinets where a company stores user permissions. You, as a user, typically agree to terms by clicking “I accept,” and the company keeps track of your consent in its own database. These systems are straightforward but have limitations in both transparency and user control.
Blockchain consent management is more advanced. Imagine a shared, digital ledger where every consent decision is recorded in a way that everyone can see, and that can’t be easily changed except by the relevant party making the consent decisions.
This gives individuals more visibility into how their data is being used, and prevents companies from secretly modifying or ignoring users’ permissions.
The key differences lie in control and transparency. Traditional consent systems rely on companies to manage and track user permissions. This does work, but can leave users with limited visibility into how their data is used.
Blockchain consent gives the user more say in how their information is shared. Relevant parties — users, companies requesting the permissions, third parties needing access to the data for processing — can see exactly who has accessed the data, when, and for what purpose.
Security is another key difference. Traditional systems are centralized, meaning data is stored in one place and subject to one company’s security measures, which can make it more vulnerable to unauthorized access.
In contrast, the blockchain distributes information across multiple secure networks. This reduces the risk of a single point of failure and makes it harder to compromise any user’s data.
The benefits of blockchain for consent management
Blockchain consent management has the power to reshape the way companies handle user permissions. It solves some of the issues found in traditional systems by combining secure technology with features that benefit both users and businesses.
Here’s why companies are adopting blockchain for consent management.
Blockchain consent is decentralized and offers data integrity
The blockchain distributes data across multiple nodes, which reduces the risks of breaches or system failures. Since consent records are stored permanently, they can’t be altered without detection. This helps keep data secure and builds trust.
Consent management on the blockchain is transparent and auditable
Every consent action is recorded in the equivalent of a transparent ledger. This makes it easy for users and regulators to track compliance. Organizations can also use this record to demonstrate compliance with privacy laws like the GDPR. This transparency can foster trust and reduce disputes over data use.
Blockchain offers more user control and privacy
Blockchain enables users to control exactly what data they share, with whom, and for what purpose. This is foundational for Privacy-Led Marketing, which focuses on ethical and user-centered practices. For businesses, it means having access to more accurate, consent-driven data that improves the efficiency of marketing campaigns.
Consent on blockchain enables granular consent settings
On blockchain, users can set detailed preferences, specifying which data points they share and who can access them. This level of control supports universal consent management by enabling users to manage permissions across multiple platforms. This helps businesses align their data use with user expectations and build stronger customer relationships.
Blockchain uses smart contracts for automation
Smart contracts automatically enforce consent rules based on user preferences. They restrict data access to agreed parameters, reducing compliance risks. This automation also makes consent-based marketing easier by streamlining permission management.
Blockchain consent management provides real-time verification
Blockchain enables businesses to verify user consent instantly. They can then use data according to the latest permissions, improving operational efficiency. As blockchain also supports Privacy-Led Marketing, companies can rely on verified first-party consent.
How does blockchain consent management work?
Blockchain consent management offers a secure, transparent way to control how your personal information is used. Instead of relying on vague agreements or hidden terms, blockchain consent records and enforces your choices, and makes them easy to track. Here’s how it works:
- When you grant permission for a company to use your data, your choices are securely recorded on the blockchain.
- This record acts like a digital ledger, shared across multiple computers. This makes it nearly impossible to alter that record without your knowledge.
- You can decide exactly what data to share and with whom, which offers more precision than simply clicking “I agree.”
- Smart contracts enforce your consent choices, maintaining compliance without manual oversight.
- Every time someone accesses your data, it’s logged in the consent management of the blockchain. It creates a transparent history you can check anytime.
- If you change your mind, you can easily update your permissions, and the system will automatically follow your new preferences.
This approach puts the user in control of their personal information while giving companies a straightforward way to prove they’re respecting their audience’s wishes.
How to implement blockchain consent management: Best practices
Using blockchain for consent management can improve data control and security, but getting it right requires careful planning. Here are some best practices to keep in mind.
Understand your organization’s consent needs
Start by identifying your organization’s specific consent requirements. Understand what types of data you manage and how consent is collected, stored, and used. Align these needs with your operational goals to help ensure the blockchain solution fits your processes.
Choose the right blockchain platform
Pick a platform that suits your company’s needs. Public blockchains like Ethereum offer transparency, but may not be suitable for sensitive data. Private blockchains, such as Corda — a popular option in the financial sector — provide more control and customization. This can be useful for compliance-heavy industries.
Confirm that it integrates with existing systems
Verify that the blockchain solution works well with your current systems to avoid operational disruptions. In addition, check that databases and interfaces can support blockchain’s distributed structure.
Provide user-friendly interfaces
The success of blockchain consent management depends on its usability. The system and its layout should be easy for your audience to use. This means creating simple dashboards where users can manage their data permissions. Work with user experience experts to design intuitive tools that simplify complex blockchain processes.
Educate stakeholders
Blockchain can be complex. Offer training sessions, workshops, or guides to help stakeholders understand its benefits. Clear communication builds trust and encourages adoption across your organization.
Use enhanced privacy tools
Employ technologies like encryption and zero-knowledge proofs to protect sensitive data stored on the blockchain. This keeps data secure while maintaining the transparency of the system.
Test and plan for scalability
Before rolling out a blockchain system, test it thoroughly before launching. Identify potential issues, such as slow performance or security risks. Plan for future growth by designing a system that can handle more users and transactions over time.
Implement smart contracts
Use smart contracts to automate blockchain consent management processes. These contracts can define terms, track permissions, and revoke access when needed. Make sure that the code is secure and reliable before deployment.
Continuously monitor and improve
Regularly review how the system performs and gather user feedback. Based on new data privacy regulations, implement mechanisms for users to easily adjust their consents and opt out when necessary. Make updates as needed to improve functionality and address issues that arise over time.
Blockchain consent management and data privacy regulations
As data privacy laws tighten worldwide, many companies are seeking simpler ways to stay compliant. Blockchain consent management offers a solution that enhances compliance without disrupting operations.
Different regulations have unique requirements. Here’s how blockchain can address the specific demands of global data privacy laws.
GDPR compliance and blockchain consent management
The GDPR in the European Union sets high standards for data privacy. It emphasizes user consent and control over personal data. Blockchain technology aligns with several GDPR principles, including data minimization, transparency, and accountability.
Blockchain technology provides a secure and transparent way for organizations to keep records of consent transactions. Once recorded, these records cannot be changed, making them resistant to tampering. This helps organizations easily track and prove compliance with regulatory requirements.
However, the GDPR also presents challenges that blockchain technology does not address. The regulation’s “right to be forgotten” requirement conflicts with blockchain because its records cannot be easily changed or deleted. To solve this, many companies use hybrid solutions. This typically means keeping personal data outside the blockchain while storing only consent-related information on it.
Data privacy laws across the US
The United States does not have a single federal privacy law equivalent to the GDPR. However, state-level regulations like the California Consumer Privacy Act (CCPA), now amended by the California Privacy Rights Act (CPRA), introduced requirements for user consent and data control. Blockchain-based consent management systems could offer a tamper-proof record of user permissions, enabling businesses to demonstrate compliance with the CCPA’s requirements for data collection, deletion, and opt-out requests.
PIPEDA and blockchain in Canada
The Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada emphasizes the importance of user consent for data collection and processing. Blockchain can support PIPEDA’s principles of accountability and individual access by offering a decentralized and user-centric consent management system.
LGPD compliance and blockchain in Brazil
Brazil’s General Data Protection Law (LGPD) closely mirrors the GDPR in its approach to data privacy. It mandates that personal data processing must be based on consent or other legal grounds, and individuals have the right to access, correct, and delete their data.
Blockchain technology can support a company’s efforts to be LGPD-compliant by providing transparency and security in consent management. However, like with the GDPR, blockchain’s permanent nature makes it difficult to delete data upon request. To comply with the law, companies may need to use off-chain solutions.
Data privacy regulations in Asia
Privacy regulations throughout Asia, such as Japan’s Act on the Protection of Personal Information (APPI) and China’s Personal Information Protection Law (PIPL), impose strict requirements on data handling and user consent.
In Japan, organizations must obtain clear user consent before processing personal data, and blockchain can provide a transparent and auditable method to record such consent.
In China, the PIPL mandates strict data localization requirements. This means that blockchain consent solutions must support compliance by storing consent data in approved locations while maintaining operational efficiency.
The challenges of using blockchain for consent management
At this point, blockchain may appear to be a promising solution for consent management. However, despite its potential, several challenges must be addressed within the technology before it can become a practical option for businesses.
- Data storage and deletion: Blockchain isn’t designed to store large amounts of personal data, and its permanent nature makes it difficult to comply with privacy laws that require data to be deleted on request.
- Privacy concerns: Public blockchains can expose sensitive information, raising privacy risks. Private blockchains provide more control, but come with added complexity and costs.
- Regulatory uncertainty: Existing privacy laws weren’t created with blockchain in mind, leading to confusion and potential compliance risks for businesses.
- Complexity and usability: Implementing blockchain-based consent management systems requires technical expertise that many organizations lack, making adoption challenging.
Wrapping up: Blockchain’s role in compliance
Blockchain consent management isn’t a cure-all for data privacy challenges. Still, it does offer a practical solution for improving transparency, security, and user control. By addressing some limitations in traditional systems, it helps businesses navigate privacy regulations while respecting user preferences.
Its implementation, however, requires careful planning and some technical know-how. But as technology and data privacy regulations evolve, blockchain may play a role in shaping better data practices.
Privacy compliance used to be simpler. Your team would perhaps update privacy notices yearly, run occasional audits, and call it a day.
Now, it’s a daily challenge for enterprise companies that need to manage user consent across dozens of tools and platforms while navigating global privacy laws. You could spend countless hours reviewing tools one by one, checking boxes manually, and customizing implementations. This approach isn’t just time-consuming: it’s prone to errors and impossible to scale.
Manual processes that worked a few years ago simply can’t keep up with today’s privacy regulations.
But here’s the good news: automation is changing how we handle data and privacy compliance, making it simpler and more reliable than ever.
What is compliance automation?
Compliance automation means using technology to minimize manual, administrative work in compliance activities.
With dedicated software solutions, companies can automate compliance to streamline various compliance procedures relevant to their industry.
Compliance automation tools track internal systems, processes, and controls to check for adherence to the granular policies of applicable regulations and standards without requiring ongoing involvement.
For example, when a user updates their privacy preferences, these changes automatically apply across connected tools and platforms.
This reduces the need for manual workflows while providing real-time insights that help organizations stay on top of compliance. As a result, companies not only boost efficiency, but can also continuously uphold regulatory standards.
Manual versus automated compliance management
Traditional, more manual compliance relies heavily on spreadsheets, email chains, and individual tool reviews. This approach typically requires privacy teams to spend hours gathering evidence, conducting access reviews, and documenting their findings. And because it’s time-intensive, manual compliance often means playing catch-up rather than staying proactively compliant.
In contrast, automated compliance streamlines these tasks. Consent preferences sync across tools, access reviews run on schedule, and documentation updates in real-time as systems change. Automation not only reduces administrative burden but can also strengthen security.
In fact, companies using security AI and automation saved an average of USD 2.2 million in breach costs compared to those without automation. By shifting to an automated approach, privacy teams can focus on strategy rather than routine tasks, improving both compliance and risk management.
Why is compliance automation important?
Managing consent at scale and keeping up with changing privacy laws across different regions can feel overwhelming. For many companies, manual compliance is a constant struggle.
Plus, privacy regulations have evolved rapidly in recent years:
- The General Data Protection Regulation (GDPR) in Europe introduced strict consent rules and data subject rights.
- The California Consumer Privacy Act (CCPA) set new transparency obligations, and the California Privacy Rights Act (CPRA) expanded consumer protections even further.
- Laws in states Virginia, Colorado, Utah, and Connecticut each add their own requirements, and many states are already passing amendments to their privacy laws.
- Global regulations like Brazil’s Lei Geral de Proteção de Dados (LGPD) and China’s Personal Information Protection Law (PIPL) create additional complexity.
Each law comes with its own definitions, enforcement mechanisms, and compliance obligations. So, a manual approach means constantly researching updates, retraining staff, and making changes across multiple systems. It’s an ongoing, resource-heavy process.
Given the number of global privacy laws, it’s no surprise that 95 percent of businesses are working to build a culture of compliance. But with regulations shifting, budgets tightening, and security threats increasing, keeping up can feel like an endless game of catch-up. That’s why more companies are turning to compliance automation.
Compliance automation helps businesses stay ahead of regulatory changes, strengthen security, and build customer trust. Instead of reacting to new requirements as they come, companies can implement scalable solutions that evolve with the laws, reducing risk while making compliance more efficient.
Benefits of compliance automation
Keeping up with privacy regulations is a constant challenge, especially when relying on manual processes. Compliance automation removes much of the repetitive, time-consuming work, helping teams stay accurate, efficient, and ahead of regulatory changes.
Here’s why more and more companies are choosing to automate their data privacy compliance.
- Cuts down on repetitive tasks: Automating compliance processes frees up time and resources previously spent on manual privacy work.
- Reduces human error: Manually updating privacy settings across multiple tools increases the risk of mistakes. Automation checks operations and applies changes consistently.
- Speeds up campaigns and projects: Automated compliance checks happen almost instantly, eliminating delays caused by manual reviews.
- Improves efficiency: Automation streamlines workflows, eliminates bottlenecks, and continuously maintains compliance.
- Provides real-time monitoring and reporting: A centralized compliance view helps teams spot and address risks early, so there’s no need to panic in the face of last-minute audits.
- Lowers costs: Automation reduces the need for large compliance teams and external audits while helping businesses avoid costly noncompliance penalties.
Instead of playing catch-up, companies can take a proactive approach. They can save time, reduce risk, and stay compliant without the extra workload that comes with manual compliance.
How does compliance automation work?
Think of compliance automation as a central control system for your privacy operations. It connects to your marketing tools, analytics platforms, and other systems through Application Programming Interface (API) integrations.
So, when an event happens — such as a user updating their privacy preferences — the system automatically applies the necessary changes across your technology stack.
But automation goes beyond handling individual events. It keeps compliance running smoothly in the background while covering three key areas: management, monitoring, and testing.
Automated compliance management
Automated compliance management covers your privacy program’s day to day operation. It handles tasks like syncing consent preferences, maintaining documentation, and keeping privacy practices consistent across systems.
For example, when a user updates their consent preferences on your website, an automated system will:
- Record the change in a central database
- Push updates to connected marketing tools like analytics, customer relationship management (CRM), and advertising platforms
- Generate and store a record of the change for future audit purposes
- Apply the appropriate data handling rules based on the user’s new preferences
All of this happens without manual intervention, which means that consent choices are respected instantly across your entire technology ecosystem.
Automated compliance monitoring
Automated compliance monitoring acts as an early warning system. Rather than discovering problems during periodic manual reviews, the system continuously checks for potential issues and will alert you when something needs attention.
A good monitoring system will:
- Regularly scan your website and apps for unauthorized trackers or tags
- Check that privacy notices match your actual data collection practices
- Verify proper consent collection before data processing begins
- Alert teams to potential compliance gaps before they become significant issues
This continuous monitoring approach means you’re no longer working with outdated compliance information or discovering problems months after they appear.
Automated compliance testing
Automated compliance testing helps verify that your privacy practices work as intended. It can regularly check system configurations, test consent collection and management, and support proper data handling across your tools.
Automated testing might include:
- Simulating user interactions with consent mechanisms to verify proper function
- Checking data flows to ensure information only moves where permitted
- Verifying that privacy preferences persist across user sessions
- Confirming that data subject rights requests are properly processed
By automating these tests, organizations can maintain confidence in their privacy practices without spending time and resources on manual verification for every scenario.
How to get started with compliance automation
Here’s a quick run-through of how you can implement compliance automation.
1. Assess your current compliance needs
Begin by identifying your regulatory obligations. These will be based on your business activities, geographic scope, and industry. Determine which specific compliance areas cause the most friction in your operations.
2. Map your technology ecosystem
Document all the tools, platforms, and systems that process personal data. These may include marketing analytics, CRM systems, email platforms, advertising tools, and website technologies. Understanding your tech landscape will make for smoother integration.
3. Define your compliance automation goals
Identify the compliance tasks that will benefit most from automation. Prioritize areas that are time-consuming or prone to error, such as:
- Consent management across systems
- Documentation and evidence collection
- Vendor risk assessment
- Data subject rights fulfillment
4. Select the right automation platform
Focus on finding an automation platform that integrates seamlessly with your existing technology stack. It should meet the unique needs of your industry and be scalable as your business grows.
Additionally, choose a platform that provides regular updates to stay aligned with evolving regulations.
5. Implement automated regulatory compliance in phases
Start with thoroughly automating one compliance area before expanding. Many companies begin with consent management automation before moving to more complex areas, like documentation or testing.
6. Train your teams
Make sure your marketing, IT, and legal teams understand the new automated workflows and their responsibilities within the system.
7. Monitor and refine
Regularly assess the effectiveness of your automation solution and adjust as needed to improve efficiency and compliance outcomes.
Common challenges of compliance automation and how to overcome them
While compliance automation offers significant benefits, successful implementation comes with challenges. Here’s how to overcome some of the most common obstacles.
Integration complexities
One of the main challenges is connecting automated systems with existing tools and platforms. To do so, start with key integrations and expand gradually.
Work with vendors that offer pre-built connections to common platforms, and prioritize automation for systems that handle sensitive data or present the highest compliance risks.
Middleware solutions can also help bridge gaps between systems that don’t have native integration capabilities.
Team adoption
Getting teams to trust and effectively use automated solutions can be difficult. To ease the transition, provide clear training on new workflows and demonstrate how automation saves time and reduces errors.
Involve key stakeholders early in the implementation process and document success stories where automation prevented compliance issues or improved efficiency.
Simple guides explaining how automation changes daily processes for different teams can also be helpful.
Maintaining human oversight
Finding the right balance between the ease of automation and the necessity of human judgment is crucial. Automate routine tasks, but keep strategic decision-making in the hands of your team.
Set clear criteria for when human review is necessary and establish escalation paths in case potential issues arise.
Regularly review how automation is performing, and adjust human oversight as needed.
Managing upfront costs
The initial investment in compliance automation can raise concerns. While it’s true that there is an upfront cost for software and implementation, the long-term savings quickly offset these expenses by reducing compliance overhead and avoiding costly fines.
Companies may benefit from starting with smaller automation projects that demonstrate clear ROI. Alternatively, consider phased implementation approaches to spread costs over time.
Automated compliance across different industries
Compliance automation needs vary significantly across industries, with each sector facing unique regulatory requirements and operational challenges. Organizations need to understand industry-specific applications to implement the most effective compliance automation strategies.
Automated compliance in the finance industry
The finance and banking industries operate under some of the strictest regulations. Automation plays a crucial role in handling processes like Know Your Customer (KYC), anti-money laundering (AML) checks, and risk assessments.
For financial institutions, compliance automation can simplify tasks like:
- Verifying customer identities
- Monitoring transactions for suspicious activity
- Managing regulatory reporting across various jurisdictions
- Collecting evidence for audits
- Implementing privacy policies on digital platforms
This approach not only supports compliance but also streamlines operations, enhancing efficiency and the customer experience.
Regulatory compliance automation in the healthcare sector
Healthcare organizations in the US must balance Health Insurance Portability and Accountability Act (HIPAA) compliance, as well as following other regulations, while delivering top quality patient care.
Automation helps manage access to patient data, maintains audit trails, and supports consent management.
In healthcare, compliance automation typically covers:
- Tracking patient consent across systems
- Managing access to protected health information
- Documenting security measures
- Detecting breaches and preparing notifications
- Streamlining HIPAA-compliant marketing workflows
These automated processes enable healthcare organizations to prioritize patient care while safeguarding privacy and meeting regulatory standards.
Automated security compliance in ecommerce
Ecommerce businesses face the challenge of managing privacy compliance across multiple regions. Automated systems help track local regulations, handle cookie consent, and manage data subject rights requests. These steps are especially important as privacy laws continue to evolve globally.
For ecommerce businesses, compliance automation often includes:
- Maintaining cross-border data transfer compliance
- Adhering to Payment Card Industry (PCI) standards
- Managing cookie consent across different regions
- Complying with regional marketing regulations
- Handling user preferences on shopping platforms
These automated solutions enable ecommerce businesses to scale internationally while maintaining consistent compliance with various privacy laws.
IT and security compliance automation
For IT teams, compliance automation is essential for managing security and risk.
Cybersecurity threats are on the rise, and compliance regulations demand strict controls over data access, storage, and usage. Without automation, maintaining compliance can be time-consuming and expensive. However, companies that do implement compliance technology have cited reduced compliance costs by an average of USD 1.45 million.
IT compliance automation also helps businesses stay ahead by enabling continuous security monitoring and aligning systems with industry standards like ISO 27001, NIST, and SOC 2. Common functions of automated compliance solutions include:
- Continuously assessing security posture against regulatory requirements
- Automatically documenting security controls for audit purposes
- Regularly scanning for unauthorized system changes or configurations
- Collecting evidence of security practice implementation
- Streamlining security incident response workflows
Patching is another critical compliance requirement that automation makes more manageable. Security patches must be applied promptly to prevent vulnerabilities, yet manual patching can be inconsistent and prone to delays. Automated patching keeps systems up to date, which reduces security risks and keeps organizations in compliance with regulatory requirements.
Access management also plays a key role in IT compliance automation. Many regulations require strict control over who can access sensitive data. Instead of relying on manual reviews, compliance automation enforces user access policies, automates regular access reviews, and ensures proper role-based controls, which minimizes the risk of unauthorized access.
By integrating compliance automation into security processes, IT teams can reduce costs, minimize regulatory risk, and maintain continuous compliance without the burden of manual upkeep.
How Usercentrics can help your compliance automation efforts
Manual compliance processes take too much time, increase the risk of errors, and are difficult to keep up with as regulations change. Compliance automation helps businesses stay on top of requirements without the constant manual effort.
Usercentrics Consent Management Platform can help you simplify privacy compliance by automating key tasks like consent management across your websites and apps. We’ll help make it easier to follow privacy laws such as the GDPR and the CPRA.
Usercentrics can help you:
- Automate consent collection with customizable, on-brand user interfaces that meet regulatory requirements across jurisdictions.
- Sync consent preferences automatically across your technology stack, helping you achieve consistent privacy standards throughout your digital ecosystem.
- Provide comprehensive and secure compliance records to maintain complete audit trails of consent activities and privacy preference changes.
- Monitor compliance status through real-time dashboards that highlight potential issues before they become problems.
Instead of tracking regulations manually, businesses can rely on our compliance automation to collect data and user permissions in a privacy-compliant way.
Watch our on-demand session to learn how to properly manage cookies and avoid legal risks.
This webinar, featuring Magdalena Aleksova (Usercentrics) and Adrian Nowakowski (Up Blue), provides practical insights into cookie compliance, legal risks, and best practices for managing cookies on your website.
What You’ll Learn:
- Key differences between preference, analytical, and marketing cookies
- Legal and financial risks of incorrect cookie handling
- How to verify if your website is compliant with regulations
- Recent cases of companies penalized for non-compliance
Who Should Watch?
- Marketing & Legal Professionals – Stay updated on cookie compliance regulations
- Website Owners & Developers – Learn how to manage cookies correctly
- Business Leaders – Understand the financial risks of non-compliance