The California Consumer Privacy Act (CCPA) set US standards for consumer privacy and data protection. It requires businesses that operate in digital markets to establish compliant data collection practices, communicate these to their customers, and implement measures to protect this data.
Meeting CCPA requirements can entail a large investment of time and resources, but failing to adhere to its provisions can be even more costly. The fines, legal fees, and loss of customer trust that stem from noncompliance are significant risks to your business’s bottom line.
Compliance tools are invaluable in helping you adhere to CCPA requirements. They simplify privacy compliance by streamlining consent collection, management, and signaling according to regulatory requirements, so that you can remain focused on your core business operations.
Our picks of the top CCPA compliance software:
Essential features for CCPA compliance solutions
Complying with the CCPA helps your business to protect consumer rights and build customer trust while also safeguarding it against various noncompliance risks, including CCPA class action lawsuits.
Using a robust CCPA compliance tool can help you to meet the requirements of this regulation and the California Privacy Rights Act (CPRA), which expanded and amended it. When choosing your platform, it’s important to evaluate the following features.
- Consent management: A consent management platform (CMP) enables you to securely collect, manage, and signal user consent in line with CCPA requirements.
- Sensitive data handling: Look for features that help identify, secure, and manage the processing of sensitive personal information.
- Data processing: Ensure there are mechanisms for monitoring and controlling the processing of personal data so it meets the CCPA’s transparency, purpose limitation, and data minimization requirements.
- Data privacy management: Make sure there are comprehensive privacy management tools available to maintain compliance documentation, automate scanning for technologies in use that require consent, keep consent notices up to date, and manage consent choices in real-time.
| CCPA tool | Key features | Usability score | Recommended for |
|---|---|---|---|
| Usercentrics |
|
4.0/5 (Capterra) | Businesses of all sizes |
| TrustArc |
|
4.1/5 (SoftwareReviews) | Small to medium-sized businesses |
| OneTrust |
|
3.8/5 (Capterra) | Large corporations |
| Osano |
|
4.6/5 (G2) | Freelancers |
| iubenda |
|
4.5/5 (Capterra) | Small businesses |
| Ketch |
|
4.5/5 (G2) | Agencies |
6 great tools for CCPA compliance
Maintaining compliance with the CCPA doesn’t have to be a daunting task. Here are six tools designed to help you adhere to stringent data privacy laws efficiently so you can focus on what you do best — run your business.
1. Usercentrics
Usercentrics is an all-in-one CMP that enables compliance with the CCPA, GDPR, and other major data privacy laws. It features more than 2,200 legal templates to save time and resources during implementation and maintenance.
This powerful solution integrates easily with popular content management systems (CMSs) and web builder platforms. It enables privacy compliance right out of the box, and you can also customize it extensively, from visual branding to regulatory coverage and more.
However, note that the extensive feature set can make it somewhat challenging for new users to master initially.
Top features
- DPS Scanner: Identify third-party cookies and other tracking technologies on your website to ensure that you’re informing users about the services in use and that you’re able to control them in line with users’ consent choices.
- Legal templates: Access 2,200+ ready-to-use or customizable legal templates to save time on setup, categorization, and maintenance.
- Google-certified: Comes with Google Consent Mode v2 integrated and ready to use.
- Cross-domain and cross-device consent: Improve user experience by obtaining consent for all your websites and apps with a single consent interaction.
- Robust analytics: Get a detailed view of user interaction and consent rates to drive informed decision-making and optimize opt-ins.
Pricing plans
Usercentrics offers a 30-day free trial, after which users can sign up for one of the following paid plans.
- Starter: USD 60/month for up to 50,000 sessions
- Advanced: USD 175–1,150/month for 50,000+ sessions
- Premium: Custom pricing
| Full UI customization | Analytics data only available for 90 days |
| Automated third-party cookie blocking | |
| Flexible pricing and packages |
2. TrustArc

TrustArc provides businesses with automated privacy solutions to help them achieve compliance while increasing user trust. Once it’s up and running, the platform is easy to implement at scale, but you may have to invest significant time to overcome a learning curve to unlock its full potential.
Top features
- Auto-law identification: Gain a better understanding of privacy regulations and standards so you can maintain compliance.
- Trust Center: Display all CCPA-related data privacy information in one place to build trust with your customers.
- Multiple APIs: Integrate third-party applications and tools into your website with Rapid and REST APIs for compliant data collection.
Pricing plans
Contact TrustArc for pricing.
| Google-certified CMP provider | Poor customer support, according to some users |
| Easy to use (G2 user reviews) | |
| Drag-and-drop customization |
3. OneTrust

With an extensive set of privacy management tools, OneTrust enables businesses to safely handle customer data while minimizing security, privacy, governance, and compliance risks. The tool’s automation features can reduce the complexity involved in staying compliant, but you may experience implementation challenges, according to some users.
Top features
- Data intelligence: Centralize and organize data to easily identify sensitive information and understand potential risks.
- Data mapping: Gain an understanding of how data flows through your organization to enable the implementation of CCPA-compliant measures at every stage of handling.
- Reporting and logs: Be prepared for an audit and equipped to show that your business is in compliance with CCPA requirements.
Pricing plans
Contact OneTrust for pricing.
| Vendor risk management | Pricing information not publicly available |
| Automated compliance assessments | |
| Incident and breach management |
4. Osano

Osano enables more than 40,000 users to meet the requirements of data privacy laws. Although it offers an all-in-one solution that centralizes CCPA compliance management, some users note that customization options are limited.
Top features
- “No Fines, No Penalties” Pledge: Claim up to USD 200,000 compensation for any data privacy-related fines or penalties incurred while using Osano.
- Automated data request workflows: Collect, track, and fulfill customers’ requests to disclose, access, or delete the personal information you have on hand, as required by the CCPA.
- Regulatory alerts: Get updates about upcoming changes to the CCPA and other data privacy laws to stay ahead of requirements and maintain compliance.
Pricing plans
Osano has two self-service cookie consent packages:
- Free: USD 0/month for 1 user, 1 domain, and up to 5,000 visitors/month
- Plus: USD 199/month for 2 users, 3 domains, and up to 30,000/month
Contact Osano for pricing for the Privacy & Trust Assurance, Privacy Essentials, and Privacy Operations & Government plans.
| Secure blockchain storage | Free plan only supports 5,000 monthly visitors |
| Geolocation capabilities | |
| Easy setup (G2 user reviews) |
5. iubenda
iubenda’s CMP offers what they refer to as attorney-level consent management tools that help businesses take the guesswork out of compliance. However, geolocation-based consent settings, which are important for tailoring consent banners to user location, aren’t available on all plans.
Top features
- Privacy policy generator: Produce legally compliant documents that detail your business’s data handling practices.
- Automatic policy updates: Be informed of regulatory changes with automatic policy updates drafted and implemented by attorneys.
- Consent database: Save and manage user consent choices as required by the CCPA and CPRA.
Pricing plans
iubenda provides a free plan for websites with fewer than 5,000 page views per month. They also offer a free 14-day money-back guarantee on their three paid packages. Pricing is as follows:
- Essentials: USD 5.99/month/site or app
- Advanced: USD 24.99/month/site or app
- Ultimate: USD 99.99/month/site or app
| Automatic updates to maintain compliance | Only one language included with the Essentials plan |
| Chat and email support | |
| Centralized dashboard for managing multiple websites |
6. Ketch

Ketch is a design-first CMP that places emphasis on the look and feel of data privacy notices, as well as compliance requirements. This US provider’s no-code solutions are aimed at teams that don’t have much technical expertise, but some users note that the platform has a learning curve and its interface is sometimes confusing.
Top features
- Identity resolution: Recognize users across digital channels and devices and automatically apply their consent preferences.
- Ketch Smart Tag: Add privacy notices to your website with lightweight script that aligns with current web design best practices.
- Ketch permit vault: Access up to date records of your customers’ privacy choices and retrieve records of processing activities with one click.
Pricing plans
Ketch offers three plans at three different price points:
- Ketch Free: USD 0
- Ketch Essentials: From USD 350/month
- Ketch Pro: Contact Ketch for pricing
| No-code solution | Free plan only supports 5,000 monthly visitors |
| Easy to use (G2 user reviews) | |
| Over 1,000 pre-built integrations |
How to stay CCPA-compliant with a consent management platform
Managing customers’ personal information, collecting user data, and implementing and maintaining data security in line with the CCPA is a complex and demanding task. A CMP reduces the burden of compliance by automating and streamlining the processes involved in data collection and helping to ensure that they adhere to regulatory standards.
With a CMP, businesses can efficiently establish whether they’re compliant with the CCPA and identify specific actions for achieving compliance. This significantly reduces the hassle and risk associated with adhering to this complex regulation.
Usercentrics for CCPA peace of mind
Complying with the CCPA requires a thorough understanding of the law’s detailed provisions around data collection, storage, and processing. What’s more, growing demands from consumers for the respect for and protection of their data mean that compliance is no longer just a legal requirement but a necessity for business success and longevity.
The recent introduction of the CPRA has further elevated these challenges, building on the CCPA’s requirements. As these laws continue to evolve, businesses need to remain agile and in the know in order to adapt to new guidelines and avoid costly financial and reputational damage.
Usercentrics’ CMP is designed to enable businesses to collect and manage user data in a transparent manner in order to meet the requirements of the CCPA and CPRA. Our Google-certified tool features an extensive library of more than 2,200 legal templates, a best-in-class DPS Scanner, and robust analytics for informed decision-making.
By integrating Usercentrics CMP into your tech stack, privacy compliance can be as seamless as it is robust, and you can align with current regulations, prepare for future changes, and protect your operations and your reputation.
The information presented in this article is accurate based on publicly available sources as of the date of publication. Details about products, features, pricing, etc. may change over time.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.
The ever expanding number of data privacy laws — and their often lengthy and varied lists of requirements — means that a manual approach to meeting and monitoring compliance outcomes is virtually impossible.
To stay ahead of the curve and avoid potential consequences of breaching these regulations, you need effective compliance management software. These tools are key to building privacy compliance into your day to day business practices and managing risk.
We’ve reviewed six tools that can help you streamline your compliance efforts and optimize your data privacy outcomes, so you can select the ideal compliance management software for your business.
When making our selection, we’ve considered factors like consent management features, analytics, and reporting capabilities.
Our top picks for compliance management:
| Compliance management software | Key features | Usability score* | Pricing |
|---|---|---|---|
| Usercentrics |
|
4.7 (Capterra) | From USD 60/month |
| consentmanager |
|
4.2 (Capterra) | Free version available, paid tiers from USD 21/month |
| iubenda |
|
4.5 (Capterra) | From USD 5.99/month |
| Didomi |
|
4.6 (Capterra) | Pricing available on request |
| Osano |
|
4.5 (G2) | Free plan available, Plus plan priced at USD 199/month |
| Cookie Information |
|
4.2 | From EUR 15/month |
*Ease of use scores found via Capterra and/or G2 user reviews
Why are compliance management tools a must in 2024?
Compliance management software enables businesses to comply with data privacy laws by automating tasks once implemented and monitoring regulatory changes. These tools help ensure the process is seamless, requires limited resources, and enable organizations to offer granular consent management options to users.
Failure to adhere to the rules set by various data privacy laws can result in fines. What’s more, the reputational damage that results from noncompliance can lead to a loss of customer trust that can be even more damaging in the long term.
However, you need access to consented data to launch successful marketing initiatives, improve products, and provide the kinds of personalized experiences customers expect. A compliance management solution provides users with the transparency and control they require while meeting compliance criteria and securely storing data according to regulatory requirements.
By automating and streamlining compliance tasks, these specialized tools make compliance easier while reducing the risk of human error.
Our picks for 6 top compliance software solutions
Collating a cookies checklist or data privacy to-do list are just two requirements for companies seeking to become privacy-compliant with relevant regulations. This can be extra challenging for smaller organizations with limited resources. Fit-for-purpose software can help you minimize the burden of achieving and maintaining compliance.
1. Usercentrics
Usercentrics CMP is an industry-leading consent management tool that equips businesses to manage both website and application consent via one interface.
Easily customized consent banners enable granular consent management, which helps organizations stay compliant while delivering a consistent and branded user experience. Interaction Analytics enable businesses to see how users are engaging with consent banners so they can optimize opt-in rates.
Usercentrics is a powerful platform, so there may be a bit of a learning curve for non-technical teams looking to master its more advanced features. That said, there are plenty of useful resources online, and the customer support team is always available to help with troubleshooting.
Key features
- Granular consent management: Give users complete control over the data they share across domains and devices in just a few clicks.
- Robust analytics and reporting: Get detailed information about cookie acceptance rates to enable informed decision-making.
- A/B testing tools: Gain valuable insights into user behavior to optimize your CMP and consent rates.
- Data Processing Service (DPS) Scanner: Identify all third-party technologies that are collecting customer data from your website.
- Google-certified CMP: Comply with Google’s EU user consent policy requirements and integrate with Google Consent Mode v2 by default.
- Geolocation: Serve users consent notices that meet the requirements of their jurisdiction’s data privacy laws based on their location.
Usercentrics pricing
Usercentrics offers a free 30-day trial, after which users can sign up for one of the following paid plans.
- Starter: USD 60/month for up to 50,000 sessions
- Advanced: USD 175–1,150/month for 50,000+ sessions
- Premium: Custom pricing

| 2,200+ legal templates | Analytics data only available for 90 days |
| Full UI customization | |
| 60+ languages supported |
2. consentmanager

consentmanager promises to help businesses increase their cookie acceptance rates by giving users access to in-depth reporting and intelligent A/B testing tools. However, with its main focus on the GDPR, the platform may not be the best option for businesses with global operations.
Key features
- EU servers: Store user consent records on servers located in the EU.
- Automatic cookie deletion: Remove cookies when users reject tracking.
- Time-adjustable re-consent: Set intervals for users to reconfirm tracking consent.
consentmanager pricing
- Basic: USD 0 for up to 5,000 pageviews/month on 1 website.
- Beginner: USD 21/month for up to 100,000 pageviews/month on 1 website.
- Standard: USD 53/month for up to 1 million pageviews/month on 3 websites.
- Agency: USD 211/month for up to 20 million pageviews/month on 20 websites.
- Enterprise: Custom pricing based on demand.
| Consent management for website, mobile apps, connected TVs | No geolocation capabilities |
| GDPR-compliant servers | |
| Integrated cookie checker |
3. Iubenda
iubenda provides a complete set of what they refer to as attorney-level privacy and consent management tools to help ensure your website and apps are compliant with laws across multiple jurisdictions. While it’s a Google-certified CMP partner, not all GDPR and CCPA compliance features are available in every plan.
Key features
- Consent Database: Access and review consent records via a user-friendly database.
- Data processing activities register: Document how you store and use the data you collect from your website and app visitors.
- Policy generators: Easily generate and manage privacy and cookie policies that comply with main international laws.
iubenda pricing
- Essentials: USD 5.99/month per site or app
- Advanced: USD 24.99/month per site or app
- Ultimate: USD 99.99/month per site or app
| Attorney-level compliance solutions | Only 11 languages available on consent banners |
| Customizable cookie and privacy policies | |
| Automatic cookie classification |
4. Didomi
Didomi is a cloud-based CMP that the company touts as seamlessly integrating into businesses’ existing tech stacks to make it easier to achieve compliance with major data privacy laws. Unfortunately, the platform doesn’t offer ready to use solutions, so you’ll need to go through a consultation process to establish which tools will meet your needs.
Key features
- Multi-regulation CMP: Geotargeted consent banners tailored to user location.
- Global privacy control: Implement appropriate data collection measures based on users’ previous consent choices.
- Consent versions and proofs: Track consent history across various versions of notices to see what users agreed to at any point in time.
Didomi pricing
Contact Didomi for pricing for Content Essentials, Core Privacy UX, and Privacy UX Plus plans.
| APIs and SDKs for seamless integration with existing infrastructure | Opaque pricing |
| Granular consent controls | |
| Customer support via live chat and email |
5. Osano

Osano supports compliance for more than 11,000 organizations worldwide with its unified consent and preference hub. Although it has some powerful features, some users note that customization options are limited.
Key features
- Cookie Consent: CMP for complying with regulations in over 50 countries.
- Data mapping: Generate visualizations of your data collection and processing practices to help identify potential risks and opportunities.
- Regulatory updates: Receive notifications about changes to the data privacy laws and regulations applicable to your business.
Osano pricing
Osano has two self-service cookie consent packages:
- Free: USD 0/month for 1 user, 1 domain, and up to 5,000 visitors/month
- Plus: USD 199/month for 2 users, 3 domains, and up to 30,000/month
Contact Osano for pricing for the Privacy & Trust Assurance, Privacy Essentials, and Privacy Operations & Government plans.
| “No Fines, No Penalties” Pledge | Free plan only supports 5,000 monthly visitors |
| Free tier | |
| Data stored on blockchain |
6. Cookie Information

Cookie Information equips businesses with the tools they need to deploy cookie banners and privacy notices that comply with the GDPR, CCPA, and other data privacy laws. However, some users note they would like more customization options.
Key features
- Data discovery: Find and flag data management practices that don’t comply with your organization’s policies.
- Compliance dashboard: Mitigate risks by tracking compliance with the GDPR and ePrivacy Directive across your entire digital portfolio from one place.
- Customer data platform: Segment data to create custom audiences and serve personalized adverts to data subjects.
Cookie Information pricing
- Essential: From EUR 15/month/domain
- Professional: From EUR 34/month/domain
| Free 30-day trial | No geotargeting |
| Robust analytics | |
| Daily and weekly website scans |
Choosing the right compliance management tool
Whether you need to achieve GDPR or CCPA compliance, selecting the right compliance management tool is crucial.
A reliable solution will help you continuously meet the requirements of applicable laws while avoiding the risks associated with noncompliance.
Compliance processes you should consider
The actions your business will need to take in relation to data collection and processing will depend on the jurisdictions where your audiences are located.
Here are a few of the most important regulations to keep in mind, along with their main requirements.
- General Data Protection Regulation (GDPR): Obtain explicit consent for collecting and processing data from users in the EU, no matter where your business is located.
- California Consumer Privacy Act (CCPA): Enforce California users’ right to know what data you’re collecting, as well as the right to delete data and opt out of data sales.
- Virginia Consumer Data Protection Act (VCDPA): Provide data subjects in Virginia with the right to access, correct, and delete data.
- Lei Geral de Proteção de Dados (LGPD): Obtain Brazilian users’ explicit consent for data collection and enforce their rights to access, correct, and delete that information.
- Protection of Personal Information Act (POPIA): Secure South African data subjects’ consent for data processing and provide transparency about data usage.
- Federal Act on Data Protection (FADP): Ensure transparent, lawful, and purpose limited collection and processing of Swiss users’ data.
- Transparency & Consent Framework (TCF v2.2): Provide clear consent management frameworks and ensure that data subjects can easily manage their consent choices.
Factors to consider when choosing a compliance management solution
Compliance management tools make it easier to adhere to multiple data privacy laws simultaneously. The platform you choose should enable you to:
- Obtain explicit, informed consent
- Enable multi-jurisdictional compliance
- Maintain detailed records of consent and data processing activities
- Protect user data from being transferred to unauthorized third-party recipients
- Ensure audit preparedness
Usercentrics CMP is a robust data compliance management solution that enables you to offer your users location-driven and granular consent management options. The platform comes with functionality to streamline compliance processes by reducing the amount of manual input required to increase opt-ins, maintain consented data, and meet rigorous compliance requirements.
In addition to enabling compliance with international regulations and frameworks, Usercentrics is Google-certified and comes integrated with Google Consent Mode v2, so you can continue with digital advertising in the EU, UK, and Switzerland uninterrupted. This helps you to ensure your users can effectively signal and manage their consent in a way that complies with Google’s requirements under the Digital Markets Act (DMA) and the updated EU user consent policy.
Potential compliance risks
Data management and compliance are becoming increasingly important, and not just because of the financial risks that come from falling short of legal requirements.
- Fines and penalties: Most data privacy regulations impose hefty fines on businesses that don’t comply. For example, under the GDPR, businesses can be fined up to EUR 20 million or 4 percent of the global annual turnover, whichever is higher, for repeat or more serious offenses.
- Loss of market share: Consumers are increasingly aware of their data privacy rights and prefer to engage with businesses that prioritize and enforce them. Failure to comply with data privacy laws can reduce customer trust and result in a loss of market share.
- Legal actions: Individuals and groups affected by incidents that flow from noncompliance, such as data breaches, can decide to take legal action against a business under some laws.
- Regulatory scrutiny: Persistent failure to adhere to data privacy regulations or severe violations of these laws may attract increased scrutiny from regulatory bodies. This can result in closer monitoring and more frequent audits and documentation requirements, which may inflate ongoing compliance costs and resource demands.
- Operational disruptions: Audits, investigations, and other adverse events that result from noncompliance can disrupt your business operations, including orders to cease certain operations and/or delete data. This can make it difficult to do business effectively and to grow.
Who should be responsible for compliance operations within an organization?
Data privacy laws affect every department in your organization. From the importance of consent management for digital marketers to compliance-related tasks for human resources and customer service, dedicated compliance officers, like a Data Protection Officer (DPO) or management teams should oversee compliance across the company.
However, if you want to minimize manual effort — and the risk of errors that comes along with it — these individuals shouldn’t be left to manage compliance operations on their own. Equip them with a robust compliance management tool to help teams to stay up to date with evolving laws and business requirements and reduce the complexity involved.
Using compliance management software to consolidate activities and automate tasks can optimize your team’s output and enable your organization to remain proactive while minimizing the risks associated with noncompliance.
Usercentrics CMP for streamlined compliance processes
Failing to comply with data privacy laws can lead to hefty fines, reputational damage, and legal actions that can negatively affect your organization’s bottom line.
When it comes to achieving and maintaining compliance, Usercentrics’ CMP offers dynamic and comprehensive consent management tools that help you adhere to the numerous data privacy regulations in effect across the globe.
By streamlining the collection and management of user consent and making it easier to track regulatory changes, Usercentrics helps businesses in 195 countries to achieve and maintain privacy compliance.
The information presented in this article is provided for educational purposes only. Engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations when evaluating solutions is always recommended. This information is accurate based on these publicly available sources as of the date of publication. Details about products, features, pricing, etc. may change over time.
Global Privacy Control (GPC) is a browser-based privacy tool that standardizes a user’s privacy choices across all websites. It is a type of universal opt-out mechanism (UOOM) or signal.
The GPC’s development is an open initiative that seeks to enable a browser-based global standard for privacy control. It’s been driven by a group of people and organizations — including legal experts, technology professionals, privacy activists and advocates — dedicated to improving privacy online.
The GPC is supported by the Electronic Frontier Foundation and Mozilla and is available through major browsers, including Chrome, Firefox, Brave, and DuckDuckGo, either built in or via a browser extension.
How does the universal opt-out signal work?
A UOOM like the GPC enables people online to signal consent choices to share or refuse access to their personal data for purposes like sale or targeted advertising. The goal is to enable users to select their privacy preferences once and have the tool communicate that decision every subsequent time a user is asked for their consent, typically when visiting websites.
In line with this, the GPC permits automated opt-ins and opt-outs related to cookie use, the sharing or sale of data, targeted advertising, and other online services. The choice can be as basic as refusing all access to one’s personal data, or very granular, with permission for some specific uses and refusal for others.
Although it’s not legally binding in many jurisdictions just yet, to date over half of the state-level privacy laws in the United States require businesses to respect this signal as though it was communicated directly by the user.
What does the Global Privacy Control mean for consumers?
There are a number of benefits that the GPC brings consumers, many of whom experience consent fatigue after a number of years of constant consent requests and being faced with popups everywhere online.
- A simplified, universal way to communicate privacy choices across a variety of online properties.
- More control over their personal data through one-off, granular controls and automated opt-outs.
- Consistency in expressing privacy choices to avoid oversharing data as a result of differences in mood, how busy they are, how many sites they visit on a given day, etc.
- Spreading awareness about and contributing to advocacy for transparent practices, and online data privacy and protection in line with accepted standards and regulations.
What does the Global Privacy Control mean for businesses?
Universal opt-out mechanisms apply to online platforms and services operating in regions where data privacy laws require their use. The signal is not a requirement under the General Data Protection Regulation (GDPR) in the European Union, which has among the world’s most strict data privacy requirements. This is because the GDPR predates the GPC initiative.
The jurisdictions that have adopted the requirement in their privacy laws are currently concentrated in the US, and all within the last four or five years.
However, all businesses that collect and use personal data online need to be aware of the GPC and user consent choices. It’s likely that the use and allowance of UOOMs will be incorporated into major new and updated data privacy laws over time.
Enabling your website visitors to opt in or out using the GPC can streamline your business’s privacy operations. Non-standard data privacy implementations can be a resource drain for businesses. Using this standardized system helps simplify adoption and enable accelerated innovation within the data privacy space.
Recognizing the GPC shows a dedication to data privacy best practices and a commitment to transparency and accountability. This helps to build trust with your customers and gives you a competitive advantage in an increasingly privacy conscious market.
How to implement Global Privacy Control in your business
Understanding GPC is just the beginning. Businesses must actively comply with and properly respond to GPC signals to ensure that they meet legal requirements (where present) while respecting visitors’ choices.
Evaluate which privacy laws apply to your business
Businesses must assess the privacy laws applicable in each jurisdiction in which they operate. This involves identifying relevant regulations, such as the GDPR in Europe or the CCPA in California, and understanding their specific requirements.
As noted, however, employing best practices and respecting the GPC signal even if your audience isn’t protected by a law that requires it is always a good idea. It provides additional protection for your business and demonstrates respect for users’ privacy.
Ensure your consent management platform supports GPC
To ensure that GPC signals are not overlooked, it’s crucial that your consent management platform (CMP) supports these universal opt-out mechanisms. Usercentrics CMP is enabled by default for a variety of regulations that require recognition of an opt-out mechanism, including GPC.
Having a CMP that automatically detects and honors the GPC signal helps reduce consent fatigue for users. It also helps build trust and prevent confusion, since they don’t have to wonder why they’re still being asked for consent choices via a consent banner when they already set up their choices in the GPC tool.
Integrate with GPC signals
Ensuring that your web properties can receive GPC signals is increasingly vital for empowering users in owning their data privacy.
This capability not only enhances user trust but also ensures that your business meets modern privacy standards, and facilitates a transparent and user-centric approach to data management.
Global Privacy Control and international data privacy regulations
| Privacy regulation | GPC obligations |
|---|---|
| Digital Markets Act (EU) | No explicit obligations.
Principles align closely with respect to end-user consent for data processing and do not track requests. |
| General Data Protection Regulation (EU) | No explicit obligations.
Strict GDPR consent requirements can be furthered by GPC signals’ ability to express consent across websites. |
| California Consumer Privacy Act / California Privacy Rights Act | Businesses must respect the “Do Not Sell Or Share My Personal Information” action, which GPC signals can communicate automatically across websites and online services. |
| Virginia Consumer Data Protection Act | Consumers must be allowed to opt out of data processing and sale as well as targeted advertising, which can be effectively communicated through GPC signals. |
| Lei Geral de Proteção de Dados (General Data Protection Law – Brazil) | No explicit obligations.
Consumers must give clear consent to data processing and this could be enabled through GPC signals. |
| Protection of Personal Information Act (South Africa) | No explicit obligations.
GPC can facilitate the fulfillment of POPIA’s requirement for explicit consent regarding the collection and processing of personal information. |
| Federal Act on Data Protection (Switzerland) | No explicit obligation.
Consent must be given for personal data processing; GPC can play a role in managing consent preferences. |
| TCF v2.2 (EU) | No explicit obligation.
TCF 2.2 includes detailed user consent mechanisms that GPC can support to ensure that user consent is respected across digital environments. |
| Google Consent Mode | No explicit obligation.
Integration with GPC will enable the signaling of consent preferences across Google’s extensive digital ecosystem. |
European Union, GDPR, and GPC
The European Union’s GDPR predates the GPC initiative, so the law doesn’t specifically reference the universal opt-out signal.
There are some concerns about whether the GPC can meet some data privacy law requirements, like the one for consent prior to data processing. One sticking point for the GDPR is whether consent can be considered to be informed and explicit if the GPC is used.
Additionally, while GPC is designed to express a generic preference for data privacy, which may align with the right to object (Art. 21, GDPR), there is no explicit endorsement or regulatory guidance from European authorities confirming this applicability.
The interpretation and legal acknowledgment of GPC under the GDPR remain areas of active discussion and are likely to continue to evolve.
United States and state-level laws and GPC
The US has passed 21 state-level privacy laws as of August 2024. However, reference to or requirements regarding the GPC are inconsistent.
The laws in California (California Consumer Privacy Act and California Privacy Rights Act), Colorado, Connecticut, Delaware, Maryland, Minnesota, Montana, Nebraska, New Hampshire, New Jersey, Oregon, and Texas require that businesses respect GPC. On the other hand, the laws in Florida, Indiana, Iowa, Kentucky, Virginia, Nevada, Rhode Island, Tennessee, and Utah do not mention or require it.
California’s Attorney General specifically recommended respecting the GPC, particularly for mobile platforms, early in 2023. It has also been referenced in relation to the CCPA-related penalties against beauty retailer Sephora.
The Oregon Consumer Privacy Act (OCPA), which came into effect on July 1, 2024, mandates that businesses must recognize universal opt-out mechanisms such as GPC for targeted advertising, the sale of personal data, and profiling that produces legal or significant effects on consumers by January 1, 2026.
Delaware’s Digital Personal Data Protection Act (DPDPA) and New Hampshire’s Data Privacy Act (NHDPA) have followed suit, each incorporating provisions that align with the GPC’s objectives to enhance user privacy controls. New Jersey’s Data Privacy Act also supports the use of GPC by mandating compliance with these universal opt-out protocols.
Brazil, the LGPD, and the GPC
Brazil’s Lei Geral de Proteção de Dados (LGPD) does not specifically reference the GPC signal. Like the GDPR, this exclusion is a result of the law having come into effect before the GPC initiative was launched.
As with the GDPR, concerns remain about whether the GPC can meet some data privacy law requirements, for example, those necessitating consent prior to data processing.
However, the LGPD does provide flexibility with regard to consent mechanisms, recognizing different contexts and enabling organizations to adapt their processes accordingly. It emphasizes on the rights of data subjects and aligns in spirit with the objectives of GPC to enhance user control over personal data.
The adoption of GPC within Brazil will depend on how well GPC mechanisms can align with these detailed requirements under the LGPD.
South Africa, POPIA, and the GPC
Like the GDPR and the LGPD, South Africa’s Protection of Personal Information Act (POPIA) came into effect before the GPC initiative was launched and thus does not specifically reference the universal opt-out mechanisms.
The same concerns also exist about whether the GPC can meet some of the data privacy law’s requirements.
POPIA emphasizes that consent must be a voluntary, specific, and informed expression of will. The adequacy of GPC in meeting POPIA’s detailed consent requirements remains under consideration.
TCF v2.2 and the GPC
The Transparency and Consent Framework (TCF) v2.2 and GPC both aim to enhance transparency and user control over personal data collection, processing and usage.
The TCF v2.2 focuses mainly on providing a standardized framework for obtaining and managing user consent in the digital advertising ecosystem, whereas the GPC is meant to establish a universal consent mechanism on websites and online services.
While TCF v2.2 and GPC share common goals, TCF doesn’t explicitly incorporate GPC signals. However, recent changes around data consent mechanisms, including clearer language and more detailed vendor disclosures, aligns with the broader objectives of GPC to simplify and standardize user consent across websites and online services.
As the TCF and GPC evolve, it’s likely that future versions of the TCF might include GPC as part of a broader strategy to unify user privacy controls across different platforms and regulatory environments.
The future of Global Privacy Control
The average online user has become increasingly aware of online privacy and the use of their data, and cares about what happens to it. However, many people are also experiencing consent fatigue from having to make frequent consent choices every time they use a browser.
In this light, a universal opt-out mechanism that enables users to “set it and forget it” makes sense. This aligns with individuals’ desires for less intrusive consent mechanisms but also supports broader compliance efforts with data privacy regulations, despite GPC’s current non-mandatory status in many jurisdictions.
That said, concerns remain about the GPC’s ability to meet stringent consent requirements, like the GDPR’s demand for explicit and informed consent. This ongoing concern may become a strong driver for developments that ensure the GPC better aligns with various global data protection laws.
As technology continues to evolve, so too will universal opt-out request signals. The GPC is likely to become an even more streamlined, user-friendly, and powerful tool to help protect users’ data privacy online.
Although GPC isn’t currently a feature in all data privacy legislation, universal opt-out mechanisms being referenced in some major acts indicates that they are likely to become critical for compliance in the future.
Fortunately, achieving and maintaining compliance with these complex and changing laws is made simple with a robust CMP. Usercentrics is an all-in-one consent management solution that helps businesses manage consents and adapt to evolving frameworks to support a comprehensive approach to data protection.
If you operate an online business, whether via a website, mobile app, or both, your business needs a clear understanding of user consent for their data. As privacy protection laws become increasingly strict, failure to gain proper consent from visitors, customers, and users can lead to both hefty fines and brand distrust.
But there are many different types of consent, all with specific requirements levied by regulatory bodies. Understanding what consent you need and when and how you need to request it can help you build brand loyalty, make better decisions for your business, comply with regulations, and avoid penalties for noncompliance.
Different types of user consent
While there are two main consent models used in privacy regulations around the world, the conditions for valid consent under different data processing circumstances vary more widely. We break down what they are, where they’re relevant, and how to comply with them.
Opt-in vs. opt-out consent
Digital marketers need to obtain valid opt-in consent from users, for functions like subscribing to a newsletter or using their data to personalize ads shown to them. Similarly, users need the option to opt out of data-driven activities, such as unsubscribing from a newsletter or withdrawing from data collection for advertising or analytics.
Along with marketing functions, opt-in and opt-out consent also applies to cookie banners. A consent banner employed for CCPA/CPRA-compliant consent would include an opt-out option, and requires the phrase “Do Not Sell Or Share My Personal Information”. Users can click that link at any time, but companies don’t need to get consent before they start collecting users’ data in most cases. If the user has not explicitly opted out, consent is implied.
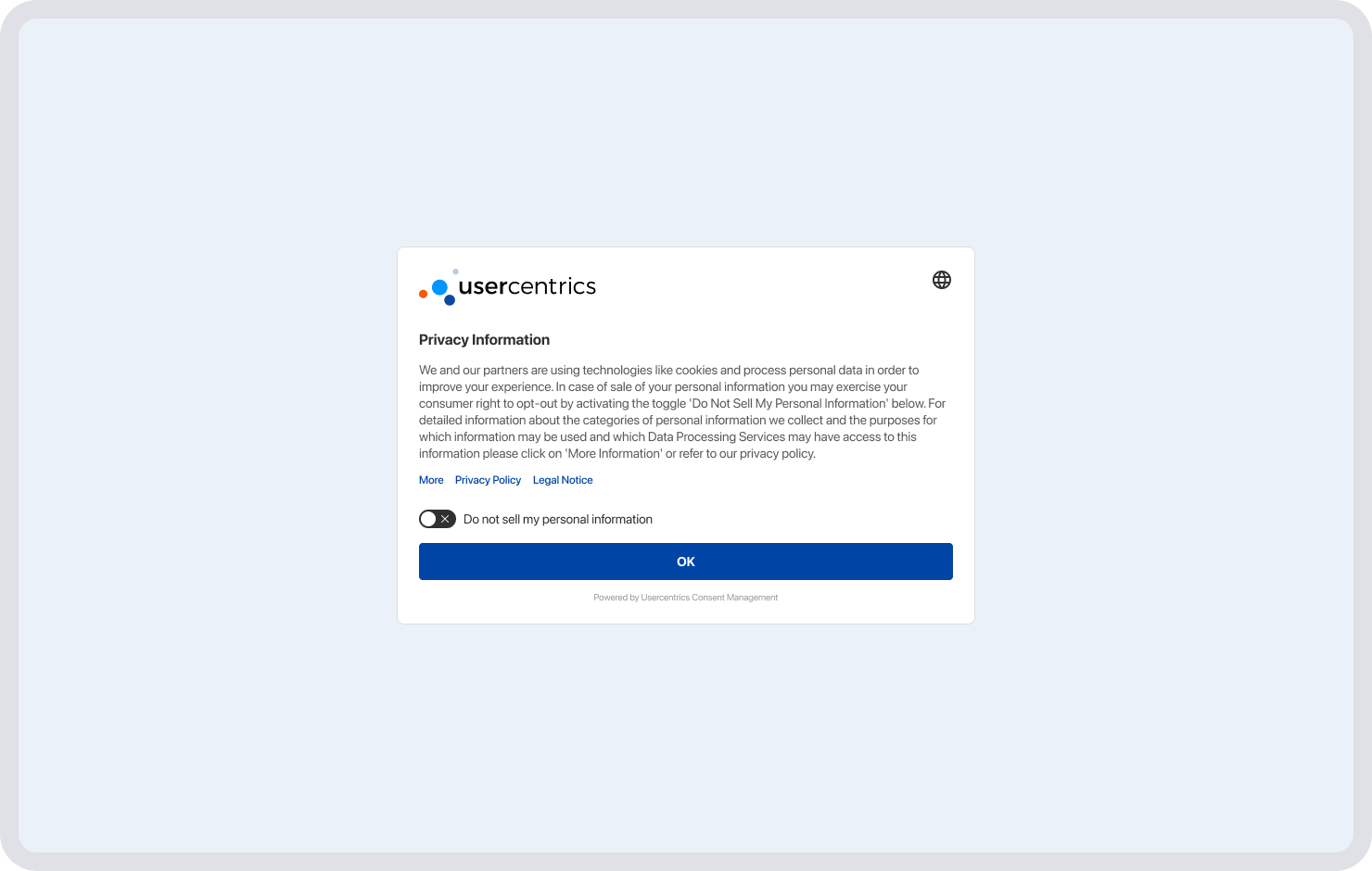
A cookie banner that follows an opt-in model would require users to manually click an “Accept” button or similar explicit action to agree to the data collection practices and purposes communicated. This style of banner is mandatory under GDPR law for consent to be valid.
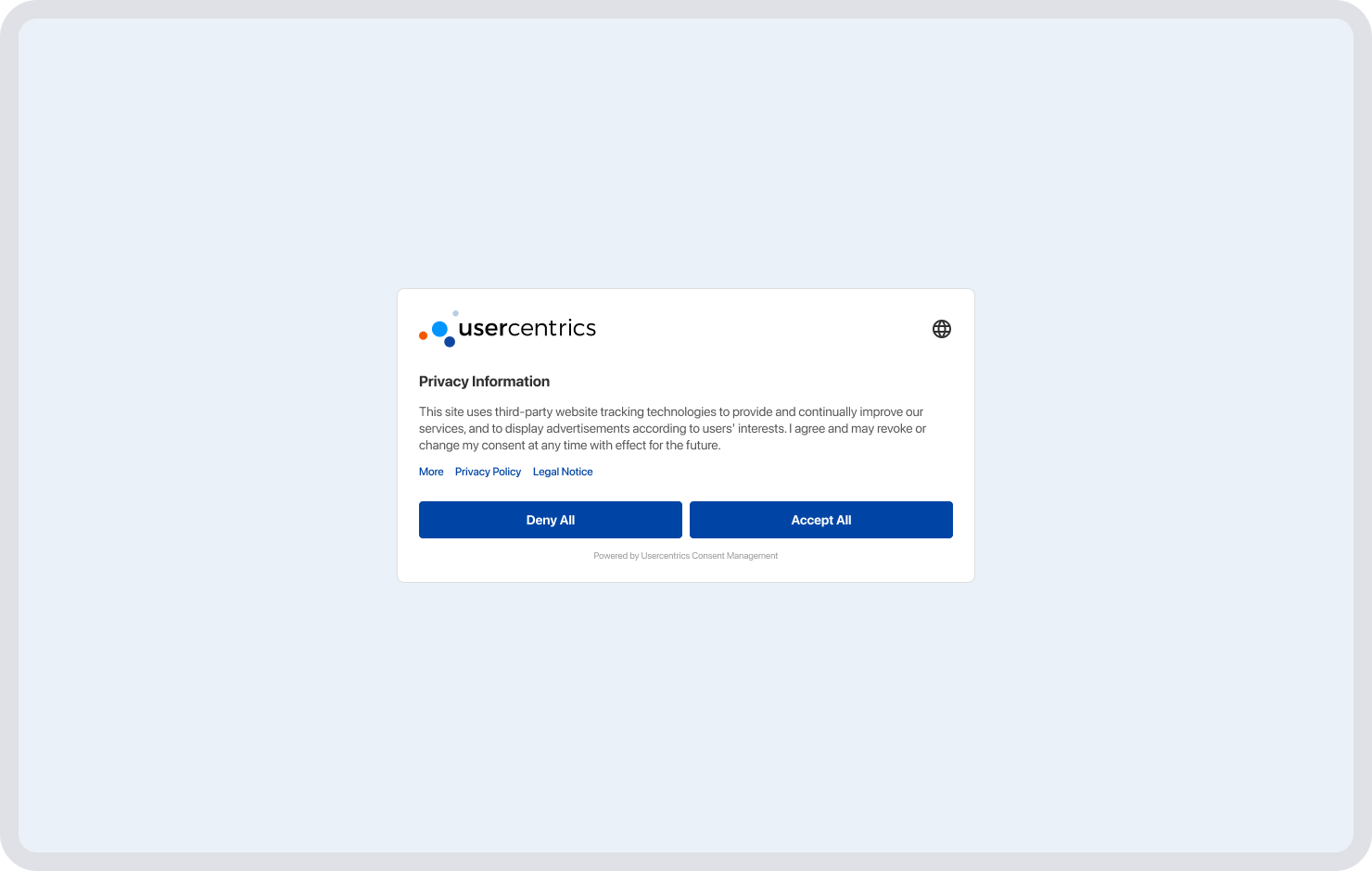
In most cases it is not compliant to prevent users from accessing sites or their features if they decline consent, e.g. with a consent wall that can’t be bypassed, or for them to have a lesser user experience if they don’t consent. Here are tips for creating cookie banners that meet legal requirements.
Informed consent
Informed consent was once predominantly applied in sectors like research, healthcare, and media studies. But it’s becoming increasingly applicable in online data protection and relevant to marketers, especially since the introduction of the General Data Protection Regulation (GDPR) in the European Union.
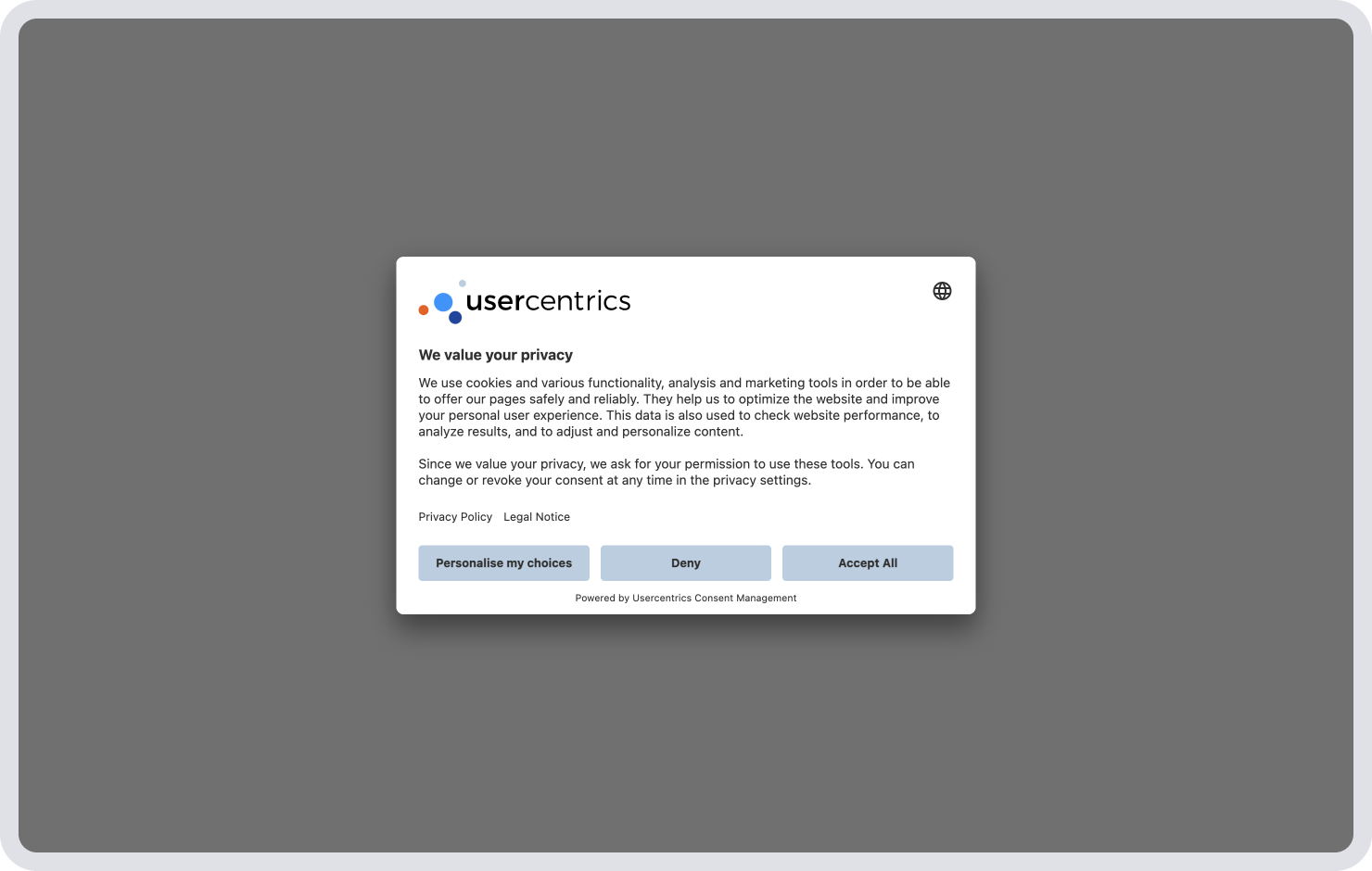
Informed consent requires users to be informed of the details of digital data collection. Regardless of the consent model, all data privacy laws require that data subjects are provided with information about data collection and use and their rights.
- What data is collected, e.g. name, email address, browsing history, location data, etc.
- How the data is used: the purpose(s) for collecting the data should be specific and transparent, e.g., for personalization, targeted advertising, analytics, etc.
- Potential risks and benefits: users should be aware of potential risks, like data breaches or regulated activities, like targeted marketing, and benefits they might receive from consenting, e.g. more personalized communications and offers
- Control over data: users should be able to clearly understand how they can control their information, such as opting out of some or all data collection, accessing their data, or requesting its correction or deletion.
Read about email marketing privacy policy now
Informed consent is especially relevant for businesses that are required to comply with the GDPR. Organizations that fail to obtain proper informed consent in the EU can be heavily fined.
Since then, Google has introduced solutions for data privacy protection with tools like Google Consent Mode and updates to its EU user consent policy.
Explicit consent
Explicit consent is clear and unambiguous on the part of the data subject. With informed consent, the individual knows what their data will be used for and what their rights are. With explicit consent, the user must perform a clear, dedicated action to express their acceptance with the request for access to their data.
Examples of this include:
- Opt-in mechanisms, such as ticking a box or clicking a button that says “I Agree” in a cookie banner.
- Detailed permission requests, such as subscribing to marketing emails (especially with double opt-in) or allowing tracking for a map app.
By using explicit consent, not only are you meeting regulatory requirements, but you’re demonstrating respect for data privacy and building stronger trust with your users.
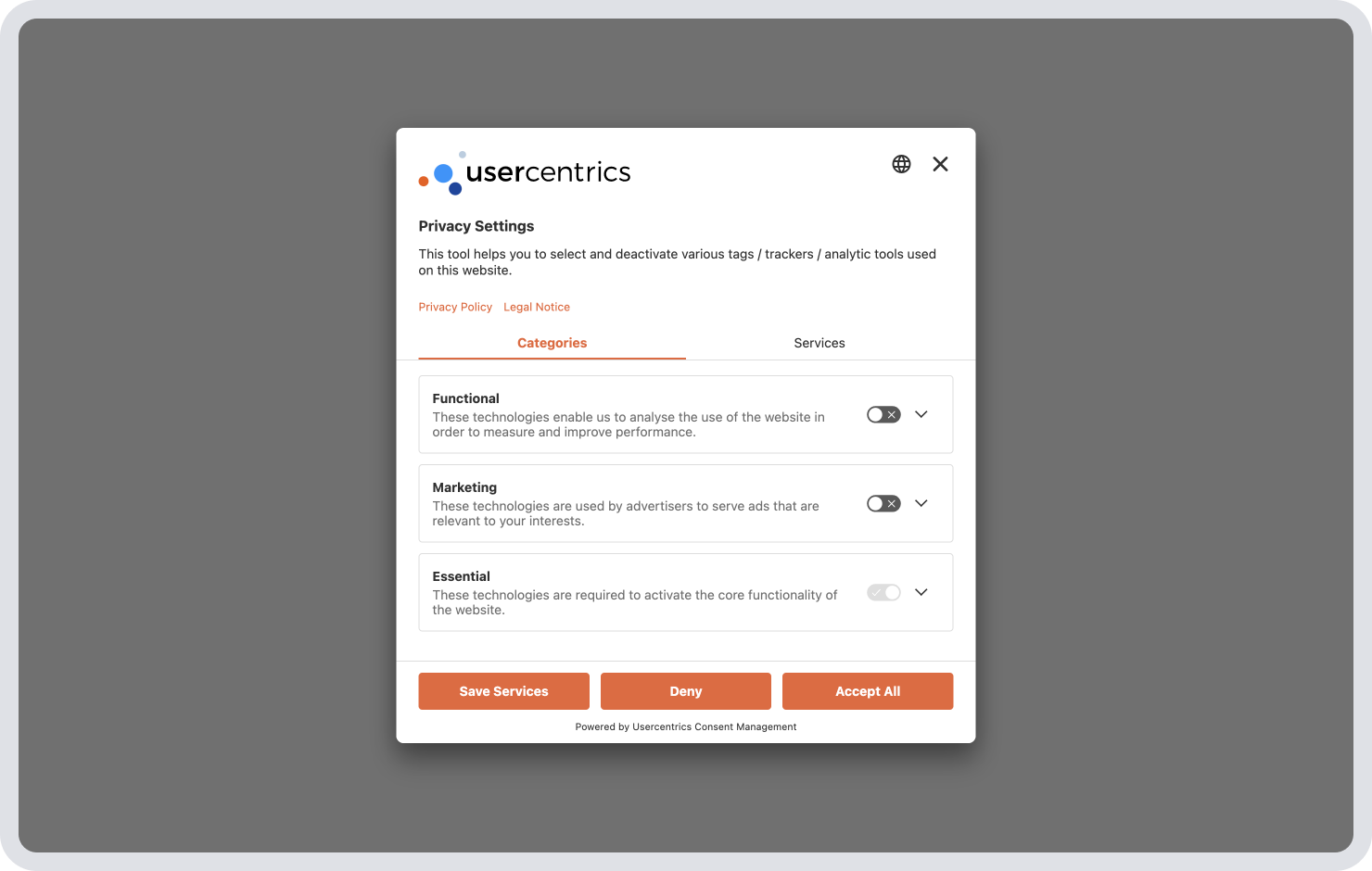
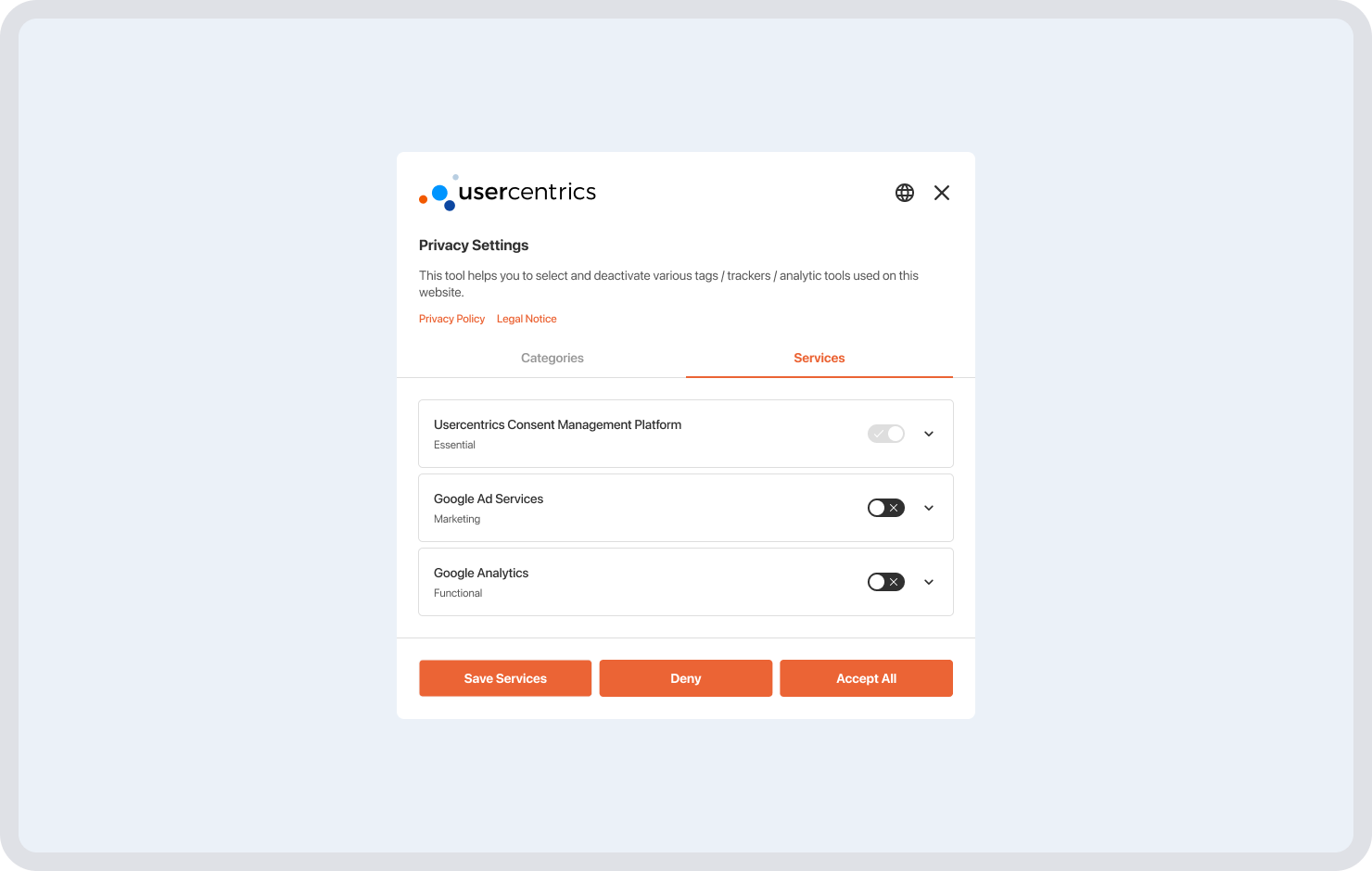
Granular consent
Granular consent involves requesting separate consent for different data processing purposes.
For example, rather than a cookie banner that only gives users the option to “Accept All” for cookies and other trackers in use, website hosts need to offer specific cookie consent options to comply with GDPR, like enabling visitors to say yes to analytics cookies but no to advertising ones, for example.
Users should be presented with clear and user-friendly options to accept or reject data processing, such as banners that allow users to opt-in or opt-out of specific cookies individually, like in the image below.
Implied consent
Unlike explicit consent, implied consent involves assuming consent based on a person’s actions or inactions. An example of this might be a user continuing to browse a website after a cookie banner pops up, and ignoring it. These are sometimes referred to as “browsewrap agreements”.
With a marked shift towards privacy-led marketing and regulatory authorities increasingly prohibiting assuming consent from a user not performing an explicit action, it’s recommended to err on the side of caution against implied consent.
Instead, follow informed and explicit consent best practices, following privacy-led and consent-based marketing principles.
General consent
Unlike granular consent, general consent offers limited control over what data users can agree to or reject.
An example of this could be a general online service agreement where users consent to the Terms of Service, without providing necessary details about the privacy policy and how data is being collected, stored, and processed.
General consent was once fairly commonplace, but it’s becoming increasingly discouraged in favor of granular consent. Consent “bundling” is also not allowed under a number of data privacy laws. Best practices involve separating out different kinds of required information, like in the Terms of Service and privacy policy, as well as having a cookie notice and consent banner for informed and explicit consent management.
Conditional consent
This typically follows a ‘this for that’ approach. Conditional consent can look like companies offering something in exchange for a user’s data. For example, a user accessing a whitepaper or webinar under the condition that the company can send them marketing messages. Or a discount code in exchange for a newsletter signup.
For businesses in the European Union, conditional consent can become convoluted as consent must be “freely given” under the GDPR. This blurs the lines with marketing strategies like gated content. It has generally not been frowned upon to make such offers, but what individuals are giving must be equivalent to what they’re getting, otherwise it looks like a bribe for consent, which is definitely frowned on by data protection authorities.
If you’re considering conditional consent-based marketing, using a consent management platform to follow proper protocol is recommended.
Ongoing and dynamic consent
Ongoing consent, otherwise known as dynamic consent, helps ensure that users have the opportunity to actively manage their data and adjust, update, or withdraw their consent at any point.
Unlike the traditional one-time model of consent, sometimes referred to as a “clickwrap agreement”, a dynamic consent approach is based on a few core factors.
- Continual engagement with users about their preferences.
- Transparency with clear messaging on what is happening with personal data, especially with process updates or changes.
- Options for users to update their preferences, such as the frequency or channels by which they receive messages, as well as information about user rights.
- Preference management tools to offer personalization and encourage zero-party data collection.
Offering dynamic/ongoing consent is a crucial way to build trust with users by improving user experience, and adhering to data privacy laws.
Withdrawable consent
Whether using an opt-in or opt-out consent model, pretty much all data privacy laws require users to be able to withdraw consent at any time, even if their data has been collected and used for some time. Ideally individuals should be able to easily change consent preferences at any time as well, if they don’t want to entirely revoke them. Once the user opts out, data collection and processing must stop as soon as possible, ideally immediately, including processing by third parties working for the main controller.
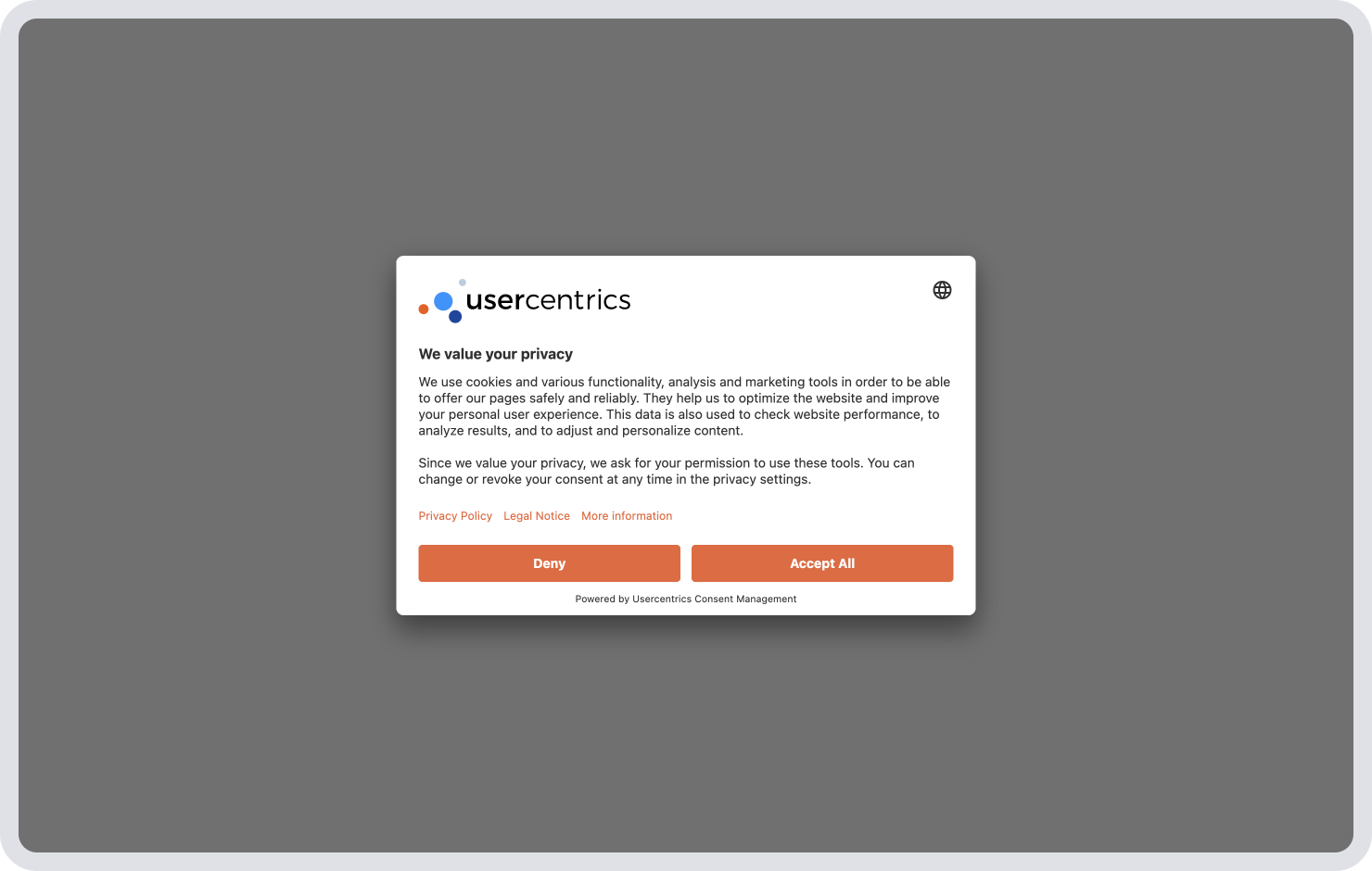
Here are specific features of withdrawable consent:
- The right to withdraw consent at any point, even if they previously agreed to it, which also includes changing consent preferences under some laws
- Accessible, clear, easy to use functionality for users to withdraw, such as opt-out buttons in settings — it’s not compliant to hide this functionality and privacy laws require that withdrawing or declining consent be as easy as giving it
- Once withdrawn, the organization can no longer use the user’s data for its original purposes and collection of data must cease
The right to withdraw consent is, arguably, one of the most important aspects of data protection. Consider a consent management platform to help manage withdrawal functionality accordingly. Many data privacy laws require companies to maintain proof of consent, which includes user actions over time, like accepting, changing, or later withdrawing it.
Consent requirements under global privacy laws
Many of the world’s modern and comprehensive data privacy laws require opt-in consent, among other requirements. While all EU member states are covered by the GDPR, each country has additional consent requirements. The United States is the biggest market where opt-out consent is the norm, though in that country there is not yet a federal law managing privacy requirements, and in the US data privacy is handled state by state.
Consent requirements under the GDPR
When the GDPR came into effect it created a global standard for consent standards in privacy laws. But what, specifically, does the GDPR require around consent? Here are the key requirements.
Consent requirements under the CCPA
The California Consumer Privacy Act (CCPA) and its expansion with the California Privacy Rights Act (CPRA), applies to for-profit organizations that conduct business in California and meet certain criteria.
The CCPA is generally less strict than the GDPR, especially with regards to consent requirements. Still, like the GDPR, failure to adhere to these criteria can result in serious penalties and damage to consumer trust and brand reputation. Here is a high-level checklist of its requirements.
Consent requirements under the LGPD
Another prominent data protection law is Brazil’s Lei Geral de Proteção de Dados (LGPD), which translates to General Data Protection Law in English. The LGPD was influenced heavily by the GDPR, and has actually expanded its coverage beyond the GDPR in some areas. Here are some of the core requirements for consent under the LGPD.
- Opt-in and explicit
- Free, informed, and unambiguous
- Consent must be given in writing for a specified purpose (which includes electronic means)
How to comply with different types of consent requirements: use a Google-certified CMP
Navigating different types of consent can be overwhelming, especially if you conduct business globally where customer expectations vary regionally and when technology and regulation frequently changes.
For example, business requirements are catching up to regulatory ones for consent. Due to Digital Markets Act (DMA) requirements on Google, for example, publishers and developers using Google AdSense, Ad Manager, or AdMob now require a Google-certified Consent Management Platform integrated with the latest version of Google Consent Mode if they want to retain access to all features of Google services, like personalization and retargeting, across the EU/EEA and UK. Google has also expanded their EU user consent policy to include Switzerland.
To ensure that you’re conducting business in these regions while complying with legal and business requirements, choose a Google-certified consent management platform (CMP) like Usercentrics CMP.
From obtaining compliant consent and better engaging customers to staying up to date with evolving regulations, a CMP like Usercentrics’ simplifies the process and helps to ensure you can both achieve and maintain privacy compliance while getting the data your company needs, and building trust and engagement with customers.
As privacy regulations tighten worldwide, businesses must adapt to increasingly complex data landscapes. Third-party cookies, while not entirely phased out, are becoming less effective due to these restrictions. Even with top Consent Management Platforms (CMP) like Usercentrics, obtaining user consent is challenging, complicating attribution and driving up the cost per lead for marketing campaigns. Retargeting, now referred to as Re-engagement by Google, has also become more complex.
To address these challenges, industry leaders like Google are encouraging companies to “bring their own data.” This means businesses should start collecting Zero and First Party data.
Zero-party data, often heralded as the “Holy Grail” of marketing, is information that customers intentionally and proactively share with a brand. This includes data provided through quizzes, surveys, preference centers, and opt-in forms. Because users explicitly state their preferences, zero-party data is highly reliable for creating personalized marketing strategies.
First-party data, also known as customer or proprietary data, is collected directly from your audience through your own channels. This data encompasses information from website analytics, CRM systems, purchase history, and customer feedback. First-party data is invaluable for understanding user behaviors and preferences, providing a solid foundation for targeted marketing efforts. The industry often collectively refers to both Zero and First Party data as First Party data.
Read about first party data marketing now.
Both zero and first-party data are essential as they ensure compliance with data privacy regulations and help build trust with customers by respecting their privacy and preferences. This shift is not just about compliance; it’s about ensuring that your marketing efforts remain effective and relevant in a more privacy-conscious world.
With stricter regulations like GDPR in Europe and the Digital Markets Act (DMA), along with various US data privacy laws, businesses must handle user data with greater care and precision. Tools like Google’s Customer Match and Facebook’s Audience Ad Targeting now require explicit consent, which must be collected at the moment users provide their data and passed programmatically via API to various tools. Failing to properly pass the consent signal can result in non-compliance and significant marketing inefficiencies.
Integrating marketing automation tools with preference management solutions is no longer optional—it’s essential.
Effective integration ensures that user preferences are accurately captured and managed across various platforms, facilitating the creation of targeted and compliant marketing campaigns. By streamlining the collection and use of Zero and First Party data, businesses can craft highly personalized campaigns that resonate with their audience while adhering to privacy standards. This not only enhances customer engagement but also helps avoid potential regulatory issues.
Usercentrics Preference Manager is a key player in this integration process. It simplifies the synchronization of user preferences across different channels and marketing tools, ensuring your data is always accurate and up-to-date. This seamless integration is vital for meeting data privacy requirements and delivering personalized experiences that build trust with your audience. With Usercentrics PMP, managing user preferences and staying compliant becomes much more straightforward, allowing you to focus on what you do best: creating impactful marketing strategies.
In this guide, we explore the benefits of integrating Usercentrics Preference Manager into your martech stack and provide an example of setting up the Mailchimp integration via Zapier.
Benefits of Integrating Your Martech Tools with Usercentrics Preference Manager
-
Flexible and Customizable User Interface
Usercentrics Preference Manager offers a dynamic and adaptable interface that empowers end-users to manage their communication preferences effortlessly across multiple touchpoints, including websites, onboarding processes, and mobile apps. This flexibility goes beyond what is typically available, providing a more tailored and engaging experience for users. By integrating with Mailchimp’s Preference Manager, Usercentrics enhances the overall functionality, offering an intuitive and customizable interface that aligns seamlessly with your brand’s identity and user experience goals.
-
Critical Privacy Layer
Privacy is at the core of Usercentrics Preference Manager. The platform adds a crucial layer of privacy protection by maintaining a comprehensive history log of all user preference changes, ensuring thorough audit trails. This feature is essential for businesses striving to comply with stringent data privacy regulations such as GDPR and CCPA. Furthermore, Usercentrics allows businesses to define data retention periods for valid user preferences, thereby enhancing compliance and reinforcing user trust in how their data is handled.
-
Seamless Integration for Targeted, User-Controlled Email Campaigns
The integration between Usercentrics Preference Manager and Mailchimp is designed to be seamless, enabling businesses to deliver highly targeted and personalized email campaigns. This integration ensures that all marketing efforts are fully controlled by the end user, fostering a sense of trust and transparency. Users can easily update their preferences, and businesses can automatically reflect these changes in their email marketing strategies, resulting in more relevant and engaging communications.
-
Streamlined Workflow
Integrating Usercentrics Preference Manager with Mailchimp not only enhances functionality but also streamlines workflows. This integration eliminates the need for manual data entry and significantly reduces the risk of errors. Marketing teams can rely on accurate, up-to-date user preference data, allowing them to focus on crafting impactful content and strategies. By automating the synchronization of user preferences, businesses can ensure that their marketing campaigns are both effective and compliant, ultimately leading to better customer engagement and satisfaction.
Why Usercentrics Preference Manager?
What sets Usercentrics Preference Manager apart from other preference management platforms? Below are some of the core capabilities that make it the ideal choice for businesses seeking comprehensive preference management, enabling them to create tailored and engaging experiences for their audience.
Granular Preference Capture
Usercentrics Preference Manager excels in capturing user preferences with a high level of detail. This allows you to gather deep insights into what your users are interested in, their preferred content, and how they wish to communicate with you. Such granularity ensures that you can cater to each user’s unique needs, enhancing their experience and your engagement with them.
Customizable Widgets
The platform offers customizable widgets that you can align with your brand’s look and feel. This flexibility ensures that the preference capture process is not only efficient but also seamlessly integrated into your user journey, reflecting your brand’s identity and commitment to user-centric design.
Robust Data Security Measures
In today’s digital landscape, data security is paramount. Usercentrics Preference Manager prioritizes this by implementing stringent security measures. These measures protect user preference data, fostering trust and ensuring compliance with global data privacy regulations. By safeguarding this data, you reinforce your commitment to user privacy and build stronger, trust-based relationships with your customers.
Integration with Popular Platforms
Usercentrics Preference Manager is designed to integrate smoothly with a wide range of popular platforms, making it a versatile addition to your existing tech stack. Whether you’re using marketing automation tools, CRM systems, or other digital marketing solutions, Usercentrics can adapt to fit your needs. This capability ensures that you can effectively manage user preferences across various tools, enhancing your ability to deliver personalized and relevant marketing content.
For instance, integrating Mailchimp via Zapier is straightforward with Usercentrics. This example highlights the ease with which you can transfer user preferences and leverage personalized marketing. By integrating these platforms, you streamline operations and ensure that user data is accurately reflected across all your marketing efforts, making your campaigns more effective and compliant with privacy standards.
Find out how Usercentrics Preference Manager ranks against similar tools: 8 top preference management tools in 2024
Integrating Usercentrics Preference Manager with Mailchimp via Zapier
Integrating Usercentrics Preference Manager with Mailchimp through Zapier simplifies how you manage and utilize user preferences. Follow these steps for a smooth integration:
Step 1: Utilize Webhook Functionality on Usercentrics Preference Manager
Usercentrics Preference Manager offers webhooks, a feature that allows for seamless data transfer between different platforms. Think of webhooks as a way to easily send user preference information to other systems.
Step 2: Capture Webhook Data with Zapier
Set up Zapier to capture the data sent by Usercentrics Preference Manager. Zapier acts as an intermediary, monitoring for new data and ensuring it is processed efficiently. This step helps you catch and manage the data effectively.
Step 3: Update Mailchimp with Processed Data
Use the processed data from Zapier to update or add information in your Mailchimp mailing lists. This step ensures that your email campaigns reflect the latest user preferences, allowing you to tailor your communications more effectively.
Introduction
Consumers are increasingly concerned about how companies collect and use their personal data, and they’re even willing to change their spending habits because of it. Meanwhile, data protection authorities are ramping up enforcement of privacy laws.
This has led to renewed focus on privacy by design, a framework that enables organizations to deliver better and more trusted user experiences long term, achieve and maintain privacy compliance, and ensure the critical flow of data to drive revenue.
First introduced in the 1990s, the concept of privacy by design” gained significant attention with the EU’s key data protection legislation, the GDPR, where it is the basis of Art. 25. The core principle is that privacy should be built into companies’ processes, products, and services at every stage of development, from conception through implementation to usage.
In other words, privacy should be a central consideration right from the design stage, rather than being thought about and added retroactively when companies get worried about privacy compliance.
We explore what privacy by design is, why it’s important, and how you can build its core principles effectively into your business.
What is privacy by design?
Privacy by design is a concept that advocates for user privacy and data protection compliance to be embedded into just about all ways companies function and deliver products and services, including directly into the design specifications of technologies, business practices, and physical infrastructures.
As a framework for privacy protection, it requires thinking about and implementing privacy measures right from the onset of projects that involve the processing of personal data, from planning and design through to deployment, maintenance, and updates.
How is privacy by design implemented?
Building privacy by design into processes like software development seems obvious, but it can be equally important to include it in projects like user persona development. During this process, you should ask yourself questions like:
- Which groups need to be protected?
- What data of theirs will be requested, for what purpose, that needs protecting?
- How can we best minimize the data we need and best secure it in our operations?
- How do our customers view and approach their data privacy?
- What experiences do we want to provide them and how does privacy affect that?
Privacy by design should be integrated into numerous aspects of projects and operations and not limited to website cookie use or designing forms or databases. This helps you achieve better UX and privacy compliance and update rollouts.
Outside of active building, as with software development, privacy by design also needs to be included in day to day operations like customer support, advertising, and partnership building.
Why is privacy by design important?
Privacy by design enables businesses to build data protection practices into product offerings, which is part of what makes it so important. This helps safeguard potentially sensitive user information and helps ensure regulatory compliance in a way that’s streamlined, scalable, and fully aligned with other areas of the business.
Here are six key reasons privacy by design is so important for businesses.
1. App monetization and privacy go hand in hand
More and more, large advertisers will rarely invest in publishers that fail to collect consent strings in accordance with the latest privacy principles. Even programmatic advertising, the most lucrative way to use real-time data, requires consent from end users. Publishers that want access to premium ad inventory need to prove they collect valid consent.
Data privacy is an increasingly relevant topic to app developers, with three key driving factors:
- Regulatory bodies are pushing for stronger regulation in the app industry.
- Premium advertisers increasingly won’t buy inventory where consent hasn’t been collected in a compliant manner.
- App developers and companies are realizing that their current business model isn’t sustainable or scalable without a privacy strategy from the start of application development.
Getting consent without disrupting the user experience (UX) is also crucial. This is particularly important for mobile games and applications developers since these users have smaller screens and tend to be more impatient compared to those using desktop web browsers, for example.
As such, core data privacy features should blend seamlessly with your app’s design and functionality and not negatively affect performance to avoid interfering with UX.
2. Get your project off on the right foot
Design conception is where privacy by design takes center stage. Developers must align data collection to the specific purpose the data is needed for, and then communicate that purpose to mobile app and website users. This helps ensure that data controllers, including joint controllers, implement appropriate technical and organizational measures so that data processing complies with relevant regulations.
Art. 5 GDPR states the principles for lawful processing of personal data:
(i) Lawfulness, fairness, and transparency
(ii) Purpose limitation
(iii) Data minimization
(iv) Accuracy
(v) Storage limitation
(v) Integrity and confidentiality
(vi) Accountability (must be observed in the design and implementation of these systems)
3. It helps you establish a strong brand reputation
81 percent of adults in the US are concerned about how companies use the personal data they collect, according to a 2023 Pew Research report.
According to the Global System for Mobile Communications Association (GSMA), “Even applications that legitimately access and use personal information may fail to meet the privacy expectation of users and undermine their confidence and trust in organizations and the wider mobile ecosystem.”
So what happens when businesses invest in data privacy and users trust that their data is used legally and ethically? The results are clear. In the Cisco 2024 Data Privacy Benchmark Study, 80 percent of businesses reported increased customer loyalty as a result of their investment in privacy.
The return on that investment typically ranged from 60 to 100 percent. In other words, prioritizing transparency and user privacy means higher customer lifetime value (CLV).
4. Liability can be an organizational hurdle
Data privacy liability broadly falls on the company in general, but it can also fall on specific departments. According to the GDPR, if you play a role in determining “the purpose or means” of data processing, you are a joint responsible party (data controller) for the data processed by any third party.
For example, if your website or app has monetization functionality, analytics, or reporting SDKs, you can be held accountable for a lack of sufficient user consent. This makes clear accountability essential for developers.
5. It helps you grow with a global outlook in mind
Online, your customers and users can be located pretty much anywhere. Publishers must ensure global privacy compliance on their websites and/or mobile applications if they collect personal data from users in jurisdictions protected by privacy regulations, which at this point is most of them.
This refers to processing financial transactions, collecting email addresses at account signup, settings cookies, and transmitting data to other apps.
The GDPR applies to websites and mobile apps that collect and process the personal data of EU citizens. It doesn’t matter if your business is based outside of the EU — if you process data from EU residents, the GDPR still applies to you.
Many other global data privacy laws are also extraterritorial in this way, so it’s important to be familiar with the laws of regions where you do business, and to know where your audience and customers are.
6. You likely collect vast amounts of data
If you think you don’t need to develop a privacy strategy simply because your app doesn’t use cookies (or you think it doesn’t), think again.
According to a Trinity College Dublin study, a significant amount of user data is transmitted to third parties without any option to opt-out, largely as a result of pre-installed apps like Google, Facebook, and LinkedIn.
On the positive side, the vast amounts of data gathered can provide a lucrative revenue stream. On the negative side, the information collected by cookies, trackers, and third-party SDKs will gradually become of little to no use if valid consent isn’t collected and signaled to important partners and vendors, especially as global privacy regulations become more stringent.
What are the 7 privacy by design principles?
Privacy by design has seven generally accepted foundational principles. Following them will help you achieve a design that’s enjoyable for the user while prioritizing privacy.
Principle 1: Proactive not reactive; preventative not remedial
Anticipate and prevent privacy-invasive events before they happen. Don’t wait for privacy risks to materialize, and don’t offer remedies for resolving privacy infractions once they’ve occurred. Rather, prevent them from occurring in the first place.
Principle 2: Privacy as the default setting
Deliver the maximum degree of privacy by ensuring that the minimum amount of personal data is collected and that it is automatically protected in any IT system or business practice. An individual’s privacy should be protected even if they do nothing to ensure it, as it’s built into the system by default.
Principle 3: Privacy embedded into design
Embed privacy into the design and architecture of IT systems, website and app functions, and business practices rather than bolting it on after the fact. Make privacy an essential component of the core functionality being delivered, integral to the system without diminishing functionality.
Principle 4: Full functionality — positive-sum, not zero-sum
Accommodate all legitimate interests and objectives in a “win–win” manner. Don’t make unnecessary trade-offs because of dated beliefs or practices. Achieve goals with privacy, not in spite of it. Avoid false dichotomies like privacy vs. security, and demonstrate that it’s possible and desirable to have both.
Principle 5: End-to-end security — full lifecycle protection
Embed privacy long before data is collected, and manage it securely throughout the entire lifecycle of the data. Strong security measures are essential from start to finish, so ensure that all data is securely retained only as long as needed and securely destroyed or anonymized in a timely manner at the end of the process.
Principle 6: Visibility and transparency — keep it open
Assure all stakeholders that all business practices and technology involved operate according to stated objectives and contractual requirements, subject to independent verification. Component parts and operations should be visible and transparent to users and providers alike as much as possible.
Principle 7: Respect for user privacy — keep it user-centric
Architects and operators are required to prioritize the interests of individuals by offering strong privacy defaults, providing appropriate notice, and ensuring user-friendly options are available.
How to implement privacy by design on websites and apps
To implement privacy by design, organizations that collect and process personal data via websites or apps should abide by the following best practices. These recommendations parallel the “principles relating to processing of personal data” in Art. 5 GDPR.
Data minimization
Collect only the personal data that’s necessary for the specific, stated purpose. This helps to reduce the risk and potential harm from unauthorized access in the event of a breach. Users are also more likely to trust organizations that only ask for data that’s necessary to provide the experience, product, or service they offer.
Transparency
Provide clear and easily accessible information about the types of personal data being collected, why it’s being collected, and who will have access to it, among other relevant information.
While some privacy laws don’t require consent prior to personal data collection, such as US-based laws like the California Consumer Privacy Act (CCPA), all of them require you to notify users of relevant information via a privacy policy, consent banner, or combination of solutions.
It’s also necessary to ensure this information is kept up to date — for instance when there are changes in regulations or the technologies your site or app uses. To avoid noncompliance, it’s best to automate these functions with a consent management solution.
Security
Implement appropriate physical, technical, and organizational measures to protect personal data from unauthorized access, theft, modification, or destruction.
After all, it’s safer to prevent violations than to deal with their consequences. Repairing your company’s legal status, finances, and reputation is always much more challenging than preventing security incidents in the first place.
User control
Ensure users can control the collection and use of their personal data, ideally at a granular level. For example, provide options to opt out of data collection or sale and the ability to request corrections or deletion.
Many privacy laws actually require these functions and outline them as consumers’ rights, but it’s better to go beyond the basic legal requirements and put users in control. This can also include going further and asking customers for their preferences so that communications, offers, and data used for personalization, etc. is explicitly provided by them, so of optimal quality and fully consented.
This promotes trust and willingness for your customers to provide more data over the long term. However, ensure you present all options equally to avoid dark patterns or other manipulative practices.
Privacy by default
Build privacy into the design and default settings of your products and services. For example, use privacy-enhancing technologies, such as encryption and pseudonymization by default.
Additionally, consult qualified legal counsel and/or data privacy experts to fully understand your ongoing responsibilities under relevant data privacy laws for the regions where you do business, and what you can do to stay compliant throughout the user and data journey.
Read about privacy-enhancing technologies now
Third-party relationships
Evaluate the privacy practices of third-party service providers, such as analytics and advertising companies, and ensure that appropriate contracts and agreements are in place to protect personal data. Also regularly audit data collection practices as the tools used by third parties and the data they collect change over time.
Under most privacy laws, the data controller — not the processor (e.g. the advertising partner) — is legally responsible for data protection and held liable if there is a violation.
Regular review
Regularly review and assess the current legal landscape of relevant regulations, as well as privacy impacts of products, services, and processes, to ensure that privacy by design remains an ongoing focal point. Audit data operations, employee access, and training competence regularly as well so your people are as secure as your technical systems.
It’s generally best practice to review privacy practices and notifications every six to 12 months, and some laws actually require you to do so.
Using a consent management platform (CMP) enables you to regularly analyze user interactions, scan for the cookies and other trackers in use, and update your data processing information. This helps optimize messaging and UX and ensures users are informed, privacy is protected, and consent rates are maximized.
Privacy by design and marketing
A 2022 Google/Ipsos report found that a positive privacy experience for users increases brand preference by 43 percent. As marketers want to build great customer relationships, adding privacy by design into their strategies and operations is an effective way to do so while still getting the business-critical data they need to run those operations effectively.
Privacy by design can significantly impact marketing operations by shifting data strategies away from third-party data toward more controlled and targeted methods of collecting and using higher quality personal data, such as first-party and zero-party data.
This approach is crucial for popular marketing functions like preference management and server-side tagging, where user consent is vital throughout the data lifecycle.
The GDPR and privacy by design
The GDPR’s requirements are fairly extensive, making privacy a vital consideration in all aspects of process, product, and service design involving personal data. Art. 25 GDPR specifically addresses privacy by design and by default.
According to the GDPR, data controllers are responsible for managing risk and ensuring data protection from development through to daily operations.
US privacy laws and privacy by design
The CCPA and other laws require businesses to implement reasonable security measures to protect personal information and to consider privacy risks when developing and implementing new products and services.
Industry-specific federal laws also address data privacy and security, like the Federal Trade Commission’s Gramm–Leach–Bliley Act, which applies to financial institutions, and the Health Insurance Portability and Accountability Act (HIPAA), which covers healthcare.
There’s not yet a comprehensive federal privacy law in the US that requires privacy by design across all industries, so interpretation and implementation will likely vary for the foreseeable future. However, increased scrutiny and enforcement by data protection agencies may lead to standardization.
How does privacy by design protect data and user privacy?
The core purpose of privacy by design is to protect user data and privacy, while still providing great user experience, with an emphasis that both privacy and security are achievable and desirable.
Privacy by design anticipates and helps prevent data breaches and helps ensure personal information is automatically protected. This approach shifts responsibility for privacy protection away from users and reduces risks.
Transparency remains a central value, as users are kept notified about privacy and data use at all stages and retain control.
Entities that access personal data hold responsibility and liability for their actions and for any third-party entities that access the data. If anything goes wrong, they face a loss of trust, reputational damage, fines, and other penalties — even if they didn’t directly cause the issue.
Privacy by design helps guarantee that data and privacy are protected automatically, as these protections are designed and built into all systems from the start. This helps ensure strong security throughout the entire data lifecycle, eliminating weak points where data privacy measures might otherwise be “bolted on” as an afterthought.
Privacy by design and consent management
Consent management solutions offer a smart and reliable way to implement privacy by design at the point of personal data collection. A tool like Usercentrics CMP enables you to notify users about data collection and its purposes. It also securely records and stores consent preferences, as required by regulations or best practices, and enables seamless signaling of consent information via the Google Consent Mode integration.
This not only helps ensure privacy compliance but also keeps a detailed trail of consent requests, which can be used in the event of regulatory inquiry. These tools also enable users to update or revoke their consent choices at any point in the future.
Usercentrics helps facilitate privacy by design by enabling businesses to gauge, track and control which third-party sites are loading cookies to collect user data. By demonstrating respect for user privacy and consent, our software can help increase trust and user engagement and establish long-term customer relationships. Speak to a Usercentrics expert today.
Organizations collect vast amounts of data from their users, which ranges from personal information to website usage patterns to financial details. This data collection helps improve services, tailor experiences, and drive business growth. However, it can also bring significant risks related to data breaches and unauthorized access to or misuse of personal data.
A Data Protection Impact Assessment (DPIA) helps organizations identify these risks, implement necessary safeguards, and maintain regulatory compliance, specifically with the European Union’s (EU) General Data Protection Regulation (GDPR).
What is a Data Protection Impact Assessment (DPIA) and why is it essential for GDPR compliance?
A Data Protection Impact Assessment (DPIA) is a risk assessment process that helps organizations identify and reduce the risks to personal data they process. It involves examining how personal data is collected, handled, and stored, and ensuring there are adequate measures in place to protect individuals’ privacy and rights as they pertain to that data. Requirements for a DPIA are included in Art. 35 GDPR.
Conducting an effective DPIA enables organizations to detect and address potential problems at an early stage, helping prevent data breaches, avoid legal complications, and protect the organization’s reputation.
Who should implement a DPIA?
The GDPR can require the data controller to carry out a DPIA. A data controller is defined as “the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data.”
While the data controller may appoint third-party data processors to carry out processing activities on its behalf, the responsibility for the DPIA remains with the data controller who is ultimately responsible for GDPR compliance and data security. The data processor should assist the controller in carrying out the DPIA by providing any necessary information, as required by Article 28(3)(f) GDPR.
If a Data Protection Officer (DPO) is appointed under the regulation, the controller must consult with the DPO when carrying out a DPIA. The advice given by the DPO and the decisions made by the controller should be documented within the DPIA.
The DPIA may be carried out by someone outside the organization, but the data controller remains accountable for ensuring that it is completed appropriately.
When is a DPIA required?
A DPIA is required whenever a processing activity, in particular using new technologies, triggers one of the obligations to conduct it under the law. Art. 35 requires a DPIA where data processing activities are “likely to result in a high risk to the rights and freedoms of natural persons.” According to the guidelines issued by the Article 29 Working Party (WP29), the predecessor of the European Data Protection Board (EDPB), these rights and freedoms include the rights to data protection and privacy, and may also include:
- freedom of speech
- freedom of thought
- freedom of movement
- prohibition of discrimination
- right to liberty, conscience, and religion
The GDPR specifically requires controllers to carry out a DPIA when:
- there is a systematic and extensive evaluation of personal aspects of individuals, including profiling and automated decision-making
- sensitive data, or data related to criminal convictions and offenses, is processed on a large scale
- publicly accessible areas are systematically monitored on a large scale
A DPIA may be required in other cases, and the controller must evaluate whether processing activities may result in a high risk to the rights and freedoms of individuals. Some examples from the WP29 and Recital 75 GDPR include cases where the processing:
- involves the use of new technologies
- involves matching or combining datasets from two different processing operations
- involves personal data of vulnerable individuals, including children
- is done to track behavior, location, or movements
- may give rise to significant economic or social disadvantage, including identity theft or fraud, discrimination, or financial loss
- may prevent data subjects from exercising control over their personal data
A DPIA can address either a single processing operation or multiple operations that share similar characteristics in terms of their nature, scope, context, purpose, and risks.
Read about marketing data management now
Exclusions from the DPIA requirements
There are two circumstances when a DPIA is specifically not required under the GDPR:
- when the processing operations fall under a list established by a supervisory authority or Data Protection Authority of an EU member state as not requiring a DPIA
- when the processing has a legal basis in EU law or in the law of the member state that applies to the controller, and that law specifically regulates the processing activity
At what stage should a DPIA be carried out?
A DPIA should be carried out before any type of processing begins that is likely to result in a high risk, ideally during the early planning stages of the project, new feature, or new use case. This early assessment helps identify and manage potential risks even if some processing details are still being finalized.
DPIAs are an ongoing activity, and the controller’s obligation doesn’t end once the initial DPIA has been carried out. If data processing has commenced for specific purposes, but the conditions of processing — such as purpose or type of personal data collected — change significantly and are likely to result in a high risk to individuals’ rights and freedoms, the controller must revisit the DPIA before these new processing conditions are implemented. If a DPIA was not initially required before data processing began but changes in processing conditions make it necessary, then it must be conducted when those new conditions arise.
What are the DPIA requirements under the GDPR?
There are certain minimum regulatory requirements for what a DPIA must include. The key components of a DPIA are:
- systematic description of the processing operations, including the nature, scope, context, and purposes of the processing
- assessment of whether the processing operations are necessary and proportional in relation to the purposes, to evaluate whether the same objectives can be met with less data or through less intrusive means
- identification and assessment of the likelihood and severity of potential risks to data subjects’ rights and freedoms
- measures to address and mitigate the risks, including safeguards and security measures such as encryption, access controls, and regular audits to protect personal data and demonstrate compliance with the GDPR
DPIAs under US law
There is no comprehensive federal data privacy law in the US, and a number of states have enacted laws to protect the personal data — often referred to as “personal information” in some laws — of their residents.
Many of these US state-level data privacy laws require controllers to conduct DPIAs. While there may be some variations among state laws, they are usually required in the following cases:
- processing of personal data for the purposes of:
- targeted advertising
- profiling
- sale of personal data
- processing of sensitive data (which usually includes children’s data)
- processing activities that present a heightened risk of harm to consumers
What constitutes “sensitive data” or “sensitive personal information” may differ across various laws, so controllers must ensure they follow the specific requirements of each applicable law.
States that require these assessments include Colorado, Texas, Maryland, Connecticut, Virginia, Nebraska, Oregon, and Tennessee, among others. California requires a DPIA under the California Privacy Rights Act (CPRA), which amended the California Consumer Privacy Act (CCPA).
DPIA procedure
The GDPR doesn’t specify a procedure for conducting a DPIA, giving controllers the flexibility to approach it in a way that effectively assesses risks and informs data processing decisions. The basic steps to conduct a DPIA are as follows.
1. Identify if a DPIA is required
The first step is to determine whether a DPIA is necessary before data processing activities begin. It may not be immediately clear if a DPIA is necessary, and controllers might realize it partway through the project. In such a case, controllers must ensure the DPIA is completed before they begin any processing activities or begin collecting data.
2. Consult the DPO, if appointed
Art. 35(2) of the GDPR makes it mandatory to consult the DPO if the organization has appointed one. The DPO’s advice must be documented in the DPIA and, if the advice is overruled, the DPIA must explain why.
3. Identify all parties to be consulted
Controllers must list all internal and external stakeholders to be consulted. This includes data processors and data subjects or their representatives. The DPIA must include their feedback on the processing activities and, if feedback is disregarded, why.
4. Document the nature, scope, context, and purposes of the data processing
Controllers should list all the data processing activities, including why and how the data is being processed. This should cover, among other things:
- what types of personal data are being collected and processed, including whether the data is sensitive, the volume of data, and how long it will be retained
- the source of the data, and whether it will be shared with any third parties
- how much control data subjects will have over the data, and whether any new technologies will be used in processing
- the intended effect on data subjects and benefits for the controller
5. Assess the necessity and proportionality
The GDPR requires controllers to evaluate whether the data processing is necessary and proportional to achieve the intended purposes, including determining the lawful basis for processing. Controllers should consider what information will be shared with data subjects in their privacy policy, how to achieve data minimization and data quality, and how international transfers will be handled.
6. Identify and assess potential risks
Controllers are required to identify and evaluate the potential risks to data subjects’ rights and freedoms, and outline measures to mitigate these risks. They must assess the likelihood and severity of each risk, considering factors like the nature of the data, the context of processing, and the potential impact on individuals. Controllers should develop a risk mitigation plan that includes specific measures such as encryption, anonymization, access controls, and regular security audits.
7. Validate and sign the DPIA
Controllers must validate and sign the DPIA once it is completed. This involves recording who approved the protection measures and any residual risks. Documenting the decision-making process and identifying those responsible for its implementation and authorization provides a clear record of the approval process.
There is no official template from the EDPB, and controllers that need structure or guidance to get started may use templates from Data Protection Authorities such as France’s National Commission on Informatics and Liberty (CNIL) or the UK’s Information Commissioner’s Office. Although the EU GDPR doesn’t apply to the UK post-Brexit, the UK GDPR is nearly identical to the EU version and includes the same provisions for DPIA requirements.
Conclusion and next steps
Conducting a DPIA is a vital practice for safeguarding personal data, maintaining data subjects’ trust, and avoiding reputational damage. By conducting a DPIA, organizations can identify and mitigate potential risks, ensuring that data processing activities are both secure and compliant.
Organizations should consult a qualified legal professional, privacy expert, or DPO to ensure compliance with the GDPR’s DPIA requirements and to implement the necessary safeguards effectively.
Safeguarding personal information online has become more critical than ever as data privacy laws expand and consumers’ expectations grow. One of the most effective strategies for protecting data is through data minimization.
This principle, enshrined in various data protection and privacy laws like the General Data Protection Regulation (GDPR) and the California Privacy Rights Act (CPRA), emphasizes the importance of collecting, processing, and storing only the minimum amount of personal data necessary for a specific purpose, and retaining it only as long as needed to fulfill the stated purpose.
But what exactly is data minimization, how does it work, and how can your company implement measures to limit its data collection in beneficial ways? Let’s delve into it.
What is data minimization?
Data minimization is a fundamental principle in data protection and privacy laws like the General Data Protection Regulation (GDPR).
Data minimization refers to collecting, processing, and storing only the minimum amount of personal information necessary for a specific purpose, and retaining it only as long as needed to fulfill that purpose.
This approach aims to reduce risks associated with companies’ potential privacy overreach, data breaches, and other misuse while helping to ensure compliance with various data protection regulations. It also shows respect for customers by demonstrably limiting data collection and use to only what’s needed, communicated, and consented to.
Organizations implementing data minimization strategies only collect relevant data and retain it for the shortest time possible. They also regularly review, delete, or anonymize unnecessary information.
By adhering to this principle, companies can better protect individual privacy, enhance data security, improve data management efficiency, meet legal requirements, and improve customer experience.
Read about marketing data management now
Data minimization and GDPR
Data minimization is a key principle of the GDPR. It requires organizations to collect and process only the personal data that is necessary for their specified purposes. It explicitly addresses data minimization in Article 5(1)(c) GDPR, which states that personal data shall be: “adequate, relevant and limited to what is necessary in relation to the purposes for which they are processed (‘data minimization’).”
This principle is further reinforced by Article 25 GDPR, which requires that data minimization be applied by default to each specific purpose of data processing. These articles mean that website owners and businesses must identify the minimum amount of personal data required to fulfill their purpose and collect and hold only that information.
To comply with data minimization requirements, organizations should regularly review their data collection mechanisms, like website cookies, what data they collect, and for what purposes. Then they should also review what data they currently store and use, and if the purposes for which the data was collected are still valid. Finally, they should delete or anonymize data that is no longer needed.
By adhering to this principle, organizations can demonstrate accountability and reduce their risk of noncompliance with the GDPR.
Data minimization and CPRA
The California Privacy Rights Act (CPRA) also introduces data minimization as a key principle for businesses handling consumer personal information.
Under the CPRA, businesses are required to collect, use, retain, and share personal information only to the reasonably necessary extent and proportionate to achieve the specific purposes for which it was collected or processed.
Therefore, businesses must clearly define and disclose the purposes for data collection and ensure that the data is not used beyond these purposes without additional consumer notification and consent where required. In addition, the law requires businesses to implement data retention schedules and delete or anonymize (depending on the law or relevant policies) personal information once it is no longer necessary for disclosed processing purposes.
What is an example of data minimization?
Data minimization doesn’t have to be a complicated affair. For example, let’s look at data minimization in action in the context of an ecommerce website’s checkout process.
Instead of collecting extensive personal information from customers, the website could request only the necessary details for completing the transaction and shipping the product. This might include the customer’s email address, to send a receipt and order confirmation; name and shipping address, to send the order; and payment information. The company also receives various data just as part of the ordering process, like that from website cookies that track the customer’s shopping process, and order specifics like which product, size, and color.
In this example, there is no real need to ask for additional data, such as the customer’s date of birth, gender, or occupation, which are not essential for processing the order, even if these details would provide the company with more demographic information about the customer.
By limiting data collection to only what is required, the ecommerce site reduces its data liability and enhances customer privacy, while still effectively fulfilling its primary function of selling and delivering products.
Read about GDPR email marketing now
Benefits of data minimization
Many website owners and companies prefer to collect a lot of data. After all, more data helps you understand your target audience and optimize marketing campaigns. However, this is a poor practice in the age of digital privacy.
While privacy laws like the GDPR and CPRA require businesses to implement data minimization practices, the benefits go beyond regulatory compliance. Additional benefits of data minimization include:
- Reduced costs: Collecting and storing only necessary data significantly lowers storage and management expenses.
- Enhanced security: Collecting less data reduces the potential impact of breaches and theft, leaving less potentially sensitive information at risk.
- Efficient data management: With less data to process, analyze, and prune, organizations can manage their information more effectively, improving operational efficiency.
- Better data quality: Focusing on relevant and necessary data improves the overall quality and accuracy of datasets.
- Reduced risk profile: Minimizing data collection and storage decreases an organization’s risk related to data access and handling.
- Enhanced customer trust: Data minimization shows a commitment to protecting customer privacy, boosting consumer confidence.
- Simplified data governance: Fewer data assets make it easier to implement and maintain effective data governance.
- Faster data processing: Smaller data volumes allow for quicker analysis and decision-making.
The principles of data minimization
Data minimization is a key principle of data privacy regulation, along with closely related ones like maintaining accuracy and purpose limitation. It’s meant to guide organizations in collecting, processing, and storing personal data to fulfill specific purposes, from ecommerce sales to marketing campaigns to product development.
Here are key principles that website owners should follow to reduce their privacy noncompliance risk.
- Clearly define the specific purpose(s) for data collection and use before any personal data is collected. This will inform what data is needed to fulfill the purpose.
- Only collect data that is directly relevant and necessary for a specific purpose. Be extra vigilant if any of the data is typically categorized as “sensitive” or belongs to children, as this often requires additional consent and safeguards.
- Do not repurpose data without necessary notification, justification, and updated consent.
- Collect enough data to fulfill the stated purpose without exceeding what is required.
- Keep personal data only as long as necessary to achieve the specified purpose. Establish and follow data retention policies to delete or anonymize data when it is no longer needed.
- Embed data minimization into the design of systems and processes from the start to ensure privacy protection is built in.
- When possible, anonymize personal data to reduce the risk of identifying individuals, especially for long-term retention or secondary uses.
- Regularly review data collection, processing, and holdings to determine if they remain relevant, or need to be updated or deprecated.
By following these principles, website owners can reduce privacy risks, enhance data security, improve regulatory compliance, roll out more precise marketing initiatives, and build trust with their customers.
Read about Big data marketing now
Data minimization and risk mitigation
Data minimization is a powerful strategy for reducing risks when handling personal information.
By collecting and keeping only essential personal data and cookies, website owners can significantly lessen the impact of potential breaches. This approach simplifies data protection efforts, as there’s less information to safeguard.
From a legal perspective, holding less data means fewer chances of violating privacy laws. This is particularly important given strict regulations like the GDPR. Data minimization brings companies one step closer to complying with these laws, avoiding hefty fines, reputational damage, and legal complications.
There’s also a financial advantage to this approach. Storing and managing large amounts of information can be costly, from both a financial and resource perspective. By cutting down on unnecessary data, companies can save on storage and processing expenses. Not to mention the work of maintaining or expunging it, or finding all of it to fulfill a data subject access request, for example.
In the event of a data issue, having less information to sort through enables quicker response times and a higher likelihood of accuracy. This rapid action can help limit damage and preserve customer trust.
Moreover, data minimization demonstrates respect for customer privacy. By only requesting and retaining necessary information, businesses can build stronger, more trusting relationships with their clients. This practice not only protects the company but also enhances its reputation in an increasingly privacy-conscious market.
How to implement data minimization measures
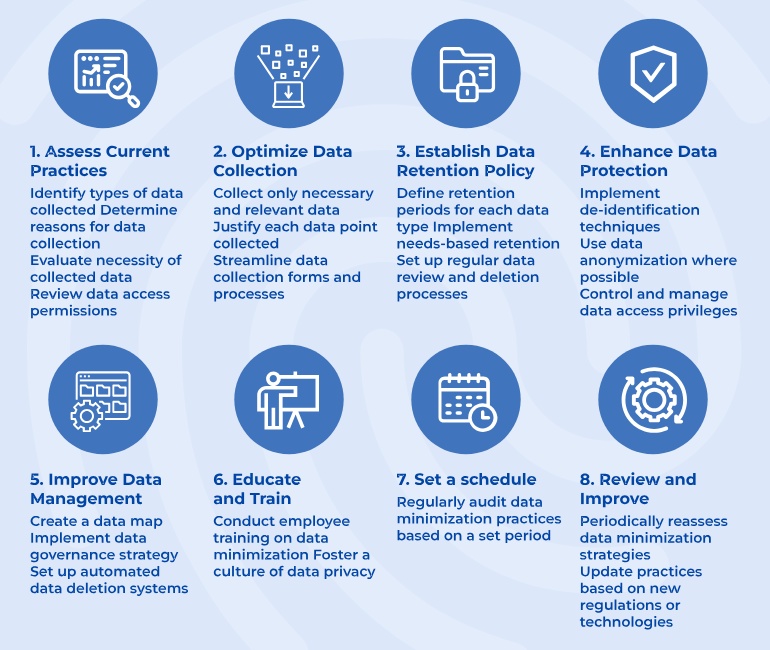
Data minimization may sound simple, but in practice, companies must consider how they collect, use, store, and dispose of customer data. In addition to being prepared to do the work to update policies, processes, and the management of the data itself.
Thus, if your company is considering implementing a data minimization policy, there are certain steps you need to follow.
- Assess your current data practices: Evaluate how your organization currently collects, retains, and manages access to personally identifiable information. This involves:
- identifying what types of data are being collected
- determining how long the organization has had the data
- determining why each piece of data is being collected
- evaluating if the collected data is necessary for the stated purpose
- reviewing who has access to data (e.g. third-party vendors) and what they may be doing with it
- review where data is stored (e.g. in various departments) and who has access
- Implement proportional data collection: Only collect data that is proportional and relevant to the purposes for which you are collecting it. Justify why you collect, process, or store consumer data and ensure these purposes align with your current business and data privacy objectives.
- Establish needs-based retention: Develop a strict data retention policy that ensures your business only retains data needed for specific purposes and only for as long as necessary. Once these purposes are met or the required retention period has passed, the data should be deleted.
- Use data anonymization techniques: When possible, anonymize data to protect individual privacy while still allowing for necessary data processing.
- Control data access: Implement a system that enables secure management of data access privileges across your organization. This ensures that only specific applications or individuals have access to the data fields required for their business processes.
- Regularly review data and delete unnecessary information: Establish procedures to periodically review the data your organization processes and the purposes for it, and remove anything that is no longer necessary to fulfill its original purpose. Consider implementing an automated solution that deletes certain data at predefined intervals.
- Define data retention schedules: Set specific retention periods for each type of data your website and company processes. This should be part of your overall data map and governance strategy.
- Streamline data collection processes: Review your data collection methods and forms to ensure you’re only asking for essential information. For example, if you only need a customer’s email for communication, don’t ask for their phone number or physical address.
By following these steps, website owners can effectively implement data minimization, enhance protection, reduce risks, and build customer trust.
Collect less to build consumer trust
Data minimization is not just a regulatory requirement, but a fundamental practice that can transform how organizations handle personal information.
By collecting only what is necessary, website owners can visibly demonstrate dedication to data security, user privacy, and respect for users’ rights under privacy regulations. The principles of data minimization, as outlined in regulations like GDPR and CPRA, offer a clear framework for organizations to follow, helping companies achieve and maintain compliance.
As digital privacy concerns continue to grow, adopting data minimization practices will be crucial for any organization aiming to maintain its reputation and safeguard its stakeholders’ information.
On April 4, 2024, Kentucky became the fifteenth state in the United States to enact a consumer privacy bill with the passing of House Bill 15, the Kentucky Consumer Data Protection Act (KCDPA). The law goes into effect on January 1, 2026 and gives organizations close to two years to prepare for compliance.
We look at the KCDPA, who it applies to, how it protects consumers, and how organizations can prepare for compliance.
What is the Kentucky Consumer Data Protection Act?
The Kentucky Consumer Data Protection Act (KCDPA) aims to protect the privacy and personal data of the state’s 4.5 million residents by regulating how it is collected and used. It sets obligations on businesses that operate in Kentucky or produce products or services consumed by its residents and process their personal data.
The KCDPA protects the personal data of residents acting in “an individual context” and not for commercial or employment purposes and defines them as “consumers”.
Like most other US states with consumer privacy laws, Kentucky follows an opt-out consent model. Businesses must clearly explain to consumers:
- what personal data they collect
- why they collect it
- third parties they share it with
- how consumers can opt out of its collection and processing for certain purposes
Definitions under the Kentucky Consumer Data Protection Act
The KCDPA defines key terms concerning the data it protects and data processing activities.
Personal data under the KCDPA
The Kentucky privacy law defines personal data as “any information that is linked or reasonably linkable to an identified or identifiable natural person.” The definition specifically excludes de-identified data or publicly available information.
Common types of personal data that businesses collect include name, phone number, email address, account name, IP address, passport number, or driver’s license number.
Sensitive data under the KCDPA
Sensitive data under Kentucky’s privacy law is personal data that could harm consumers if abused and includes:
- racial or ethnic origin
- religious beliefs
- mental or physical health diagnosis
- sexual orientation
- citizenship or immigration status
- genetic or biometric data processed for the purpose of uniquely identifying a specific natural person
- personal data collected from a known child (under 13 years of age)
- precise geolocation data that can accurately identify an individual’s specific location within a radius of 1,750 feet (533.4 meters)
Consent under the KCDPA
The Kentucky data privacy law defines consent as “a clear affirmative act signifying a consumer’s freely given, specific, informed, and unambiguous agreement to process personal data relating to the consumer.”
Consent may include a written statement, including a statement written by electronic means, or any other unambiguous affirmative action.
Controller under the KCDPA
A controller under the law is “a natural or legal person that, alone or jointly with others, determines the purpose and means of processing personal data.“
A controller, often referred to as a “data controller” in some regulations, is responsible for protecting personal data and must comply with the legal requirements for data protection.
Processor under the KCDPA
A controller may share personal data it collects with a third party for processing purposes. This third-party is known as a processor under the Kentucky privacy law and is defined as “a natural or legal entity that processes personal data on behalf of a controller.”
Sale of personal data under the KCDPA
The Kentucky privacy law defines sale of personal data as “the exchange of personal data for monetary consideration by the controller to a third party.“
Sale does not include disclosure of personal data:
- to a processor that processes the personal data on the controller’s behalf
- to a third party for the purposes of providing a product or service the consumer has requested
- or its transfer:
- to the controller’s affiliate
- to a third party as an asset that is part of a proposed or actual merger, acquisition, bankruptcy, or other transaction
- that the consumer intentionally made available to the public through a mass media channel not restricted to a specific audience
Many other US state-level privacy laws define sale as the exchange of personal data “for monetary or other valuable consideration” by the controller or third party. The KCDPA, like the Virginia Consumer Data Protection Act (VCDPA) and the Utah Consumer Privacy Act (UCPA), requires monetary consideration for the exchange of personal data to be considered sale.
Non-monetary consideration does not constitute sale under the Kentucky privacy law.
Targeted advertising under the KCDPA
The KCDPA defines targeted advertising as “displaying advertisements to a consumer where the advertisement is selected based on personal data obtained or inferred from that consumer’s activities over time and across nonaffiliated websites or online applications to predict that consumer’s preferences or interests.”
The definition excludes:
- ads based on activities within a controller’s own websites or online apps
- ads based on the context of a consumer’s current search query, visit to the website, or online app
- ads directed to a consumer in response to the consumer’s request for information or feedback
- processing of personal data solely for measuring or reporting ad performance, reach, or frequency
Who must comply with the Kentucky Consumer Data Protection Act
The Kentucky privacy law applies to businesses that operate in the Commonwealth of Kentucky or produce products or services aimed at its residents and which, during a calendar year:
- controlled or processed the personal data of at least 100,000 consumers
or
- controlled or processed the personal data of at least 25,000 consumers and derived more than 50 percent of gross revenue from the sale of personal data
Unlike some other US state laws, including the California Consumer Privacy Act (CCPA) / California Privacy Rights Act (CPRA), the KCDPA does not require businesses to comply based on revenue alone.
Exemptions to compliance with the Kentucky Consumer Data Protection Act
The Kentucky data privacy law exempts certain entities and types of data from compliance. Entity-level exemptions include, among others:
- city or state agencies or state political subdivisions
- financial institutions or affiliates subject to the Gramm-Leach-Bliley Act (GLBA)
- covered entities or business associates governed by the Health Insurance Portability and Accountability Act (HIPAA)
- nonprofit organizations, including nonprofit controllers that process personal data solely to help:
- law enforcement agencies investigating suspected insurance-related crimes or fraud
- first responders dealing with catastrophic events
- higher education institutions
- small telephone utilities
Data-level exemptions include, among others:
- protected healthcare-related information, health data, and patient identifying information
- data processed or maintained as emergency contact information for a natural person and used for emergency contact purposes
- data created for or collected under several federal laws, including, among others:
- Health Care Quality Improvement Act
- Patient Safety and Quality Improvement Act
- HIPAA
- Fair Credit Reporting Act (FCRA)
- Combat Methamphetamine Epidemic Act
- Family Educational Rights and Privacy Act (FERPA)
- Farm Credit Act (FCA)
Consumer rights under the Kentucky Consumer Data Protection Act
Consumers have several rights under the Kentucky privacy law to protect their personal data.
- Right to access: consumers can confirm whether or not the controller is processing their personal data and can access their data, unless doing either requires the controller to reveal trade secrets
- Right to correction: consumers can have inaccuracies in their personal data corrected, taking into account the nature of the personal data and purposes of processing
- Right to deletion: consumers can request controllers to delete any personal data provided by, or obtained about, them, with exceptions
- Right to data portability: consumers can obtain a copy of their personal data that they previously provided to the controller, in a ready usable format, with some exceptions
- Right to opt out: consumers can opt out of the processing of their personal data for the purposes of its sale, use in targeted advertising, or profiling in furtherance of “decisions that produce legal or similarly significant effects” concerning them
There is no private right of action — or right to directly sue a controller — under the KCDPA.
Controllers’ obligations under the Kentucky Consumer Data Protection Act
Organizations subject to KCDPA compliance have several obligations under the law to protect consumers’ personal data.
Privacy policy under the KCDPA
Controllers must publish a privacy notice, or, similarly, privacy policy, that informs consumers about:
- categories of personal data the controller processes
- purpose(s) for processing personal data
- method of exercising their rights under the law and how to appeal the controller’s decision regarding a request
- categories of personal data shared with third parties, if any
- categories of third parties who receive personal data, if any
Controllers must clearly inform consumers if they sell personal data to third parties or process it for targeted advertising purposes. Unlike the CCPA, Florida Digital Bill of Rights (FDBR), and Texas Data Privacy and Security Act (TDPSA), the Kentucky privacy law doesn’t require any specific wording to be used to disclose this information. Controllers must also advise consumers how they can opt out of sale or processing for targeted advertising.
The privacy notice must be accessible, clear, and meaningful. It is usually published through a link on the controller’s website, like in the footer, to ensure that consumers can access it from any page.
Consumer rights requests under the KCDPA
Controllers must provide one or more secure and reliable methods for consumers to exercise their rights. Consumers may be asked to log in to an existing account for identity verification, but they can’t be required to create a new account solely for this purpose.
Controllers have 45 days to respond to consumer requests, with the option to extend this period by another 45 days if reasonably necessary. If they need an extension, the controller must inform the consumer before the initial 45-day period expires.
If the controller is unable to reasonably verify the consumer’s identity, they may request additional verification or decline the request. In cases where a request is declined, the controller must notify the consumer within 45 days of receiving the request, providing the reason for the denial and information on how to appeal the decision. Controllers must respond to appeals within 60 days. If an appeal is denied, the controller must provide the consumer a method to contact the Attorney General online to submit a complaint.
Purpose limitation under the KCDPA
Controllers are required to disclose the purpose(s) for which they collect personal data, and the KCDPA requires them to limit the personal data they collect to only what is “adequate, relevant, and reasonably necessary” for the purposes.
Controllers cannot process personal data for any purposes other than those that are disclosed to consumers. If the purpose of data processing changes, they must inform consumers about the new purpose and obtain consent for processing their data, if applicable.
Data security under the KCDPA
Controllers must ensure the confidentiality, integrity, and accessibility of the personal data they collect and process. The Kentucky data privacy law requires them to establish, implement, and maintain reasonable administrative, technical, and physical security measures that are appropriate to the volume and nature of the personal data.
Data protection assessments under the KCDPA
The Kentucky privacy law requires controllers to conduct and document a data protection impact assessment (DPIA) when processing personal data:
- for the purpose of targeted advertising
- for sale
- for the purpose of profiling that presents a reasonably foreseeable risk of:
- unfair or deceptive treatment of or disparate impact on consumers
- financial, physical, or reputational injury
- physical or other intrusion into consumers’ private affairs
- other substantial injury to consumers
- that is classified as sensitive data under the law, including childrens’ data
- presents a heightened risk of harm to consumers
DPIAs are classified information under the law and are exempt from disclosure, public inspection, and copying. However, the Attorney General can request the controller to disclose a DPIA during its investigations into any alleged violations, and the controller must make it available in this circumstance.
If a controller has already conducted a DPIA for other laws or regulations, and it is similar in scope and effect to what is required under the law, the controller can use that DPIA to comply with the KCDPA.
DPIAs shall be required for data processing activities on or after June 1, 2026.
Consent requirements under the KCDPA
The KCDPA primarily follows an opt-out model for personal data processing, like the other US state-level data privacy laws. This means that, in most cases, businesses can collect and process personal data without needing prior consumer consent. An exception to this is processing that involves sensitive data, and controllers must obtain explicit consent before its processing.
Controllers are required to clearly inform consumers about their data processing activities and provide options for consumers to opt out of the sale of their personal data and its use for targeted advertising or profiling.
Unlike several other privacy laws, the Kentucky privacy law does not require controllers to recognize consumer consent preferences communicated through a universal opt-out mechanism such as Global Privacy Control (GPC).
With respect to children’s data, the KCDPA aligns with the Children’s Online Privacy Protection Act (COPPA), as is standard among the US data privacy laws. This requires controllers to obtain consent from a parent or guardian before processing any personal data of children under 13 years old, as the Kentucky privacy law considers all personal data of children under this age as sensitive data.
Nondiscrimination under the KCDPA
The KCDPA explicitly prohibits businesses from discriminating against consumers who exercise their rights under the law. Businesses cannot deny goods or services, charge different prices, or offer varying quality levels to these consumers. However, they may offer different prices, rates, levels, quality, or selections of goods or services to consumers if the offer is related to a voluntary loyalty, rewards, premium features, discounts, or club card program in which the consumer participates.
If a consumer chooses not to allow their personal data to be collected, processed, or sold, businesses cannot deny them access to their website. However, certain website features requiring essential cookies may not function properly if those cookies are declined. This limitation is not considered discrimination under the law.
Businesses are not required to offer a product or service that requires personal data they do not collect or maintain. They are also required to comply with state and federal discrimination laws and cannot process personal information in violation of these laws.
Data processing agreement under the KCDPA
The Kentucky privacy law requires controllers and processors to enter into contracts that govern data processing procedures. This contract is known as a “data processing agreement” under the European Union’s General Data Protection Regulation (GDPR) and Virginia’s CDPA and must include:
- instructions for processing personal data
- nature and purpose of processing
- type of data subject to processing
- duration of processing
- rights and obligations of both parties
Processors must ensure confidentiality of the personal data and that, at the controller’s direction or when the contract is complete, all personal data will be deleted or returned to the controller.
Under most data privacy laws, controllers are held accountable for the data processing actions, breaches, and violations by processors. However, the KCDPA provides two exceptions:
- if a controller or processor lawfully shares personal data with a third-party controller or processor, they are not liable for any violations by the recipient, provided they were unaware of any intent to break the law at the time of sharing
- if a controller or processor lawfully receives personal data, they are not responsible for any legal violations committed by the party that disclosed the data
The Nebraska Data Privacy Act (NDPA) contains a similar provision regarding controllers’ ultimate accountability for data processing activities.
Enforcement of the Kentucky Consumer Data Protection Act
The Kentucky Attorney General has the exclusive enforcement authority under the KCDPA. Consumers do not have a private right of action, but they can report potential violations or denials of their privacy rights directly to the Attorney General’s office.
Before initiating an enforcement action, the Attorney General must provide written notice to the implicated party, detailing the alleged violations and offering a 30-day cure period for organizations to address and resolve any issues. This cure period, which is a permanent aspect of the law, enables companies to rectify problems and implement measures to prevent future breaches.
Organizations found in violation must inform the Attorney General in writing of their corrective actions and confirm that future breaches will not occur.
Fines and penalties under the KCDPA
The Attorney General can initiate a civil action seeking damages against organizations that do not cure the violation within the 30-day period or breach the written statement they provide. Violations of the Kentucky privacy law may result in civil penalties of up to USD 7,500 per violation.
Consent management and the Kentucky Consumer Data Protection Act
The KCDPA adopts an opt-out model for data privacy, which allows businesses to collect and process personal data without requiring prior consent from individuals. However, exceptions are made for sensitive personal data and data belonging to children, where prior consent is mandatory. This approach is consistent with other US state-level data privacy laws.
Consumers must be able to opt out of data collection and processing for purposes such as sale, targeted advertising, or profiling. Businesses are required to make this opt-out option clearly available on their websites, usually through the privacy policy or privacy notice.
Websites often use consent banners on their websites that include clear links or buttons enabling users to opt out of data processing. Consent management platforms (CMPs) like Usercentrics CMP automate this process by managing cookies and other tracking technologies, ensuring they are blocked until the consumer gives consent, where this is required by law. CMPs also provide transparent information about the types of data collected, the purposes for which it is collected, and any third parties with whom the data is shared.
In the absence of a single federal privacy law in the US, businesses operating across the US and/or internationally may need to comply with various state and international privacy laws. CMPs assist by customizing cookie banners based on the user’s location, ensuring adherence to state-level laws like the KCDPA and international regulations like the GDPR.
Updates to the Kentucky Consumer Data Protection Act
Even before the KCDPA comes into effect, Kentucky legislators have passed a bill to update its requirements. Governor Andy Beshear signed HB 473 into law on March 15, 2025.
There are two healthcare-related updates. One is that information collected by health care providers that are acting covered entities under HIPAA, and that maintain protected health information according to HIPAA requirements, are exempt from relevant KCDPA requirements.
The second is that information maintained in limited data sets by entities covered by HIPAA in accordance with relevant HIPAA requirements is also exempt from relevant KCDPA requirements.
The other update limits the requirement for completing a Data Protection Impact Assessment (DPIA) in profiling cases to only those cases with unlawful disparate impact (the potential for disproportionate harm or disadvantage to members of a protected group).
These updates go into effect when the rest of the Kentucky Consumer Data Protection Act does, on January 1, 2026.
Preparing for the Kentucky Consumer Data Protection Act
Businesses operating in Kentucky have until 2026 to comply with the KCDPA. Companies already adhering to privacy laws in other states will find that much of their existing compliance work aligns with the KCDPA requirements. Businesses that meet the compliance thresholds set by the law must be prepared to offer users clear opt-out options and accessible privacy notices. Implementing privacy by design improves all aspects of organizational operations, not just compliance with regulations.
As the KCDPA adapts to new technologies and shifting consumer expectations, it is strongly recommended for businesses to seek guidance from a qualified legal professional or data privacy expert, such as a Data Protection Officer, to achieve and maintain compliance.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.
CookieYes is a consent management platform (CMP) that’s designed to help its users comply with the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), Digital Markets Act (DMA), and other data privacy laws and regulations.
While it does offer powerful features for managing consent, CookieYes users report some frustrations over subscription limitations and customization capabilities. It also lacks some of the tools and functions that some businesses may need to achieve and maintain privacy compliance.
We share our picks of the top six CookieYes alternatives to help you manage user consent and stay privacy compliant.
Our picks of the top CookieYes alternatives:
CookieYes competitors
| Software | Key feature | Recommended for |
|---|---|---|
| Usercentrics | Extensive analytics and reporting: Gain deep insights into user behavior to drive informed decision-making | Small businesses to enterprises |
| CookieFirst | Re-consent: Set goals for returning visitors to increase opt-in rates and support your marketing goals | Mid-market enterprises |
| Osano | “No Fines, No Penalties” Pledge: Get compensation of up to USD 200,000 for fines or penalties you incur while using the product according to set requirements | Solopreneurs |
| illow | Automated cookie categorization: Use the library of 50,000+ pre-categorized cookies to easily see which trackers are present on your website and what they’re used for | Agencies |
| CookiePro by OneTrust | DataGuidance-powered recommendations: Access regulatory analyses created by lawyers from across 300 jurisdictions to better understand and fulfill requirements | Medium-sized businesses |
| Cookie Information | Data Discovery: Find and categorize personal data collected and stored across your tech stack | Small businesses |
*As of July 2024
Why look for a CookieYes alternative?
CookieYes is a tool to create and customize consent banners and manage cookie consent. It’s available as a plugin for most major content management systems. While G2 users enjoy its intuitive interface, others express frustration over options for customization, and paywalls on numerous features.
- Limited customer support: CookieYes only offers support via email.
- Subscription limitations: G2 users have expressed frustration that important features are locked behind higher pricing tiers, while the free package limits the number of visitors that can see the consent banner.
- Limited customization options: G2 users are looking for more opportunities for banner customization. Plus, CookieYes branding can only be removed if you sign up for the most expensive plan.
Our picks of the 6 top CookieYes competitors
Having a robust consent management solution for customer data empowers your website and app visitors to control what information they share. This leads to two of the main benefits of consent: complying with major data privacy regulations and building trust with your audience.
1. Usercentrics
Usercentrics is committed to keeping up with regulatory changes and helping companies achieve and maintain data privacy compliance. This mission has earned it multiple G2 leaders badges in 2024.
Since 2012, Usercentrics has helped enable companies to provide seamless consent management solutions to respect user privacy and meet legal requirements in line with the GDPR, DMA, CCPA, and other global data privacy regulations and frameworks.
The platform gives you the convenience of being able to configure web and app consent in one place. Plus, features like its powerful DPS Scanner enable you to keep track of all data processing services that are collecting data on your website.
Key features
- Robust analytics and reporting: Get insights about user behavior, including cookie acceptance and denial rates, to drive informed decision-making.
- Legal template database: Make use of an extensive database of over 2,200 legal templates to ensure effective and compliant messaging across regions.
- Extensive customization: Tailor pre-built templates with HTML, CSS, or JavaScript to meet brand requirements.
- Multi-regulation compliance: Meet the requirements of the GDPR, CCPA, DMA (via Google’s Consent Mode requirements), and major data privacy laws and guidelines.
- Geolocation: Detect user locations and automatically update consent banners based on this information.
Pricing
Usercentrics offers a 30-day free trial to get businesses started with consent management, after which they can select one of three pricing plans.
- Starter: USD 60/month for up to 50,000 sessions
- Advanced: USD 175–1,150/month for 50,000+ sessions
- Premium: Custom pricing
| Flexible, scalable CMP that enables both web and app consent management | Steep learning curve for advanced features (G2 user reviews) |
| Database of over 2,200 legal templates | |
| In-depth analytics and reporting |

Usercentrics vs CookieYes
While CookieYes users note customization limitations, Usercentrics’ enables a wide range of customization options directly in the Admin Interface. Plus, features such as geolocation and full banner customization, which are only available on the two most expensive CookieYes tiers, are available from the lowest tier for Usercentrics.
2. CookieFirst

CookieFirst advertises that its users can get on a path to privacy compliance in mere minutes, thanks to its quick and easy signup process. Start with a site scan for first- and third-party cookies, after which you’ll be prompted to customize your cookie banner, which supports over 44 languages.
A free version is available, but you only get one cookie banner (in one language) as well as a one-time cookie scan of your website. Additionally, many essential features, such as IAB TCF 2.2 support, consent audit trails, and opt-in optimization, are not available on its entry-level paid plan.
Key features
- Cookie scanner: Detect first-, second-, and third-party cookies and local storage items present on your site with automatic monthly scans.
- Cookie policy generator: Create and edit an auto-generated cookie policy to share details on the trackers present on your site.
- Re-consent: Set goals for returning visitors to increase opt-in rates and support your marketing goals.
Pricing
CookieFirst gives users a two-week free trial or one month free when you sign up for the annual plan. There are four CookieFirst subscription options.
- Free: EUR 0/month
- Basic: EUR 9/month or EUR 99/year
- Plus: EUR 19/month or EUR 209/year
- Enterprise: Custom pricing
| Multilingual support for over 44 languages | License is needed for many basic features, such as IAB TCF 2.2 support and banner customization |
| Integrates with Google Consent Mode v2 | |
| Uses EU based sub-processors |
3. Osano

US-based Osano offers a range of privacy tools, including consent banner management and Subject Rights Management, as well as an additional privacy consultation tool.
While the platform uses automation to save time and reduce errors in consent management, customization options are somewhat limited (per G2 reviews).
Key features
- “No Fines, No Penalties” pledge: Get compensation of up to USD 200,00 for fines or penalties incurred due to noncompliance with data privacy regulations while using their solution, so long as you meet the requirements of this policy.
- Regulatory guidance: Receive alerts about upcoming legislative and regulatory changes to stay ahead of requirements and maintain compliance.
- Expert consultants: Access a team of data privacy attorneys and other privacy professionals to gain expert insights.
Pricing
Osano’s self-service cookie consent plans are priced as follows:
- Free: Free for 1 user on 1 domain with up to 5,000 visitors per month
- Plus: USD 199/month for 2 users on 3 domains with up to 30,000 visitors per month
Reach out to Osano for pricing on the following plans:
- Privacy Trust & Assurance
- Privacy Essentials
- Privacy Operations & Governance
| Easy to implement (G2 user reviews) | Limited customization options (G2 user reviews) |
| Free tier available | |
| Option to use Osano as a third-party, EU-based DPO |
4. illow

illow is a consent management banner that claims ultra speedy setup — enabling you to implement it with Google Consent Mode v2 in a few minutes.
Using its AI functionality, illow can automatically adapt your cookie banner and display a language- and regulation-specific banner to your visitors.
Despite these pros, G2 users make note of limitations to customization options for banners and policies.
Key features
- Automated cookie categorization: Use the library of 50,000+ pre-categorized cookies to easily see which trackers are present on your website and what they’re used for.
- Roles and permissions: Give specific authorizations and functions to teams or individuals based on the domain they interact with.
- Integrations: Add illow to your WordPress site and synchronize it with Google Tag Manager to improve consent management performance.
Pricing
You can choose from four illow plans based on the number of users that visit your website each month. Signing up for an annual subscription will save you 20 percent.
- Free: USD 0/month for up to 30,000 visitors
- Plus: USD 89/month for up to 1 million visitors
- Agency: Custom pricing and number of visitors
- Custom: Custom pricing for unlimited visitors
| Plug-and-play solution | Limited customization options (G2 user reviews) |
| Responsive, multi-lingual support for 25 different languages | |
| Cloud-based storage |
5. CookiePro by OneTrust

CookiePro by OneTrust is a widely used cookie compliance solution that processes hundreds of thousands of requests each month, for over 750,000 websites. However, after being acquired, CookiePro now forms part of the OneTrust data privacy platform.
Although existing customers are still able to log in to the CookiePro by OneTrust app, new users are directed to the OneTrust Consent & Preferences product, which includes powerful features beyond cookie consent, such as the new DataGuidance support portal.
Key features
- DataGuidance-powered recommendations: Access regulatory analyses, created by lawyers from across 300 jurisdictions, to better understand and fulfill consent management requirements. Or speak directly with an expert and receive additional guidance within 48 hours. (Via OneTrust)
- A/B testing: Test wording, layout, and other banner features to identify which configuration generates the highest conversions. (Via OneTrust)
- GRC and security assurance: Enables GRC (Governance, Risk, and Compliance) Management for numerous global compliance laws. (Via OneTrust)
Pricing
OneTrust offers custom pricing based on business needs and functionality. Contact them for a quote.
| Blocks third-party cookies by default | Nontransparent pricing |
| Includes A/B testing | |
| Includes mobile app consent |
6. Cookie Information

Cookie Information aims to make consent management easy. The platform enables businesses to deploy cookie banners and policies, and manage consent on both their app and website. Despite this, the tool lacks key features to help enable opt-in rate optimization, including A/B testing.
Key features
- Data Discovery: Find and categorize personal data collected and stored across your tech stack.
- Data Subject Requests: Centralize all data access and erasure requests to reduce response times.
- Whistleblowing: Give employees, partners, and clients a place to anonymously disclose incidents and suspected violations.
Pricing
Cookie Information has a flexible pricing structure based on the number of domains. The Essential and Professional plans share many features, but the latter has more robust monitoring capabilities.
- Essential: From EUR 15/month, per domain
- Professional: From EUR 45/month, per domain
| Automatic cookie classification | No A/B testing |
| Data stored on EU servers | |
| Advanced reporting capabilities, including consent rate insights |
Best consent management platform features
A reliable CMP makes it easier to achieve privacy compliance, increase cookie opt-ins, and build trust with your customers. In addition to meeting the provisions of international laws, business requirements, and frameworks — like the GDPR, Google’s Consent Mode v2, and TCF 2.2 — your chosen platform should:
- Work across all of your domains, platforms, and devices
- Give users granular control over their consent preferences
- Be able to generate custom cookie consent banners and policies
- Feature robust data security measures
- Automatically block unwanted cookies and trackers
- Use geotargeting and support multiple languages
Read about wordpress cookie consent now
Choose a flexible, scalable, and reliable CookieYes alternative
CookieYes offers an attractive user interface and good geographic coverage for regulations. That said, no single platform will be able to meet the requirements of each and every use case, and some users may find that the platform falls short of their compliance needs and expectations.
Each of the CMPs outlined in this article can enable you to improve user experience on your website or app, grow your privacy-led marketing initiatives, achieve and maintain privacy compliance, and build trust with your customers.
As an all-in-one CMP, Usercentrics stands out. It seamlessly integrates with your existing tech stack to ensure that you can effectively collect, store, manage, and signal user consent. This is key to help you achieve your business goals while complying with all relevant global regulations.
The information presented in this article is provided for educational purposes only. Engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations when evaluating solutions is always recommended. This information is accurate based on these publicly available sources as of the date of publication. Details about products, features, pricing, etc. may change over time.