Sensitive data exposure is a critical issue that poses significant risks to individuals and organizations alike. With the increasing digitization of personal, business, and classified information, the potential for this data to be accidentally or maliciously exposed has grown substantially.
Understanding what constitutes sensitive data, how it can be vulnerable, the consequences of its exposure, and how to protect it is essential for maintaining trust, complying with regulations, and safeguarding against severe financial and reputational damage.
What is sensitive data?
Sensitive data refers to confidential information that, if disclosed or accessed without authorization, could potentially harm individuals, organizations, or both. This type of data requires limits to collection and processing, and special protection measures due to its sensitive nature and the potential consequences of its exposure.
Regulated vs unregulated sensitive data
Sensitive data can be broadly categorized into two categories.
Regulated sensitive data is controlled by specific laws and guidance that dictate how it must be handled. For example, health information is protected under HIPAA in the United States, while financial data falls under the Payment Services Directive (PSD2) in the EU.
In addition, there’s unregulated sensitive data that might not be governed by specific legal frameworks. However, it still needs to be protected according to organizational policies and best practices. Examples of this kind of data include job applications or employee contracts.
What are the different types and examples of sensitive data?
Additionally, there are three main types of sensitive data that are particularly vulnerable to exploitation by hackers and malicious insiders. These are:
- personal information
- business information
- classified information
Let’s explore each of these types in more detail.
Personal information
Personal information refers to data that can identify an individual. This category includes Personally Identifiable Information (PII), such as:
- full name
- Social Security number
- date of birth
- home address
- phone number
- email address
Also included is Protected Health Information (PHI):
- medical records
- health conditions
- treatments
- health insurance information
Business information
Business Information encompasses data that is critical to an organization’s operations and competitive edge. This includes:
- Trade secrets: Confidential business information that provides a competitive advantage
- Intellectual property: Creations of the mind, such as inventions, literary and artistic works, designs, and symbols used in commerce
- Proprietary business information: Internal data that is vital for a company’s strategy and operations
- Financial information: This includes bank account numbers, credit/debit card data, credit history records, tax filings
Classified information
Classified information is primarily associated with government and military data and is restricted due to its sensitive nature. This category includes:
- Classified government documents: Information that is restricted by the government to protect national security
- Military secrets: Confidential information related to national defense and security
It’s important to note that these categories often overlap, and the classification of sensitive data can vary depending on the context and applicable regulations. Organizations typically implement data classification systems to categorize information based on its sensitivity level, ranging from public to highly restricted
Sensitive data under regulations
Protecting sensitive data is not just a best practice, it is often a legal requirement.
For example, under the General Data Protection Regulation (GDPR), sensitive data includes categories such as:
- racial or ethnic origin
- political opinions
- religious beliefs
- trade union membership
- genetic and biometric data
- health information
- sex life or sexual orientation
Companies handling sensitive data must obtain explicit consent before processing it unless there is a valid alternative legal basis. They need to implement security measures to protect against unauthorized access and breaches and ensure they only collect and retain the minimum necessary information.
Even under state privacy laws that use an opt-out consent model, i.e. not requiring prior consent before collection and processing in most cases, data categorized as sensitive does still typically require prior consent.
When transferring sensitive data outside the European Economic Area, it’s crucial to ensure the receiving country provides adequate protection. Conducting a Data Protection Impact Assessment (DPIA) helps identify and mitigate privacy risks, particularly in large-scale or high-risk scenarios, by assessing potential threats and ensuring compliance with data protection standards. Data privacy laws typically outline the circumstances under which DPIAs are required, or just recommended.
In addition, the California Consumer Privacy Act (CCPA) and its amendment, the California Privacy Rights Act (CPRA), define sensitive personal information as data that reveals an individual’s:
- Social Security number
- driver’s license number
- financial account information
- precise geolocation
- racial or ethnic origin
- religious beliefs
- union membership
- genetic data
- biometric information
- health information
- sexual orientation
The CPRA requires businesses to obtain opt-in consent before collecting or processing sensitive personal information. Under the CPRA and many other US state-level laws, data belonging to children is categorized as sensitive by default.
Brazil’s Lei Geral de Proteção de Dados (LGPD) also recognizes sensitive data as a special category requiring additional protections. Similar to the GDPR, the LGPD generally prohibits processing sensitive data without explicit consent or unless specific exceptions apply.
Many privacy laws mandate that organizations implement security measures, including encryption and access controls, to protect sensitive data. Additionally, some regulations require appointing a Data Protection Officer (DPO) and conducting DPIAs for large-scale processing.
Given the complexity of these regulations, companies should research which laws apply to them based on their location, the nature of their data processing activities, and the locations and demographics of their customers.
What is sensitive data exposure?
Sensitive data exposure is the unintentional or unauthorized release of confidential information, such as personal details like names and addresses, financial data, or health records. Exposing personal information can happen due to external threats, but also internal mistakes. And this exposure typically occurs due to inadequate security measures, such as weak passwords, lack of encryption, errors in data storage and sharing practices, or other human error.
What’s the difference between data exposure and data breach
While the terms “data exposure” and “data breach” are often used interchangeably, they have distinct meanings.
Sensitive data exposure refers to the unintentional revelation of sensitive information, often due to misconfigurations or human error. It does not necessarily imply that the data has been accessed by malicious actors.
In contrast, a data breach involves intentional, unauthorized access to sensitive data, typically through malicious means.
It’s important to understand these differences to react appropriately to data exposure.
Sensitive data exposure example
Sensitive data exposure is a pressing issue that can have serious ramifications for individuals and organizations alike. Large companies are often at the greatest risk of data exposure. Here are a few notable examples that illustrate the impact of sensitive data exposure.
In 2017, Verizon partner Nice Systems accidentally exposed the personal data of millions of Verizon customers through a misconfigured Amazon S3 storage bucket. The exposed information included names, addresses, account details, and PIN codes. This sensitive data was publicly accessible to anyone who knew the web address of the cloud server, potentially putting millions of customers at risk of identity theft or fraud.
A year later, in 2018, a bug in Google+’s API potentially exposed private profile data of up to 500,000 users. The exposed data included names, email addresses, occupations, and birthdates. While there was no evidence of data misuse, the exposure existed for three years before its discovery.
In 2021, a misconfiguration in Microsoft’s Power Apps portal service led to the exposure of 38 million records across 47 organizations. The exposed data included COVID-19 contact tracing information, job applicant data, and employee information. This incident occurred due to a default setting that made data publicly accessible unless manually set to private.
Sensitive data often gets exposed due to lapses in data management practices. These examples underscore the importance of vigilance and proper configuration to safeguard sensitive information in our increasingly connected world.
Read about marketing data management now
Ways in which sensitive data can be exposed
Sensitive data can be exposed through various channels, often due to vulnerabilities in security practices. Organizations must be vigilant in protecting their valuable information assets from unauthorized access or disclosure. Here are some common ways sensitive data can be exposed.
- Misconfigured databases: Poorly configured databases can inadvertently expose sensitive data to the public by accidentally allowing open access, failing to patch regularly, and other security issues.
- Unencrypted data transmission: Transmitting data without encryption leaves it vulnerable to interception by unauthorized parties.
- Insider threats: Employees with access to sensitive data can pose a risk, even if unintentional. This can involve mechanisms as mundane as email.
- Device loss or theft: Laptops or mobile devices containing sensitive information can be easily lost or stolen, leading to exposure.
- Weak access controls: Insufficient access controls can allow unauthorized users to access sensitive data.
- Outdated software vulnerabilities: Failing to update software can leave systems open to exploitation by attackers.
How to safeguard and manage sensitive data within your organization?
Protecting sensitive data is crucial for every organization. Whether you’re a small business or a large company, implementing sensitive data protection measures to avoid data vulnerability is non-negotiable. To help organizations tackle this challenge, the Open Web Application Security Project (OWASP) offers expert insights and actionable best practices for enhancing software security.
Let’s break down some practical steps you can take to keep your sensitive information safe, incorporating OWASP’s guidelines along with other industry best practices.
Identify and classify sensitive data
OWASP recommends creating a comprehensive inventory of all sensitive data processed, stored, or transmitted by your systems. This may include:
- customer information
- financial records
- intellectual property
- employee data
Once identified, classify this data based on its level of sensitivity. This classification will help determine appropriate security measures for each category.
Implement strong access controls
Restrict access to sensitive data on a need-to-know basis. For example, to limit sensitive data exposure, OWASP emphasizes the principle of least privilege, advising organizations to limit access rights to the minimum necessary for users to perform their jobs. They also recommend implementing strong authentication methods, such as multi-factor authentication, for accessing sensitive data.
Encrypt sensitive data
Encryption is a powerful tool for protecting sensitive information. OWASP stresses the importance of using up-to-date and strong standard algorithms for encryption. They advise encrypting all sensitive data both at rest and in transit and implementing proper key management practices. Additionally, consider end-to-end encryption for highly sensitive communications.
Secure physical and digital storage
Protect your data wherever it resides. This means using secure, encrypted storage solutions for digital data and implementing physical security measures for onsite servers and paper documents. Lastly, regularly back up data to secure, offsite locations or encrypted cloud services.
Train employees on data security
Your employees are your first line of defense. Therefore, don’t forget to conduct regular cybersecurity awareness training. This involves educating staff on identifying phishing attempts and other common cyber threats, establishing clear policies on data handling, and ensuring all employees understand their responsibilities.
Keep systems updated
Maintain the security of your IT infrastructure. This entails:
- Regularly updating all software, systems, and applications.
- Using a patch management system to automate updates and fix security vulnerabilities.
- Implementing firewalls and antivirus software, keeping them up to date.
Monitor and audit data access
Keep track of who accesses sensitive data and when. To do this, implement logging and monitoring systems to track data access and usage. Conduct regular audits to detect any unauthorized access or suspicious activity. And use data loss prevention tools to monitor and control data movement.
OWASP also recommends independently verifying the effectiveness of configurations and settings. This includes testing all cryptographic modules to ensure they’re operating correctly and verifying that security controls are properly configured and working as intended.
Develop an incident response plan
If your company handles sensitive data, you need to be prepared for potential data breaches. Therefore, create a comprehensive incident response plan that defines roles and responsibilities for handling security incidents. Then regularly test and update your plan to ensure its effectiveness.
Secure third-party relationships
You want to be sure to protect your data when working with external partners. To keep your sensitive data safe, assess and monitor the security practices of vendors who have access to your data. Consider implementing strong contractual agreements regarding data privacy and security. But also, limit vendor access to only the data they need. When working with third parties that are in other countries, there are additional requirements for security regarding international data transfers, too.
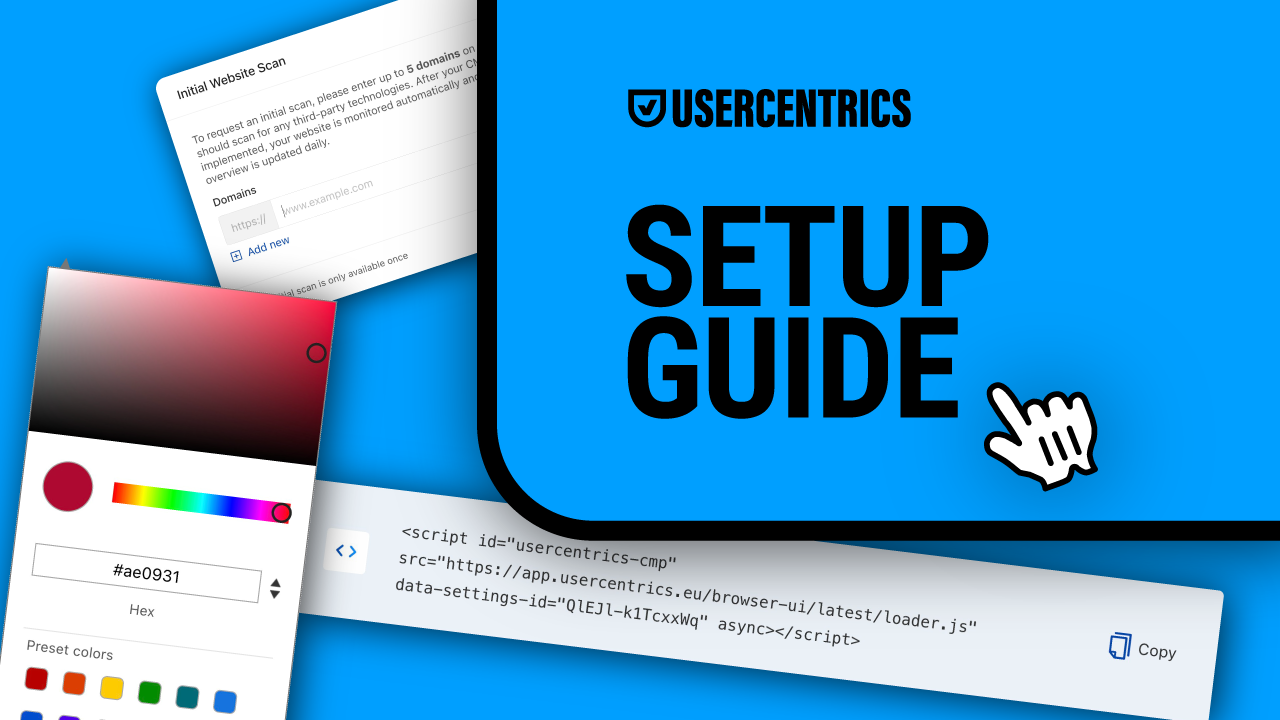
Implement a consent management platform (CMP)
To enhance your data protection and compliance, consider implementing a consent management platform. This collects and manages user consent for data processing activities, maintains detailed records of consent for compliance purposes, and provides users with easy-to-use interfaces to manage their privacy preferences.
A CMP like Usercentrics CMP is easy to integrate across your organization’s systems and platforms and helps you comply with data protection regulations like the GDPR and CCPA.
Compliance fines for sensitive data exposure
Compliance fines for sensitive data exposure are a growing concern for businesses globally as more and more data privacy laws are passed, and when penalties for sensitive data exposure or breaches can be even higher than baseline ones. With information exposure frequently in the news, regulators are enforcing strict penalties to ensure companies prioritize data protection.
Under the GDPR, organizations can face fines of up to EUR 20 million or 4 percent of global annual turnover (whichever is higher) for improper handling of sensitive data, including unauthorized exposure. These fines apply even if no breach has occurred, as the regulation has a higher penalty tier for more egregious or repeat offenses, and focuses on the principles of data protection and privacy by design.
In the US, the FTC can impose penalties of up to USD 40,000 per violation for unfair or deceptive practices related to data security, which can include improper exposure of sensitive information. Each day of noncompliance may be treated as a separate violation, potentially leading to substantial cumulative fines.
For US healthcare organizations, HIPAA violations related to improper exposure of protected health information can result in fines of up to USD 1.5 million per year. The exact amount depends on factors like the nature of the exposure and the organization’s compliance history.
Fines are typically determined based on factors such as the sensitivity of the exposed data, the duration of the exposure, the number of individuals affected, and the organization’s response and remediation efforts. Regulatory bodies also consider whether the exposure was due to negligence or intentional actions.
To avoid these penalties, organizations should implement data protection measures, conduct regular security assessments, and ensure proper handling and storage of sensitive information at all times.
Read about privacy-enhancing technologies now
Put in place measures to protect your sensitive data
Protecting sensitive data is not just a matter of regulatory compliance. It’s a crucial aspect of maintaining trust and security. From understanding the various types of sensitive information to implementing robust security measures and staying informed about regulatory requirements, organizations must be proactive in preventing data exposure.
By taking these steps, you can minimize the risk of data exposure, protect your organization from costly fines, and maintain the privacy and safety of your customers and employees.
The United States does not yet have a single federal data protection law. To date, an increasing number of states have passed their own laws and/or updated existing ones, and bills have been introduced, are in progress, or have failed in many others.
There are a number of other long standing privacy laws that target specific types of information or human demographics in the US, like the Health Insurance Portability and Accountability Act (HIPAA) for health and the Children’s Online Privacy Protection Act (COPPA) for children’s safety. This does not make it easy to keep track of all or achieve compliance for all relevant regulations that address personal data.
The first and most influential state-level consumer privacy law passed in the United States is the California Consumer Privacy Act (CCPA). It takes some influence from the European Union’s General Data Protection Regulation (GDPR) and has, in turn, influenced privacy bills drafted by other states, including the Virginia Consumer Data Protection Act (VCDPA).
What is the California Consumer Privacy Act (CCPA)?
The California Consumer Privacy Act (CCPA) is a US state-level consumer privacy law that was passed in 2018 and came into effect on January 1, 2020. It applies exclusively to residents of California, known as ”consumers” under the law, and regulates the protection of their personal information.
It’s worth noting, however, that California is the most populous US state, with a population of over 39 million people, as well as having the world’s fifth largest economy, and a number of the world’s largest and most influential tech companies are headquartered there. So the state has an outsized influence on many fronts.
A consumer under the law is a natural person who is a resident of California, however identified, including by means of a unique identifier. A “resident” means:
- every individual who is in the State for other than a temporary or transitory purpose
and
- every individual who is domiciled in the state who is outside the state for a temporary or transitory purpose
The CCPA was amended and expanded by the California Privacy Rights Act (CPRA), which took effect on January 1, 2023, and granted additional rights to consumers and established the California Privacy Protection Agency (CPPA), among other things. Enforcement of the CPRA began in February 2024 after a legal challenge. Enforcement had been scheduled to begin on July 1, 2023.
Definitions under the California Consumer Privacy Act (CCPA) data privacy law
The CCPA, as amended by the CPRA, defines several terms that cover the data it protects and data processing activities. Unlike most other data privacy laws, California does not use the terms “controller” or “processor”.
Personal information under the CCPA/CPRA
The CCPA/CPRA law defines personal information as “information that identifies, relates to, describes, is reasonably capable of being associated with, or could reasonably be linked, directly or indirectly, with a particular consumer or household.”
The CCPA/CPRA’s definition of personal information is wide ranging, and examples under the law include, among other things:
- IP address, real name, alias, postal address, Social Security number, and email address
- biometric information that can establish individual identity, such as imagery of the iris, retina, fingerprint, face, hand, palm, vein patterns, and voice recordings, as well as sleep, health, or exercise data that contain identifying information
- electronic activity information, such as browsing history or interactions with online ads
- professional or employment-related information
Personal information is known as personal data under many international and other state-level data privacy laws in the US.
Sensitive personal information under the CCPA/CPRA
Sensitive personal information is that which can cause harm to a consumer if misused, and includes, among other things:
- driver’s license, state ID card, passport, or Social Security number
- precise geolocation data that can accurately identify a person within a radius of 1850 feet (563 meters)
- racial or ethnic origin
- debit card or credit card number in combination with any required password or credentials that provide access to the account
- genetic data
- contents of a consumer’s postal mail, email, and text messages
Unique identifier under the CCPA/CPRA
The CCPA/CPRA law defines a unique identifier or “unique personal identifier” as “a persistent identifier that can be used to recognize a consumer, a family, or a device that is linked to a consumer or family, over time and across different services.”
The law specifies that a family means a custodial parent or guardian and any children under 18 years of age who are in their custody.
Examples of unique identifiers are:
- device identifier
- IP address
- cookies, beacons, pixel tags, mobile ad identifiers, or similar technology
- customer number, unique pseudonym, or user alias
Consent under the CCPA/CPRA
The law defines consent as “any freely given, specific, informed, and unambiguous indication of the consumer’s wishes by which the consumer, or the consumer’s legal guardian, a person who has power of attorney, or a person acting as a conservator for the consumer, including by a statement or by a clear affirmative action, signifies agreement to the processing of personal information relating to the consumer for a narrowly defined particular purpose.“
The following does not constitute valid consent under the CCPA/CPRA:
- acceptance of a general or broad terms of use or similar document
- hovering over, muting, pausing, or closing a piece of content
- agreement obtained through dark patterns
Sale under the CCPA/CPRA
The law defines sale as “selling, renting, releasing, disclosing, disseminating, making available, transferring, or otherwise communicating orally, in writing, or by electronic or other means, a consumer’s personal information by the business to a third party for monetary or other valuable consideration.”
A business is not considered to have sold information when:
- a consumer uses or directs the business to intentionally disclose or interact with third parties
- the business uses or shares an identifier for the consumer, for the purpose of informing others that the consumer has opted out of the sale of or limited the use of their personal information
- the business transfers personal information to a third party as an asset that is part of a merger, acquisition, bankruptcy, or other transaction in which the third party assumes control of all or part of the business
Who must comply with the California Consumer Privacy Act (CCPA)?
The CCPA/CPRA law applies to for profit businesses that operate in California and collect the personal information of the state’s residents, if they meet any one the following thresholds:
- annual gross revenues exceeding USD 26,625,000 for the previous calendar year
- receive, buy, sell, or share personal information of 100,000 or more consumers or households
- earn more than half of their annual revenue from the sale of consumers’ personal information
Interestingly, more recently passed privacy laws in other states have abandoned the revenue-only compliance threshold. Whether or not the company is headquartered in or has an office in California is not relevant to compliance. All companies that meet the threshold must meet CCPA/CPRA obligations if they are doing business with California residents, regardless of where in the world they are based.
What are consumers’ rights under the California Consumer Privacy Act (CCPA) laws?
The CCPA, as amended by the CPRA, grants consumers several rights to enable them to protect their personal information and control how it’s used.
- Right to delete: consumers can request businesses to delete their personal information that was collected from the consumer.
- Right to correct: consumers can request a business to correct any incomplete or inaccurate personal information that it holds.
- Right to know and access: consumers have a right to know and access the categories of personal information the business holds about them, the purposes for collecting the information, where the business obtained the information from, categories of third parties who receive the information, and the specific personal information the business has collected about the consumer.
- Right to know regarding sale or disclosure: consumers have the right to know what categories of personal information the business holds; the categories of personal information sold, shared, or disclosed; and the categories of third parties to whom it is sold, shared, or disclosed.
- Right to opt out: consumers have the right to opt out of the sale or sharing of their personal information.
- Right to limit: consumers have the right to limit the use or disclosure of their sensitive personal information.
- Right of nondiscrimination: consumers have the right not to be discriminated against for exercising any of their rights under the law.
In addition to these rights that are explicitly stated in the CCPA/CPRA, consumers also have the right to data portability. Where a consumer has exercised their right to know and access personal information, businesses must present the consumer’s specific personal information in a “structured, commonly used, machine-readable format.”
Obligations under the California Consumer Privacy Act (CCPA) Rules
Businesses have specific CCPA/CPRA obligations to protect consumers’ personal data, ensuring transparency and accountability in their data handling practices.
Notices required under the CCPA/CPRA
The CCPA/CPRA requires businesses to provide two distinct notices to consumers: a notice at collection and a privacy policy.
A notice at collection must be displayed to consumers at or before the point where the business collects their personal information. This notice must clearly list:
- categories of personal information collected, including sensitive personal information, if any
- purposes for which personal information will be used, including sensitive personal information, if any
- whether personal information or sensitive personal information is sold or shared
- how long the business will retain the personal information and sensitive personal information
- If the business sells or shares personal information, the notice must include a link with the specific words “Do Not Sell Or Share My Personal Information”, enabling consumers to easily opt out of such transactions.
The notice at collection should contain a link to the business’s privacy policy.
The CCPA privacy policy must include:
- a description of consumers’ privacy rights and how to exercise them
- categories of personal information collected, sold, or shared in the preceding 12 months
- categories of sources from which personal information is collected
- business or commercial purpose for collecting, selling, or sharing personal information
- categories of third parties to whom personal information is disclosed
Businesses commonly make their privacy policy accessible on their websites, typically found via a link in the footer so that consumers can easily find and review the privacy policy.
Consent requirements under the CCPA/CPRA
In most cases, the CCPA/CPRA does not require explicit consent from consumers for the collection, use, or sharing of their personal information. It operates on an opt-out model, where consumers are assumed to consent to data use unless they choose to opt out. There is an exception for the personal information belonging to minors:
- For minors aged 13 to 16, businesses must obtain explicit, opt-in consent from the minor before selling or sharing their personal information
- For minors under 13 years of age, businesses must obtain explicit consent from a parent or guardian before collecting or selling their data
Consumers have the right to opt out of the sale and several other uses of their personal information and to limit the use or disclosure of sensitive personal information.
Opt-out requests under the CCPA/CPRA
Businesses must provide options for consumers to opt out of:
- sale or sharing of their personal information (and targeted advertising and profiling under the CPRA)
- use or disclosure of their sensitive personal information for unauthorized purposes
The law mandates specific ways for businesses to provide consumers with opt-out options.
- Through a clear and conspicuous link on the business’s homepage titled “Do Not Sell Or Share My Personal Information,” which directs consumers to a page from which they can opt out of the sale or sharing of their personal information.
- Through a clear and conspicuous link titled “Limit The Use Of My Sensitive Personal Information,” which enables consumers to limit the use or disclosure of their sensitive personal information.
- If a business prefers, it can use a single link that combines both functions, as long as it effectively enables consumers to opt out of both, the sale, sharing, targeted advertising, or profiling from their personal information, and limiting the use or disclosure of their sensitive personal information.
Businesses must also respect universal opt-out mechanisms, such as Global Privacy Control (GPC) signals, through which consumers can set their consent preferences once and communicate them automatically across various websites and online services.
Consumer requests for right to know, correct, and delete
Consumers have the right to request information about the personal data collected about them, as well as to correct inaccuracies or to delete that data.
The law requires businesses to provide at least two designated methods for consumers to submit their requests, which must include a toll-free telephone number. For businesses that operate exclusively online and have a direct relationship with consumers, an email address is sufficient.
If a business maintains a website, it should enable consumers to submit requests for information, correction, and deletion directly through the site.
Consumers can request data that was collected up to 12 months prior to the date of their request. Businesses have 45 days from the date of the request to disclose the requested information, and they may seek an extension of an additional 45 days under certain circumstances
While businesses may require consumers to login to an existing account to verify identity and submit a request, they cannot require consumers to create a new account for this purpose.
Contracts under the CCPA/CPRA
Businesses that collect consumers’ personal information sometimes sell or share consumers’ personal information with a third party, or disclose the personal information to a service provider or contractor for business purposes.
The CCPA/CPRA requires businesses to enter into agreements with these third parties, service providers, or contractors. The agreement must outline that:
- the personal information is sold, shared, or disclosed only for limited and specific purposes
- the third party, service provider, or contractor must comply with the CCPA/CPRA obligations applicable to them
- the third party, service provider, or contractor must provide the level of data privacy protection required by the law
- the business is entitled to take “reasonable and appropriate steps” to ensure that any third party, service provider, or contractor uses the personal information shared in a way that aligns with the business’s CCPA/CPRA obligations
- the third party, service provider, or contractor must inform the business if it cannot meet its legal obligations
- the business has the right to take reasonable and appropriate steps to stop and remedy any unauthorized use of personal information, after providing notice
Contracts with service providers and contractors must also prohibit them from:
- selling or sharing personal information
- retaining, using, or disclosing personal information for any purpose other than that specific in the contract
- combining the personal information received from the business with personal information received by any other means, except for purposes exempted under the law
Data security under the CCPA/CPRA
Businesses that collect consumers’ personal information are obligated to safeguard the personal information from unauthorized or illegal access, destruction, use, modification, or disclosure. The CCPA/CPRA requires businesses to implement “reasonable security procedures and practices” for this purpose.
Data minimization under the CCPA/CPRA
Under the CCPA/CPRA, businesses can collect, use, store, and share consumers’ personal information only to the extent needed to achieve the original purpose for collecting the information, or for another compatible purpose. The personal information must not be processed in ways that conflict with the original purposes.
This requirement is a key aspect of data minimization, which means that companies must limit their handling of personal data to what is essential for the intended purposes.
The CPPA, in its Enforcement Advisory No. 2024-1, has highlighted the various CCPA regulations that reflect the principle of data minimization by prohibiting businesses from requiring consumers to share additional information “beyond what is necessary.”
Enforcement and penalties under the California Consumer Privacy Act (CCPA)
The CCPA/CPRA has certain unique characteristics when it comes to enforcing the state’s consumer privacy law.
Unlike most states, where the Attorney General has sole enforcement authority, California permits both the Attorney General and CPPA to enforce the law. However, the CPPA cannot limit the Attorney General’s authority and must stay an administrative action or investigation when requested. A business cannot be penalized by both the Attorney General and the CPPA.
Violations of the CCPA/CPRA attract civil penalties of up to:
- USD 2,663 per non-intentional violation
- USD 7,988 per intentional violation and violation involving the personal information of minors
The CCPA/CPRA is also the only consumer privacy law in the US that grants consumers a private right of action, although it is limited to specific situations. Consumers can sue businesses in the event of a data breach or personal security information breach, which occurred because the business failed to implement reasonable security measures to protect the personal information and that results in non-encrypted or non-redacted data being stolen.
Consumers must give businesses 30 days to cure the violation in the event of a data breach before they can bring an action against the business. Of note is that when the CCPA came into effect, the Attorney General also provided a 30-day cure period; however, that has now sunset.
Consumers can bring an action:
- to recover damages between USD 107 and USD 799 per incident, or actual damages suffered, whichever is greater
- for injunctive or declaratory relief
If a consumer believes their rights, other than those arising out of a data breach, have been violated, they may file a complaint with the Attorney General or the CPPA.
GDPR vs. CCPA: a summary
The EU’s General Data Protection Regulation (GDPR) and the CCPA/CPRA are landmark regulations when it comes to protecting data privacy.
The GDPR is considered one of the most stringent data protection regulations worldwide, and has influenced many other regulations, such as Brazil’s General Data Protection Law (LGPD) and the CCPA.
The CCPA was the first state-level consumer privacy law passed in the US and has many unique provisions, such as dual enforcement and private right of action.
We look at the two regulations side by side to examine some of the similarities and differences.
| CCPA | GDPR | |
|---|---|---|
| Scope and applicability | Applies to for-profit businesses that collect personal information from California residents and either: – have annual gross revenues exceeding USD 26,625,000 for the previous calendar year – receive, buy, or sell personal information of 100,000 or more consumers or households – earn more than half of their annual revenue from the sale of consumers’ personal information It applies to any business that meets these conditions, regardless of where the business is located (extraterritoriality). | Applies to any entity that processes the personal data of individuals located in the EU/EEA and either: – offers them goods and services – monitors their behavior Like the CCPA, it applies regardless of where the business is located (extraterritoriality). The GDPR applies to non-profit organizations and government agencies as well as for-profit businesses. |
| What it protects | Personal information of California residents, known as consumers, even if they are temporarily outside the state. Personal information includes that which can be linked to a consumer or a household. | Personal data of individuals located in the EU territory, known as data subjects. Applies to individuals only and does not extend to households. |
| Consent | Operates on an opt-out consent model and doesn’t require prior consent to collect and process data in most cases. Consumers can opt out of the use of their data in specific cases. | Operates on an opt-in consent model, meaning that organizations cannot collect or process data unless the user gives their explicit consent. |
| Legal bases | There are no specific legal bases for collecting personal information. | Personal data can only be collected if there is a legal basis: – consent – to perform a contract – legal obligation – to protect vital interests – in the public interest – legitimate interest |
| Enforcement authority | California Attorney General and California Privacy Protection Agency (CPPA). | Data Protection Authorities (DPA) of the EU Member States. |
| Private right of action | Consumers can directly sue businesses only in the event of a data breach caused by a failure to take security measures, in specific circumstances. | Data subjects can lodge complaints with the DPA in their state and receive compensation if they have suffered material or non-material damage. |
| Civil penalties | Up to USD 2,500 per non-intentional violation and USD 7,500 per intentional violation, and statutory damages for data breach. | Up to 2 percent of annual turnover or EU 10 million, whichever is higher, for certain violations. Up to 4 percent of annual turnover or EU 20 million, whichever is higher, for more serious violations. |
What does the CCPA/CPRA mean for companies’ websites?
If a business meets one of the CCPA/CPRA thresholds and has an online property, it must take several steps to meet CCPA/CPRA obligations.
- The website must present visitors with a notice at collection that lists the categories and purposes of the personal data collected, whether personal information is sold or shared, and how long the business will retain the personal information.
- The website must include a privacy policy that informs consumers of their privacy rights and how to exercise them, as well as the business’ privacy practices in more detail.
- If the business sells or shares personal data, it must present a link titled “Do Not Sell Or Share My Personal Information” to enable users to opt out of the sale of their personal data. It must also present a link titled “Limit The Use of My Sensitive Personal Information” to enable users to opt out of the use of their sensitive personal information.
- For personal information of minors, businesses must obtain explicit consent from the consumer (between 13 and 16 years) or their parent or guardian (when the minor is below 13 years) before their personal information can be shared or sold.
Businesses can use a consent management platform (CMP) like Usercentrics CMP to achieve CCPA compliance.
A CMP enables websites to display cookie consent banners with straightforward links or buttons that enable users to opt out of data processing. It can also handle cookies and other tracking technologies, blocking their use when a consumer exercises their right to opt out.
CMPs also help websites provide clear information to users about the types of data being collected, the purposes for collection, and the third parties that may receive this data, in accordance with the CCPA/CPRA and other data privacy laws.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.
The Utah Consumer Privacy Act (UCPA) came into effect on December 31, 2023, and is one of the increasing number of statewide laws in the US that aim to protect the rights of consumers whose data is processed by businesses.
When it was passed, the UCPA was the fourth piece of legislation of its kind in the US. Lawmakers were able to draw on earlier regulations, like the Colorado Privacy Act (CPA) and the Virginia Consumer Data Protection Act (VCDPA), which were both based on the first and most stringent US privacy law: the California Consumer Protection Act (CCPA).
With this foundation, the UCPA strikes a finer balance between consumer rights and business responsibilities. Overall, the narrower scope of its definitions and compliance requirements means that it can be seen as “lighter” and more business-friendly than the majority of other state-level data privacy laws in place.
What is the Utah Consumer Privacy Act?
The UCPA gives consumers in Utah a degree of control over how businesses are able to collect and use their data. Under the UCPA, individuals have the right to know if a business is processing their personal data, to access and have that data deleted, and to opt out from their data being sold.
Unlike other similar data privacy laws, the UCPA doesn’t place limits on the data that businesses can gather and what they can do with it. The responsibility for minimizing the collection and processing of data rests with the consumer.
UPCA summary
The UCPA protects the privacy rights of Utah residents and establishes data privacy responsibilities for companies that operate in the state and process the data of the nearly 4 million individuals who live there.
It requires businesses that collect data to protect the confidentiality and integrity of that data to reduce the risk of harm associated with processing it. Organizations must also provide consumers with clear and accessible privacy notices and inform them about how they can opt out of the sale of their data.
Like other US state laws, the UCPA uses an opt-out model for user consent, rather than the opt-in model in place for regulations such as the General Data Protection Regulation (GDPR).
This means that consumers’ personal data can be collected, sold, or used for targeted advertising without first obtaining their explicit and informed consent. The only exception here relates to children’s data. In that case, consent must be obtained from a parent or legal guardian.
Unlike most US data privacy laws, the UCPA does not require prior consent for the processing of data categorized as sensitive. Companies just need to notify consumers about collection and use and provide an opt-out option.
The sale of data is one of the key focuses for the UCPA. The Act defines any “exchange of personal data for monetary consideration by a controller to a third party” as a sale.
This definition doesn’t include non-monetary exchanges, which means that it doesn’t apply to data sharing among businesses, differentiating it from the CCPA and California Privacy Rights Act (CPRA).
However, consumers do have the right — and must be provided with the option — to opt out of the sale of their data or its use for targeted advertising. If a consumer exercises this right, their data can no longer be used.
Updates to the UCPA
On March 13, 2024, Utah became the first state to enact an AI-focused consumer protection law. The Utah Artificial Intelligence Policy Act (UAIP), which came into effect on May 1, 2024, modifies the UCPA and places certain duties on businesses using generative AI in the course of their business.
The act focuses mainly on businesses operating in regulated industries, i.e. those where a person requires a license or state certificate to work. These businesses must disclose to customers that they are interacting with generative AI or materials that are created by generative AI.
It also requires businesses in non-regulated sectors to disclose the use of this technology if asked or prompted by a customer. However, it’s not clear what mechanisms an organization must put in place to field these requests or how the disclosure should take place.
The UAIP has also created an Office of Artificial Intelligence Policy that is tasked with setting up an Artificial Intelligence Learning Laboratory Program. The goal is that this AI Lab will support AI-related regulation and development within the state.
Definitions under the Utah Consumer Privacy Act
The UCPA applies to controllers or processors of consumer data. It defines these terms as follows.
Controller under UCPA
Controller means “a person doing business in the state who determines the purposes for which and the means by which personal data are processed, regardless of whether the person makes the determination alone or with others.” (Section 101.12 UCPA)
Processor under UCPA
Processor means “a person who processes personal data on behalf of a controller.” In relation to controllers and processors, “person” includes natural persons or commercial or noncommercial entities, including third parties, that process data and meet the applicability criteria. (Section 101.26 UCPA)
Consumer under UCPA
Consumer means “an individual who is a resident of the state acting in an individual or household context” who is not “acting in an employment or commercial context.” (Section 101.10 UCPA)
Personal data under UCPA
“Personal data” refers to “information that is linked or reasonably linkable to an identified individual or an identifiable individual.” (Section 101.24 UCPA)
There are specific forms of personal data that can make an individual directly identifiable (e.g. a name or email address), while others may not qualify on their own (e.g. an IP address). However, it’s important to note that non-identifying data may become identifying when it’s aggregated with other kinds of personal data.
Exclusions to the definition of personal data
The UPCA sets out a number of exclusions in relation to personal data. This includes information that:
- is publicly available
- has been deidentified or anonymized
- relates to groups of consumers and has been aggregated to the extent that individuals cannot be identified
Sensitive data under UCPA
Unlike some other data privacy laws, the UCPA does not require businesses to obtain consent for processing sensitive personal data.
However, controllers do have to clearly notify consumers and provide the opportunity for them to opt out of having their sensitive personal data processed before such data is collected and processed. Like non-sensitive data, consumers can also opt out of processing for sensitive data later, at which point processing must cease.
The Act (Section 101.32 UCPA) defines “sensitive data” as personal data that includes or reveals:
- racial or ethnic origin (unless processed by a video communication service or by a licensed healthcare provider)
- religious beliefs
- sexual orientation
- citizenship or immigration status
- medical history, mental or physical health condition, or medical treatment or diagnosis by a healthcare professional
- genetic or biometric data (if the processing is for the purpose of identifying a specific individual)
- geolocation data (if the processing is for the purpose of identifying a specific individual)
Who must comply with the Utah Consumer Privacy Act?
Similar to other data privacy laws, the UCPA has provisions that provide rights to consumers and place obligations on businesses, provided that they meet certain criteria.
UCPA applies to businesses that:
- Operate in Utah, either by conducting business there or by offering a product or service to consumers who reside in the state.
- Meet the annual earnings and data processing thresholds, meaning they report revenue of USD 25 million and either
- control or process the data of 100,000 consumers
or
- derive more than 50 percent of gross revenue from the sale or control of personal data of 25,000 or more consumers
The UCPA differs from some of the other data privacy laws as entities have to meet multiple criteria for it to apply. This narrows its scope. For example, the revenue threshold will exclude smaller SMEs from qualifying. Many of the more recently passed US state-level privacy laws do not include a revenue-centric threshold, though Utah is one of the earlier ones that does.
Unsure if the UCPA applies to your business? Use our UCPA checklist to understand if the Act applies to your business, and what you need to do to be compliant.
Exemptions to Utah Consumer Privacy Act compliance
Organizational exemptions
In addition to organizations that fall below the revenue or processing volume thresholds, the UCPA exempts a number of other entities, including:
- institutions of higher education
- nonprofit organizations
- government organizations and contractors
- Indigenous groups
- air carriers
- organizations covered by the Health Insurance Portability and Accountability Act (HIPAA)
- financial institutions governed by the Gramm-Leach-Bliley Act (GLBA)
Data exemptions
The UCPA does not apply to information that’s already subject to the following regulations:
- Driver’s Privacy Protection Act (DPPA)
- Fair Credit Reporting Act (FCRA)
- Family Educational Rights and Privacy Act (FERPA)
- Farm Credit Act (FCA)
- Gramm-Leach-Bliley Act (GLBA)
- Health Insurance Portability and Accountability Act (HIPAA)
Employment exemptions
Data processed or maintained during the course of an individual’s employment is exempt from the UCPA.
This covers instances when an individual is applying for a job, as well as when they are “acting as an employee, agent, or independent contractor of a controller, processor, or third party,” provided that the data is “collected and used within the context of that role” (Section 102.2(o)(i) UCPA).
Consumer rights under the Utah Consumer Privacy Act
Consumers have four primary rights under the UCPA: access, deletion, portability, and opting out.
- Right to access, including confirming whether a controller is processing their data, and the ability to request and receive that data
- Right to deletion of personal data, if the data subject directly provided the data to the controller
- Right to portability, obtaining a copy of their personal data from the controller, in a format that is:
- portable to a technically reasonable extent
- readily usable to a practical extent
- enables the consumer to transmit the data to another controller reasonably easily, where the processing is carried out by automated means
- Right to opt out of certain processing, specifically for the sale of the personal data or the purposes of targeted advertising
Key differences with other privacy laws
While these rights are similar to those given to consumers under other data privacy laws, both within the US and globally, UCPA does not create other common rights, such as the right to appeal and the right to correct (to request and have omissions or inaccuracies rectified).
In addition to these exclusions, the UCPA does not provide for a private right of action (the ability for an individual consumer to sue a controller for noncompliance or a data breach). To date California is the only state that allows for this. Consumers also cannot use a violation of the UCPA to support a claim under other Utah laws.
What’s more, controllers under the Utah privacy law aren’t required to recognize “universal opt-out signals” as a method for consumers to opt out of data processing. This excludes global privacy control (GPC) measures, where users can set their consent choices once and have them respected across all other sites and properties on which they are active, instead of having to specify their choice at every online property they visit.
What are controllers obliged to do under the Utah Consumer Privacy Act?
Under the UCPA, data controllers must outline exactly how consumers can submit a request and exercise their rights related to their data. They must also respond to any requests within 45 days.
Transparency under the UCPA
Controllers must provide consumers with a privacy notice or policy that is “reasonably accessible and clear.” This notice would typically appear on a business’s website and must include:
- categories of personal data processed by the controller
- categories of personal data the controller shares with third parties
- categories of third parties with whom the controller shares personal data
- a clear explanation of how consumers can exercise their rights, including the right to opt out
- “clear and conspicuous” disclosure if personal data is sold to a third party or used for targeted advertising
A consent management platform (CMP) can make this easier for you. With the right tool, you can stay compliant by generating an accurate, comprehensive, and up to date privacy policy and notify consumers about any data collection that’s taking place.
Consumer requests under the UCPA
Consumer requests must be fulfilled free of charge to the consumer, unless the request is:
- the second or subsequent request within the same 12-month period
- “excessive, repetitive, technically infeasible, or manifestly unfounded” (Section 203.4.(b)(i)(A) UCPA)
- reasonably believed by the controller to have the primary purpose of “something other than exercising a right” (Section 203.4.(b)(i)(B) UCPA)
- intended to harass, disrupt, or impose undue burden on the resources of the controller’s business
Controllers must take action and notify the consumer of their actions within 45 days of receiving a request. If the controller cannot or will not respond to or fulfill the consumer’s request, e.g. if the consumer’s identity cannot be reasonably verified, they must communicate this during that same 45-day period.
However, there are exceptions. The response period can be extended by another 45 days if reasonably necessary, for example, if the request is very complex or the controller is dealing with a high number of requests.
Where there is an extension, the consumer must be informed within the initial 45 days. The notification must include reasons for and the length of the delay.
Unlike some other laws, the UCPA does not have an appeal process for consumers whose requests are denied.
Data security under the UCPA
Controllers must “establish, implement, and maintain reasonable administrative, technical, and physical data security practices” that have been “designed to protect the confidentiality and integrity of personal data.” (Section 302.2(a) UCPA)
This applies both to the controller and any third party services they use.
Third-party data processing under the UCPA
Controller organizations may use third parties to process data on their behalf, so long as there is a contract in place.
The contract must include data processing instructions, as well as some of the same information that must be outlined in the consumer notification, including:
- the nature and purpose of the processing
- the type of data to be processed
- the duration of processing
- all parties’ rights and obligations, including a duty of confidentiality
- a provision that requires the processor to have a written contract with any subcontractor engaged to process personal data that mirrors the obligations on the processor
Under the UCPA, controllers don’t have to evaluate the risks of their data processing activities via data protection assessments. What’s more, a contract between a controller and processor does not need to stipulate that the processor must comply with any reasonable data privacy audits set in motion by the data controller.
Processing of children’s personal data under the UCPA
The processing of children’s data is the only activity under the UCPA that requires explicit consent. Under the Act, a child is defined as an individual known to be under the age of 13.
Controllers must obtain verifiable parental or guardian’s consent prior to processing and process the data in accordance with the Children’s Online Privacy Protection Act (COPPA).
Nondiscrimination under the UCPA
Controllers may not discriminate against any consumer who exercises their privacy rights. Examples of potential discrimination include:
- denying goods or services
- charging a different price or rate for goods or services
- providing a different level of quality for goods or services
However, a controller is allowed to offer “a different price, rate, level, quality, or selection of a good or service to a consumer” (Section 302.4(b) UCPA) if that customer has opted out of targeted advertising, or if the offer relates to the consumer voluntarily participating in the controller’s loyalty program.
Enforcement of the Utah Consumer Privacy Act
Enforcement authority
The Utah attorney general has full enforcement authority of UCPA. However, the Division of Consumer Protection is responsible for administering consumer complaints and has the authority to investigate alleged violations.
Investigations and cure period
Where authorities find reasonable cause or evidence of a violation, it’s referred to the Attorney General. If the Attorney General pursues the investigation, their office must provide the data controller or data processor with a written notice about the violation.
The UCPA provides the offending party with a 30-day “cure” period. This is a grace period during which the controller is given the opportunity to rectify any violation and provide a statement to the Attorney General about what has been done to resolve the violation and ensure it won’t be repeated. Unlike many US data privacy laws, the UCPA’s cure period does not sunset.
Damages and fines
In cases where punitive action is required, for example, if the controller or processor fails to resolve, or repeats the violation after providing a written statement to the contrary, the Attorney General can initiate an enforcement action. This includes damages and fines up to USD 7,500 per violation.
Consent management and the Utah Consumer Privacy Act
The UCPA uses an opt-out model to regulate data collection and processing in the state of Utah. As a data controller in Utah, you’re not required to obtain data subjects’ consent before collecting personal data, unless that data belongs to a child.
However, you are required to give consumers a clear notification that their data is being collected, inform them about their rights, and provide them with the means to opt out, either before or at the point of collection and processing.
To achieve and maintain compliance, use a CMP. A robust CMP can automate the process of notifying customers about data processing, tailoring consent messages, and managing their opt-out choices. This makes it easier to achieve and maintain compliance with the UCPA and other US privacy laws like the CCPA/CPRA and VCDPA.
A robust CMP helps your business obtain consent in a transparent manner, enabling you to collect valuable data while building trust with your customers.
Navigating UCPA compliance
While the requirements for UCPA compliance are less demanding than similar laws’, the potential fines and damage to brand reputation that can result from noncompliance mean that businesses must still be diligent.
Usercentrics can help you adhere to regulatory requirements of laws like the UCPA with its all-in-one CMP that enables you to produce content for privacy notices in just a few clicks. What’s more, our platform simplifies consumer consent management and helps you personalize the consent experience for your users.
If you have questions or interest in implementing our CMP to help you achieve compliance with privacy laws in the US and around the world, talk to one of our experts.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.
Are you prepared for the latest trends in digital advertising? With the complexities of privacy in digital advertising evolving, it’s crucial to stay updated on how to leverage the newest tools and strategies effectively.
Watch our on-demand webinar recording to understand how to optimize ad performance while ensuring compliance with privacy standards. Learn from top PPC experts about Google’s Consent Mode and Customer Match to maximize your marketing ROI.
Why Watch?
- Understand Google’s Consent Mode: Get detailed insights into leveraging Google’s Consent Mode to optimize ad performance while respecting user privacy preferences.
- Maximize Customer Match: Learn strategies to effectively use Customer Match to reach your target audience with personalized ads.
- Privacy Best Practices: Discover the latest privacy regulations and how to ensure your campaigns are compliant.
- Expert Guidance: Hear from industry leaders Adriaan Dekker, Thomas Eccel, Bethany Hendricks, and David Diaz, who will provide actionable steps for your marketing strategies.
Register now to access the recording and stay informed on how to navigate the complexities of privacy in digital advertising.
Small and medium-sized companies and digital marketing agencies must meet and maintain all of the same data privacy requirements that enterprise companies do, just with fewer resources. So, saving time and streamlining work for your campaigns is extra valuable.
As user privacy expectations continue to evolve, Google has recently updated its data privacy and consent requirements in Europe, the UK, and Switzerland, and is facilitating easier adoption of Google consent mode to help meet these requirements. Consent management platforms (CMPs) that are certified by Google, like the Usercentrics CMPs, can now be implemented right from the Google Ads, Analytics, or Tag Manager interface.
Digital marketers in EU markets can now take steps to ensure they can continue targeting ads, measuring conversions, and generating revenue while meeting Google’s European Union user consent policy.
Collect and signal user consent to meet Google’s requirements and prepare for the era of privacy-led marketing. Respect user consent preferences while continuing to use Google services for your marketing operations. Continue the success of your measurement, ad personalization, and retargeting features for your campaigns.
Usercentrics CMP implementation in the Google tag UI
Google consent mode should be used with a CMP to signal user consent information to Google services. All of the Usercentrics CMPs are certified to meet the necessary requirements by Google: web and mobile, and CookiebotTM Web CMP.
Now you can create your Usercentrics account, set up your consent banner, and enable Google consent mode v2. All in one place in just a few clicks.
Read about consent mode GA4 now
What setup happens in the Google tag UI?
When you are logged into your Google Ads, Analytics, or Tag Manager account and click to set up the Usercentrics CMP, this is what happens:
- Usercentrics account setup
- Creation of your CMP banner configuration
- Google Ads and Google Analytics selected and added to the consent banner as data processing service per default
- script tag retrieval — Google pushes the Usercentrics CMP scripts to your website via Google Tag Manager or Google tag (gtag.js)
What setup happens in the Usercentrics Admin Interface?
Once you’ve completed most of the setup in your Google Ads, Analytics, or Tag Manager account, this is what you will finish up in your Usercentrics account using the Admin Interface:
- Customization of your consent banner design and content
- Addition of tracking services to your CMP (Google Ads and Google Analytics are added automatically)
Find all the instructions for the Usercentrics CMP setup in your Google Ads, Analytics, or Tag Manager account here.
“It’s now easier and more seamless than ever for SMEs to meet Google’s requirements and limit disruption to their digital marketing operations.” – Eike Paulat, Director of Product at Usercentrics
Benefits of Usercentrics CMP for Google customers
In addition to being Google-certified, Usercentrics Web and App CMPs have integrated the latest version of Google consent mode and the TCF v2.2. Usercentrics CMP also provides marketers with the following benefits for great user experience and streamlined consent management for a better privacy experience and optimizing campaigns:
- 2,200+ legal templates for reliable legal expertise that saves time and resources
- geolocation rules to display relevant banners to visitors in specific locations around the world
- banner auto-translation for 60 languages for clarity and personalized user experience
- extensive customization options to fully match your design and branding
- in-depth analytics and A/B testing for opt-in rate optimization
- cross-platform and cross-device functionality with web and app versions
The terms “data privacy” and “data security” are regularly used interchangeably, but they represent distinct concepts vital to safeguarding information and the people it comes from.
Understanding the nuances between data privacy and data security is essential for individuals and organizations striving to protect sensitive information, their customers, and, ultimately, their business.
We explore the key differences between these two critical aspects of regulatory compliance, delve into practical examples, and outline best practices for implementing compliant data privacy and security measures.
What is data security?
Data security refers to the set of measures, protocols, and technologies implemented to protect digital information from unauthorized access, corruption, theft, or destruction.
It encompasses a wide range of practices and tools designed to ensure the confidentiality, integrity, and availability of data throughout its lifecycle. The degree of protection and the measures taken vary depending on company size, industry, data stored, relevant regulations, and other factors.
The three primary objectives of data security are:
- Confidentiality: Ensuring that data is accessible only to authorized individuals or systems.
- Integrity: Maintaining the accuracy and consistency of data and preventing unauthorized modifications.
- Availability: Guaranteeing that data is accessible to authorized users when needed.
By implementing robust data security measures, organizations can mitigate the risks associated with data breaches, cyberattacks, insider threats, and other risks, thereby protecting their valuable information assets and maintaining the trust of their stakeholders.
Read about Big data marketing now
What is data privacy?
While data security focuses on safeguarding data from external threats, data privacy deals with how that data is handled and shared — starting from before it’s collected to when it’s deleted, returned, or anonymized.
Data privacy, also known as information privacy, refers to the rights of individuals to control how their personal information is collected, used, shared, and stored, and requirements levied on organizations — usually commercial companies — to obtain and use data according to regulatory guidelines.
It focuses on the ethical and legal aspects of handling personal data, ensuring that individuals have autonomy over their information and that organizations respect their privacy rights. It should be noted, however, that data privacy regulations generally include elements that address both data security and privacy.
Some key aspects of data privacy include:
- Consent: Obtaining explicit permission from individuals at specified points for collecting and processing their personal data.
- Transparency: Clearly communicating what data will be collected, how it will be used, and how data will be sold or shared.
- Purpose limitation: Using personal data only for the specific purposes for which it was collected.
- Data minimization: Collecting and retaining only the necessary personal information for specific, publicized purposes.
- Individual rights: Providing individuals with the ability to opt in or opt out of data sharing, selling profiling, or targeted advertising, in addition to other varying rights, like correction or deletion of their personal data.
Data privacy is governed by various regulations, such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States. These regulations aim to protect individuals’ privacy rights and hold organizations accountable for their data-handling practices. Companies should also stay up to date on more targeted laws that may affect data privacy and security within countries or industries, as well as policies and guidelines, like those levied by business partners.
Read about marketing data privacy now.
What’s the difference between data privacy and security?
While companies need to have robust systems to manage both data security and data privacy, and while to the layperson they may seem interchangeable, it’s important to understand the differences to develop effective strategies and ongoing management for both.
As you can see, data privacy and data security are distinct but closely related concepts that work together to protect a user’s information, their data, and a company’s business operations, reputation, and finances.
Effective data protection requires a comprehensive approach that considers both aspects. For instance, strong security measures are necessary to ensure data privacy, while privacy concerns guide how security measures are put in place and communications with data subjects.
Read about privacy-enhancing technologies now
Practical data privacy examples
The term data privacy is broadly used, and perhaps not always well understood, as it involves government regulation, companies’ marketing operations, individuals’ activities online, and more. However, let’s explore a couple of data privacy examples to see how it is applied.
For starters, social media platforms like Facebook and Instagram allow users to control who can see their posts and personal information. This control is a fundamental aspect of data privacy, granting individuals the power to manage their own data.
Interestingly, when users of social platforms do not use any privacy settings and all their posted content, replies, etc. are fully public, under some privacy laws this is considered “publicly available information” and likely not considered “personal information” protected by data privacy laws.
Another example is cookie consent banners on websites, which ask for user consent and notify users about data use before collecting tracking data for advertising, analytics, and other uses. This practice aligns with the principles of transparency and consent, ensuring users are informed about how their data will be used.
The GDPR and many other privacy laws empower individuals to exercise their rights over personal data, including the right to request access to all the data a company holds about them.
Individuals can also take advantage of newer and more privacy-focused web browsers and other tools that prevent them from being tracked online. These tools can often directly interface with a company’s consent management solution to signal the user’s consent preferences (or rejection) so they don’t have to provide them every time they go to a new website. This is known as the universal opt-out mechanism, a popular version of which is the Global Privacy Control.
These examples demonstrate some ways that individuals can protect their privacy online, and how organizations can implement data privacy principles to respect individual rights and build trust with their users.
Read about marketing data mining now
Common data security examples and measures
Data security measures are diverse and can be implemented across companies, but also on an individual level. For instance, two-factor authentication adds an extra layer of security by requiring individuals to provide two different authentication factors to verify their identity. It’s commonly used to access accounts on websites and apps to significantly reduce the risk of unauthorized access.
End-to-end encryption is another critical security measure, ensuring that only the intended recipients can read messages sent over communication channels. This type of data security measure is implemented on apps like WhatsApp and iMessage to protect user privacy by preventing unauthorized access or interception of messages, even by the service providers themselves. This ensures that the content of the communication remains confidential, safeguarding sensitive information from potential hackers, government surveillance, or other third parties.
Biometric authentication is another common data security measure. It uses unique physical characteristics like fingerprints or facial recognition, which is increasingly common in securing access to devices and systems.
Many data privacy laws require companies to implement administrative, technical, and physical means of data protection. In addition to pursuing broader compliance with the laws, these measures include encryption of data, access controls for systems and accounts, and regular audits and assessments. They also involve regular employee training and comprehensive response plans for incidents like data breaches.
Such data security measures work together to create multiple layers and types of protection against potential threats and unauthorized access.
Read about marketing data privacy now
Navigating data privacy in the United States
The United States has a sectoral approach to data privacy legislation. This means that laws relating to data privacy are created according to the needs of one particular industry or segment of the population. For example, by industry or for residents of a specific state.
Therefore, companies that operate in the US need to be aware of certain data privacy regulations. As of mid-2024, not quite half of US states have passed data privacy laws. Get the full overview of which states have regulations in place and their individual requirements: US data privacy laws by state – rights and requirements.
The US also has several sector-specific privacy laws, such as the Health Insurance Portability and Accountability Act (HIPAA) for healthcare data and the Gramm-Leach-Bliley Act (GLBA) for financial information. The state-level laws generally defer to these laws where relevant, similarly to how they defer to the Children’s Online Privacy Protection Act (COPPA) for handling data belonging to children.
There is currently no comprehensive federal privacy law in the US. However, discussions are ongoing about drafted national privacy legislation that would harmonize the various state-level regulations and likely supersede many of their requirements.
Data privacy regulations in Europe
Implemented in 2018, the GDPR is one of the strictest data privacy regulations in the world and has set a global standard for privacy protection and has been influential on several laws passed after it.
There are some key aspects of the GDPR that companies and website owners need to be aware of.
- Extraterritorial scope: The GDPR applies to organizations processing personal data of EU residents, regardless of the organization’s location.
- Data subject rights: EU residents have extensive rights, including the right to access, rectify, and erase their personal data.
- Consent requirements: Organizations must obtain prior, explicit, informed consent for data processing activities.
- Data protection by design and default: Privacy considerations must be integrated into the development of products and services from the outset.
- Data breach notification: Organizations must report certain types of data breaches to supervisory authorities and affected individuals within 72 hours.
Best practices for data security
Now that we’ve covered the basics of data privacy and security and have seen how they apply to individuals and businesses, let’s dive into the best ways to put these principles into action. Because data security is critical, and to establish a data security framework at your company, there are certain best practices you can follow. By implementing these, companies can significantly enhance their data security position and reduce the risk of data breaches and cyberattacks.
Encrypt data
Implement encryption for data at rest and in transit to protect it from unauthorized access. Ensure that encryption keys are properly managed and stored securely, separate from the encrypted data. Regularly review and update encryption protocols to stay ahead of emerging threats and comply with industry standards.
Regularly update and patch systems
Keep all software, operating systems, and applications up to date to address known vulnerabilities. Implement a structured patch management process to prioritize and apply updates promptly. Consider using automated patch management tools to streamline the process and ensure consistent application across all systems.
Conduct regular security assessments
Perform vulnerability scans, penetration testing, and security audits to identify and address potential weaknesses. Establish a regular schedule for these assessments to maintain a proactive security posture. Use the results of these assessments to inform and prioritize security improvements and investments.
Develop an incident response plan
Create and regularly test a plan for responding to security incidents and data breaches. Include clear roles and responsibilities for team members, communication protocols, and steps for containment, eradication, and recovery, as well as external communications to authorities and affected users as needed. Conduct tabletop exercises and simulations to ensure the team is prepared to execute the plan effectively when needed.
Monitor and log activity
Implement logging and monitoring systems to detect and investigate suspicious activities. Use Security Information and Event Management (SIEM) tools to centralize and analyze log data from various sources across the network. Establish baseline activity patterns and set up alerts for anomalies that may indicate potential security incidents.
Educate employees
Provide regular security awareness training to employees to help them recognize and respond to potential threats. Use a variety of training methods, including interactive online courses, simulated phishing exercises, and in-person workshops to reinforce key security concepts. Regularly update training content to address emerging threats and evolving best practices.
Secure mobile devices and remote access
Implement mobile device management and secure remote access solutions to protect data accessed outside the office. Develop and enforce clear policies for bring-your-own-device and remote work scenarios. Use virtual private networks and multi-factor authentication to secure connections from remote locations. Also, ensure that any lost or stolen devices can be remotely locked down or wiped.
Manage third-party risks
Assess and monitor the security practices of vendors and partners who have access to your data or have integrations with your systems. Develop a comprehensive vendor risk management program that includes regular security assessments, contractual security requirements, and ongoing monitoring. Establish clear incident reporting and response procedures for third-party security incidents that may affect your organization’s data.
Many data privacy laws require contractual agreements to be in place with third-party processors before any data processing begins. However, such laws also tend to hold the data controller for which third parties are working as ultimately responsible if there is a breach or other privacy violation.
Best practices for data privacy compliance
As we’ve seen, multiple regulations dictate a company’s efforts and must-haves related to data privacy. To avoid hefty fines or other disruptive penalties and avoid loss of trust by customers and the company’s brand reputation, there are some best practices website owners, app publishers, and others should follow.
Conduct data privacy impact assessments (DPIA)
Regularly assess the privacy risks associated with new products, services, or data processing activities. Document the findings and recommendations from these assessments to guide decision-making and risk mitigation efforts. Use the results to inform privacy-enhancing modifications to processes, technologies, or policies before implementation.
Many data privacy laws clearly outline when DPIAs are recommended, and when they are legally required, e.g. when performing high-risk processing or processing of sensitive data.
Develop clear privacy policies
Create transparent, easily understandable privacy policies that clearly communicate how personal data is collected, used, and shared. Use plain language and avoid legal jargon to ensure policies are accessible to all users. Don’t forget to regularly review and update privacy policies to reflect changes in data practices or regulatory requirements.
Obtain and manage consent
Implement a consent management platform (CMP) to ensure that individuals have control over how their data is used. A CMP like Usercentrics enables you to design user-friendly cookie banners, increase your opt-in rate, and provide you with +2,000 legal templates, all while respecting various global data privacy regulations. A consent management platform also keeps detailed records of consent in case your company is audited.
Limit data collection, use, and storage
Collect only the personal data that is necessary for specific, legitimate purposes that have been communicated, and retain it only as long as needed to complete those purposes. Regularly review data collection practices to identify and eliminate unnecessary data points. Consider implementing data minimization techniques and privacy mechanisms like data anonymization when possible to reduce privacy risks.
Implement data retention policies
Establish and enforce policies for retaining personal data only as long as necessary for the specified purposes. Develop clear guidelines for data deletion or anonymization when retention periods expire, which include any third-party processors. Implement automated systems to flag data for review or deletion based on retention schedules.
Train employees on privacy best practices
Educate employees about privacy regulations, best practices, and their role in protecting personal data. Consider developing role-specific training programs that address the unique privacy considerations for different departments or job functions. Conduct regular refresher courses and updates to keep employees informed, and provide safe mechanisms for employees to ask questions or report concerns.
Conduct regular privacy audits
Perform periodic audits and ongoing dialog with legal representatives or data privacy experts to ensure ongoing compliance with privacy policies and regulations, especially as company operations and technologies in use change.
Use the audit findings to identify areas for improvement and update privacy practices accordingly. Consider engaging external auditors or privacy experts to provide independent assessments of your organization’s privacy program, especially for small businesses that may not have in-house resources.
Embracing data privacy and security
In an era where data breaches and privacy concerns are increasingly common, prioritizing data privacy and security is no longer optional: it’s a necessity. Especially combined with ever-evolving privacy regulations. By understanding the distinctions between data privacy and security and implementing best practices in both areas, organizations can protect their valuable information assets, maintain customer trust and brand reputation, and navigate the complex regulatory landscape.
Additionally, by implementing data privacy and data security practices, companies not only protect against potential threats but can also use this as a competitive advantage. Such measures demonstrate an organization’s commitment to ethical data handling and customer trust, which is also increasingly attractive to potential partners, and required by large tech platforms companies rely on for advertising, audience access, and more.
Minnesota became the nineteenth state in the United States to pass a consumer privacy bill with the Minnesota Consumer Data Privacy Act (MCDPA) when Governor Tim Walz signed it into law on May 24, 2024. The law goes into effect on July 31, 2025, with the compliance deadline extended to July 31, 2029 for postsecondary institutions regulated by the Minnesota Office of Higher Education.
We look at how the MCDPA protects consumers’ information, and the broader implications for organizations under its jurisdiction.
What is the Minnesota Consumer Data Privacy Act (MCDPA)?
The Minnesota Consumer Data Privacy Act (MCDPA) is a regulation designed to protect the privacy and personal data of Minnesota’s residents by regulating how data is collected, processed, and used. The state-level law imposes specific obligations on businesses that either operate in Minnesota or offer products and services to its residents, known as “consumers” under the law, and process their personal data.
Under the MCDPA, a consumer is “a natural person who is a Minnesota resident acting only in an individual or household context.” The law explicitly excludes any natural person acting in a commercial or employment context.
Like most other US states with similar laws, Minnesota follows an opt-out consent model. Businesses must clearly inform consumers about:
- what personal data they collect
- the purpose(s) for collecting this data
- any third parties with whom the data may be shared
- how consumers can opt out of the collection and processing of their personal data for specific purposes.
Who must comply with the Minnesota Consumer Data Privacy Act?
The Minnesota privacy law applies to businesses that operate in the state and produce products or services targeted at Minnesota residents, and during a calendar year:
- control or process the personal data of at least 100,000 consumers, except if the personal data is controlled or processed only for the purposes of completing a payment transaction
or - control or process the personal data of at least 25,000 consumers and derive more than 50 percent of gross revenue from the sale of personal data
The MCDPA applies to any business that fulfills these conditions, regardless of where the business is located.
Minnesota data privacy law sets itself apart from some other state laws such as the California Consumer Privacy Act (CCPA) / California Privacy Rights Act (CPRA), as it does not require businesses to comply based on annual revenue alone.
Exemptions to Minnesota Consumer Data Privacy Act compliance
The Minnesota data privacy law exempts certain entities from complying, including:
- government entities
- federally recognised Indian tribes
- covered entities or business associates governed by the Health Insurance Portability and Accountability Act (HIPAA)
- state or federally chartered banks or credit unions, or their affiliates or subsidiaries primarily engaged in financial activities
- insurance companies, insurance producers, third-party administrators of self-insurance, or their affiliates or subsidiaries primarily engaged in financial activities
- small businesses as defined under the U.S. Small Business Act, unless they sell consumers’ sensitive data without obtaining prior consent
- air carriers subject to the Airline Deregulation Act where the personal data collected relates to prices, routes, or services
- nonprofit organizations established to detect and prevent insurance fraud
Data that is exempt from the law includes:
- protected healthcare-related information, research data, and employment-related data
- data collected or maintained as emergency contact information for a natural person if used for emergency contact purposes only
- data created for or collected under several federal laws, including, among others:
- Gramm-Leach-Bliley Act (GLBA)
- HIPAA
- Health Care Quality Improvement Act
- Family Educational Rights and Privacy Act (FERPA)
- Farm Credit Act (FCA)
- Minnesota Insurance Fair Information Reporting Act
- Driver’s Privacy Protection Act
- Fair Credit Reporting Act (FCRA)
Definitions under the Minnesota Consumer Data Privacy Act
The Minnesota privacy law defines key terms that explain the types of data it covers and the data processing activities involved.
Personal data under the MCDPA
The Minnesota privacy law defines personal data as “any information that is linked or reasonably linkable to an identified or identifiable natural person.” The definition specifically excludes de-identified data or publicly available information.
Common types of personal data that businesses collect include name, phone number, email address, Social Security number, or driver’s license number.
Sensitive data under the MCDPA
Sensitive data is personal data that could harm consumers if abused. Under the MCDPA, it includes:
- racial or ethnic origin
- religious beliefs
- mental or physical health diagnosis
- sexual orientation
- citizenship or immigration status
- genetic or biometric data processed for the purpose of uniquely identifying an individual
- personal data collected from a known child (under 13 years of age)
- precise geolocation data that can accurately identify an individual’s specific location within an accuracy of more than three decimal degrees of latitude and
- longitude or the equivalent in an alternative geographic coordinate system, or a street address derived from the coordinates
Controller under the MCDPA
Controller under Minnesota’s privacy law is “a natural or legal person who, alone or jointly with others, determines the purpose and means of processing personal data.“
A controller, also known as a “data controller” under some laws, is responsible for protecting personal data under the law.
Processor under the MCDPA
A processor under the law is “a natural or legal person who processes personal data on behalf of a controller.”
Sale of personal data under the MCDPA
Sale of personal data means “the exchange of personal data for monetary or other valuable consideration by the controller to a third party.“
The MCDPA’s definition specifically excludes the following:
- disclosure of personal data to a processor that processes the personal data on the controller’s behalf
- disclosure of personal data to a third party for the purposes of providing a product or service the consumer has requested
- disclosure or transfer of personal data to the controller’s affiliate
- disclosure of information that the consumer has intentionally made available to the public through a mass media channel not restricted to a specific audience
- disclosure or transfer of personal data to a third party as an asset that is part of a proposed or completed merger, acquisition, bankruptcy, or other transaction
- exchange of personal data between the producer of goods or services and its authorized agents who sells these goods and services, to enable both parties to provide the goods and services
Targeted advertising under the MCDPA
The MCDPA defines targeted advertising as “displaying advertisements to a consumer where the advertisement is selected based on personal data obtained or inferred from the consumer’s activities over time and across nonaffiliated websites or online applications to predict the consumer’s preferences or interests.”
Targeted advertising under the MCDPA does not include:
- ads based on activities within a controller’s own websites or online apps
- ads based on the context of a consumer’s current search query, visit to the website, or online app
- ads directed to a consumer in response to the consumer’s request for information or feedback
- processing of personal data solely for measuring or reporting ad performance, reach, or frequency
Consent under the MCDPA
The Minnesota privacy law defines consent as “any freely given, specific, informed, and unambiguous indication of the consumer’s wishes by which the consumer signifies agreement to the processing of personal data relating to the consumer.”
Excluded from the definition are:
- acceptance of a general or broad terms of use or similar document that contains descriptions of personal data processing along with other, unrelated information
hovering over, muting, pausing, or closing a given piece of content - consent obtained through the use of dark patterns
Consumer rights under the Minnesota Consumer Data Protection Act
Consumers have several rights under the MCDPA that enable them to protect their personal data and control how it’s used, in particular:
- Right to access: consumers can confirm if the controller is processing their personal data and can access this data, with some exceptions
- Right to correction: consumers have the right to have any inaccurate personal data about them corrected, taking into account the nature of the personal data and purposes of processing
- Right to deletion: consumers can request the deletion of their personal data, with exceptions
- Right to data portability: where the processing is carried out by automated means, consumers can obtain a copy of their personal data that they previously provided to the controller, in a portable and readily usable format, with some exceptions
- Right to information: consumers can obtain a list of specific third parties to whom the controller has disclosed their, or any consumer’s, personal data
- Right to opt out: consumers can opt out of the processing of their personal data for the purposes of its sale or use for targeted advertising or profiling
Consumers have the following additional rights if their data is used for profiling that affects legal decisions about them:
- to question the outcome of the profiling
- to know why the profiling led to that outcome
- if possible, to learn what actions they could have taken to achieve a different outcome and what they can do in the future to achieve such an outcome
- to review the personal data used in the profiling, and, if the decision was based on incorrect data, to correct this data and request a reevaluation of the profiling decision with the corrected data
There is no private right of action that gives consumers the right to directly sue a controller for violations of the Minnesota privacy law.
Controllers’ obligations under the Minnesota Consumer Data Privacy Act
Under the Minnesota data privacy law, controllers are required to meet specific obligations to protect consumers’ personal data.
Consumer rights requests under the MCDPA
Controllers must provide one or more secure and reliable methods for consumers to exercise their rights. While consumers can be asked to log in to an existing account for identity verification, requiring them to create a new account is not permitted under the law.
Controllers have 45 days to respond to consumer requests, with the option to extend this period by another 45 days if reasonably necessary. If an extension is required, the controller must inform the consumer before the initial 45-day period expires.
If the controller is unable to reasonably verify the consumer’s identity, they may request additional verification or decline the request. In cases where a request is declined, the controller must notify the consumer within 45 days of receiving the request, providing the reason for the denial and information on how to appeal the decision.
Controllers must respond to appeals within 45 days, and they may extend this period by an additional 60 days if reasonably necessary. If an appeal is denied, the controller must provide a written explanation with reasons for denial and inform the consumer how to submit a complaint to the Attorney General.
Controllers are required to maintain records of all appeals and their responses for a minimum of 24 months, and they must provide the Attorney General with copies of the records if requested.
Privacy notices under the MCDPA
Under the Minnesota data privacy law, controllers must publish a clear, accessible, and comprehensive privacy notice that includes the following information:
- categories of personal data processed
- purposes for processing personal data
- what rights consumers have under the law
- how consumers may exercise their rights
- how consumers may appeal the controller’s decision regarding a request
- categories of personal data sold to or shared with third parties, if any
- categories of third parties to whom the controllers sells or shares personal data, if any
- contact information for the controller
- a description of the controller’s retention policies for personal data
- date of the last update to the privacy notice
Controllers that sell consumers’ personal data to third parties, or process personal data for targeted advertising purposes or profiling, must disclose this in the privacy notice. They must also provide consumers with a prominent method to opt out of the sale, processing, or profiling for these purposes. A link provided for these purposes must use the words “Your Opt-Out Rights” or “Your Privacy Rights”.
Typically, the privacy notice or privacy policy is posted in a highly visible location on the controller’s website, such as the footer, ensuring it’s easy to locate. The MCDPA mandates that controllers use the word “privacy” in the link to the privacy notice on a website, mobile app’s app store page, or download page.
The MCDPA also requires controllers who maintain apps — whether they’re mobile, tablet, web, or smart device apps — to include a link to the privacy notice in the settings menu of the app.
If a controller doesn’t maintain a website, they must make the privacy notice accessible to consumers through the regular means of communication with them, which may include postal mail.
Purpose limitation under the MCDPA
The law requires controllers to disclose the specific purposes for which they are collecting personal data and to restrict their data collection to what is “adequate, relevant, and reasonably necessary” for these identified purposes. Controllers cannot retain personal data if it is no longer needed for the original purposes of collection and processing, unless the law requires or permits it in certain circumstances.
Data security under the MCDPA
Controllers have an obligation to protect the confidentiality, integrity, and accessibility of consumers’ personal data. The Minnesota data privacy law requires controllers to establish, implement, and maintain reasonable administrative, technical, and physical security measures for this purpose, which are appropriate to the volume and nature of the personal data being processed.
Notably, Minnesota is the first state to mandate that controllers maintain data inventories to fulfill these requirements.
Compliance policies and data privacy and protection assessments under the MCDPA
Controllers are required to document a description of the policies and procedures adopted to comply with the MCDPA, including:
- name and contact information for the controller’s chief privacy officer, or, if one is not appointed, another individual with responsibility to monitor and achieve
- the controller’s compliance with the law
- description of the controller’s data privacy policies and procedures that enable controllers to fulfill their obligations under the law
- description of any policies and procedures established to:
- ensure that their systems are designed to comply with the law
- identify and provide personal data to a consumer as required under the law
- comply with the obligation for ensuring data security
- comply with the obligation for purpose limitation
- prevent data that is no longer required from being retained unless required by law
- identify and rectify violations of the law
The MCDPA also requires controllers to conduct and document a data privacy and protection assessment, known as a data protection impact assessment under some laws, when processing personal data:
- for the purposes of targeted advertising
- for sale
- classified as sensitive data under the law, including children’s data
- that presents a heightened risk of harm to consumers
- for profiling that presents a reasonably foreseeable risk of the following on consumers:
- unfair or deceptive treatment, or disparate impact
- financial, physical, or reputational injury
- physical or other intrusion into private affairs
- other substantial injury
Data privacy and protection assessments under the MCDPA must include the description of policies and procedures that the controller has adopted to comply with the law.
The Attorney General can request the controller to disclose a data privacy and protection assessment during its investigations into any alleged violations, and the controller is obligated to make it available.
The law considers data privacy and protection assessments or risk assessments conducted by a controller for compliance with other laws as valid if the assessments share a similar scope and effect.
Consent requirements under the MCDPA
Minnesota has adopted an opt-out model for processing personal data, consistent with the other US state-level privacy laws. This means that controllers can collect and process personal data without obtaining prior consent from consumers in most cases. However, an important exception exists for sensitive personal data, where controllers must obtain explicit consent before processing.
Controllers must clearly inform consumers about their data processing activities and provide options for consumers to opt out of the sale of their personal data and its use for targeted advertising or profiling. Additionally, Minnesota law mandates that controllers provide an effective way for consumers to revoke previously given consent. This revocation mechanism must be as easy to use as the method used to give consent initially. Once consent is revoked, controllers are required to stop processing the relevant data as soon as practicable, and no later than 15 days after receiving the revocation request.
The MCDPA aligns with the Children’s Online Privacy Protection Act (COPPA) concerning children’s personal data, which is standard among US data privacy laws. This requires controllers to obtain consent from a parent or guardian before processing any personal data of children under 13 years old, as all personal data of children in this age group is classified as sensitive data under Minnesota law.
Controllers are prohibited from processing the personal data of consumers known to be between the ages of 13 and 16 for the purposes of targeted advertising or selling their data without obtaining prior consent from the individual.
Nondiscrimination under the MCDPA
The MCDPA explicitly prohibits controllers from discriminating against consumers who exercise their rights under the law. This means businesses cannot deny goods or services, charge different prices or rates for goods or services, or offer varying quality levels or experiences (e.g. website access) to consumers based on their choices to exercise their data privacy rights.
However, controllers may offer incentives, such as discounts or rewards, to consumers who voluntarily participate in activities involving the processing of personal data. These incentives must be reasonable and proportionate to avoid being considered coercive rather than optional and voluntary.
Certain website functions that rely on essential or necessary cookies may not operate effectively if a consumer declines these cookies. Such limitations are not regarded as discriminatory under the law.
Controllers are not obligated to provide a product or service that depends on personal data they do not collect or keep.
The MCDPA specifically prohibits controllers from processing personal data on the basis of certain characteristics, including, among others, race, ethnicity, religion, gender identity, familial status, or disability in a manner that unlawfully discriminates against consumers with respect to the provision of:
- housing, employment, credit, or education
- goods, services, facilities, privileges, advantages, or accommodations of any place of public accommodation
Data processing agreement under the MCDPA
The Minnesota privacy law requires controllers to enter into contracts with processors that govern data processing procedures. While the law does not explicitly use the term “data processing agreement,” this contract serves the same purpose as data processing agreements in other data privacy laws, such as the European Union’s General Data Protection Regulation (GDPR) and the Virginia Consumer Data Protection Act (VCDPA).
The contract or data processing agreement must clearly outline:
- instructions for processing data
- nature and purpose of processing
- type of data subject to processing
- duration of processing
- rights and obligations of both parties
- processor’s duty of confidentiality
- conditions under which the processor may engage a subcontractor
Processors must assist controllers in meeting their obligations under the MCDPA, including ensuring security of personal data being processed.
Universal opt-out mechanism under the MCDPA
Similar to data privacy laws in states like California, Nebraska, and Texas, the MCDPA includes provisions for universal opt-out mechanisms, such as the Global Privacy Control (GPC). These mechanisms enable consumers to set their privacy preferences once via browser settings or extensions, and these preferences are then automatically applied to all websites and online services they visit.
Under the MCDPA, controllers must respect universal opt-out signals that express a consumer’s choice to opt out of activities such as targeted advertising or the sale of personal data. Controllers that recognize opt-out preference signals approved by other state laws or regulations will be deemed compliant with this requirement under the MCDPA.
The law requires that the mechanism a controller employs must:
- not unfairly disadvantage another controller
- require consumers to make “an affirmative, freely given, and unambiguous choice“ to opt out rather than use a default opt-out setting
- be user-friendly
- be consistent with other similar technologies or mechanisms
- enable the controller to determine whether the consumer is a resident of Minnesota, either through the consumer’s IP address or other means, and has made a
- legitimate opt-out request
Enforcement of the Minnesota Consumer Data Privacy Act
The Minnesota Attorney General has exclusive authority to enforce the MCDPA. While the law does not grant consumers a private right of action, they can still file complaints about alleged violations or denials of their privacy rights directly with the Attorney General’s office. Before initiating an enforcement action, the Attorney General must issue a written notice to the implicated party, detailing the alleged violations.
The MCDPA includes a 30-day cure period for organizations to address and rectify any alleged violations after receiving the notification. This cure period has a sunset date of January 31, 2026, after which this provision will no longer apply, and any cure period will be at the discretion of the Attorney General’s office.
Fines and penalties under the MCDPA
The Minnesota Attorney General can initiate enforcement actions against controllers or processors if they fail to remedy a violation within the 30-day cure period. An enforcement action might include seeking injunctive relief and/or imposing civil penalties, which can reach up to USD 7,500 per violation, along with recovering reasonable costs related to investigating the violation.
Consent management and the Minnesota Consumer Data Privacy Act
Like consumer privacy laws in other US states, the Minnesota privacy law adopts an opt-out consent model. This means businesses can collect and process personal data without obtaining prior consent, except for sensitive personal data and data belonging to children.
Consumers have the right to opt out of the collection and processing of their personal data for purposes such as sale, targeted advertising, or profiling. Businesses are required to clearly present this opt-out option on their websites, typically within the privacy policy or privacy notice.
Many websites use cookie consent banners that include clear links or buttons that enable users to opt out of data processing. A consent management platform (CMP) like Usercentrics CMP can automate this process by managing cookies and other tracking technologies and blocking their use until the consumer gives consent, or by enabling opt-out, depending on the relevant legal model.
CMPs also enable websites to offer clear information to users regarding the types of data collected, the purposes for collection, and the third parties that might receive this data, in line with the MCDPA and other data privacy regulations.
Since there is currently no unified federal privacy law in the US, businesses that operate around the country and/or internationally likely need to comply with multiple state and international privacy regulations. CMPs can assist in this by customizing cookie banners based on the user’s location, helping businesses meet the requirements of state-level laws like the MCDPA as well as international regulations such as the GDPR.
Preparing for the Minnesota Consumer Data Privacy Act
Businesses operating in Minnesota have until the effective date of July 31, 2025, to prepare for compliance with the MCDPA. Those that are already compliant with privacy regulations in other states may find themselves ahead, as there are several overlapping requirements. However, businesses must also prepare for specific MCDPA provisions, such as the obligation to maintain data inventories and to document data privacy policies and processes. Integrating a privacy by design approach not only benefits compliance efforts but also enhances overall organizational operations.
Companies must assess whether they meet the MCDPA compliance thresholds, and, if applicable, take steps to provide users with clear opt-out options and accessible privacy notices. Using a Consent Management Platform (CMP) like Usercentrics CMP can assist in managing cookies on websites and apps.
As the MCDPA adapts to technological advancements and shifts in consumer expectations, it is crucial for businesses to consult with qualified legal professionals or data privacy experts, such as a Data Protection Officer, to maintain compliance.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.
The California Consumer Privacy Act (CCPA) set US standards for consumer privacy and data protection. It requires businesses that operate in digital markets to establish compliant data collection practices, communicate these to their customers, and implement measures to protect this data.
Meeting CCPA requirements can entail a large investment of time and resources, but failing to adhere to its provisions can be even more costly. The fines, legal fees, and loss of customer trust that stem from noncompliance are significant risks to your business’s bottom line.
Compliance tools are invaluable in helping you adhere to CCPA requirements. They simplify privacy compliance by streamlining consent collection, management, and signaling according to regulatory requirements, so that you can remain focused on your core business operations.
Our picks of the top CCPA compliance software:
Essential features for CCPA compliance solutions
Complying with the CCPA helps your business to protect consumer rights and build customer trust while also safeguarding it against various noncompliance risks, including CCPA class action lawsuits.
Using a robust CCPA compliance tool can help you to meet the requirements of this regulation and the California Privacy Rights Act (CPRA), which expanded and amended it. When choosing your platform, it’s important to evaluate the following features.
- Consent management: A consent management platform (CMP) enables you to securely collect, manage, and signal user consent in line with CCPA requirements.
- Sensitive data handling: Look for features that help identify, secure, and manage the processing of sensitive personal information.
- Data processing: Ensure there are mechanisms for monitoring and controlling the processing of personal data so it meets the CCPA’s transparency, purpose limitation, and data minimization requirements.
- Data privacy management: Make sure there are comprehensive privacy management tools available to maintain compliance documentation, automate scanning for technologies in use that require consent, keep consent notices up to date, and manage consent choices in real-time.
| CCPA tool | Key features | Usability score | Recommended for |
|---|---|---|---|
| Usercentrics |
|
4.0/5 (Capterra) | Businesses of all sizes |
| TrustArc |
|
4.1/5 (SoftwareReviews) | Small to medium-sized businesses |
| OneTrust |
|
3.8/5 (Capterra) | Large corporations |
| Osano |
|
4.6/5 (G2) | Freelancers |
| iubenda |
|
4.5/5 (Capterra) | Small businesses |
| Ketch |
|
4.5/5 (G2) | Agencies |
6 great tools for CCPA compliance
Maintaining compliance with the CCPA doesn’t have to be a daunting task. Here are six tools designed to help you adhere to stringent data privacy laws efficiently so you can focus on what you do best — run your business.
1. Usercentrics
Usercentrics is an all-in-one CMP that enables compliance with the CCPA, GDPR, and other major data privacy laws. It features more than 2,200 legal templates to save time and resources during implementation and maintenance.
This powerful solution integrates easily with popular content management systems (CMSs) and web builder platforms. It enables privacy compliance right out of the box, and you can also customize it extensively, from visual branding to regulatory coverage and more.
However, note that the extensive feature set can make it somewhat challenging for new users to master initially.
Top features
- DPS Scanner: Identify third-party cookies and other tracking technologies on your website to ensure that you’re informing users about the services in use and that you’re able to control them in line with users’ consent choices.
- Legal templates: Access 2,200+ ready-to-use or customizable legal templates to save time on setup, categorization, and maintenance.
- Google-certified: Comes with Google Consent Mode v2 integrated and ready to use.
- Cross-domain and cross-device consent: Improve user experience by obtaining consent for all your websites and apps with a single consent interaction.
- Robust analytics: Get a detailed view of user interaction and consent rates to drive informed decision-making and optimize opt-ins.
Pricing plans
Usercentrics offers a 30-day free trial, after which users can sign up for one of the following paid plans.
- Starter: USD 60/month for up to 50,000 sessions
- Advanced: USD 175–1,150/month for 50,000+ sessions
- Premium: Custom pricing
| Full UI customization | Analytics data only available for 90 days |
| Automated third-party cookie blocking | |
| Flexible pricing and packages |
2. TrustArc

TrustArc provides businesses with automated privacy solutions to help them achieve compliance while increasing user trust. Once it’s up and running, the platform is easy to implement at scale, but you may have to invest significant time to overcome a learning curve to unlock its full potential.
Top features
- Auto-law identification: Gain a better understanding of privacy regulations and standards so you can maintain compliance.
- Trust Center: Display all CCPA-related data privacy information in one place to build trust with your customers.
- Multiple APIs: Integrate third-party applications and tools into your website with Rapid and REST APIs for compliant data collection.
Pricing plans
Contact TrustArc for pricing.
| Google-certified CMP provider | Poor customer support, according to some users |
| Easy to use (G2 user reviews) | |
| Drag-and-drop customization |
3. OneTrust

With an extensive set of privacy management tools, OneTrust enables businesses to safely handle customer data while minimizing security, privacy, governance, and compliance risks. The tool’s automation features can reduce the complexity involved in staying compliant, but you may experience implementation challenges, according to some users.
Top features
- Data intelligence: Centralize and organize data to easily identify sensitive information and understand potential risks.
- Data mapping: Gain an understanding of how data flows through your organization to enable the implementation of CCPA-compliant measures at every stage of handling.
- Reporting and logs: Be prepared for an audit and equipped to show that your business is in compliance with CCPA requirements.
Pricing plans
Contact OneTrust for pricing.
| Vendor risk management | Pricing information not publicly available |
| Automated compliance assessments | |
| Incident and breach management |
4. Osano

Osano enables more than 40,000 users to meet the requirements of data privacy laws. Although it offers an all-in-one solution that centralizes CCPA compliance management, some users note that customization options are limited.
Top features
- “No Fines, No Penalties” Pledge: Claim up to USD 200,000 compensation for any data privacy-related fines or penalties incurred while using Osano.
- Automated data request workflows: Collect, track, and fulfill customers’ requests to disclose, access, or delete the personal information you have on hand, as required by the CCPA.
- Regulatory alerts: Get updates about upcoming changes to the CCPA and other data privacy laws to stay ahead of requirements and maintain compliance.
Pricing plans
Osano has two self-service cookie consent packages:
- Free: USD 0/month for 1 user, 1 domain, and up to 5,000 visitors/month
- Plus: USD 199/month for 2 users, 3 domains, and up to 30,000/month
Contact Osano for pricing for the Privacy & Trust Assurance, Privacy Essentials, and Privacy Operations & Government plans.
| Secure blockchain storage | Free plan only supports 5,000 monthly visitors |
| Geolocation capabilities | |
| Easy setup (G2 user reviews) |
5. iubenda
iubenda’s CMP offers what they refer to as attorney-level consent management tools that help businesses take the guesswork out of compliance. However, geolocation-based consent settings, which are important for tailoring consent banners to user location, aren’t available on all plans.
Top features
- Privacy policy generator: Produce legally compliant documents that detail your business’s data handling practices.
- Automatic policy updates: Be informed of regulatory changes with automatic policy updates drafted and implemented by attorneys.
- Consent database: Save and manage user consent choices as required by the CCPA and CPRA.
Pricing plans
iubenda provides a free plan for websites with fewer than 5,000 page views per month. They also offer a free 14-day money-back guarantee on their three paid packages. Pricing is as follows:
- Essentials: USD 5.99/month/site or app
- Advanced: USD 24.99/month/site or app
- Ultimate: USD 99.99/month/site or app
| Automatic updates to maintain compliance | Only one language included with the Essentials plan |
| Chat and email support | |
| Centralized dashboard for managing multiple websites |
6. Ketch

Ketch is a design-first CMP that places emphasis on the look and feel of data privacy notices, as well as compliance requirements. This US provider’s no-code solutions are aimed at teams that don’t have much technical expertise, but some users note that the platform has a learning curve and its interface is sometimes confusing.
Top features
- Identity resolution: Recognize users across digital channels and devices and automatically apply their consent preferences.
- Ketch Smart Tag: Add privacy notices to your website with lightweight script that aligns with current web design best practices.
- Ketch permit vault: Access up to date records of your customers’ privacy choices and retrieve records of processing activities with one click.
Pricing plans
Ketch offers three plans at three different price points:
- Ketch Free: USD 0
- Ketch Essentials: From USD 350/month
- Ketch Pro: Contact Ketch for pricing
| No-code solution | Free plan only supports 5,000 monthly visitors |
| Easy to use (G2 user reviews) | |
| Over 1,000 pre-built integrations |
How to stay CCPA-compliant with a consent management platform
Managing customers’ personal information, collecting user data, and implementing and maintaining data security in line with the CCPA is a complex and demanding task. A CMP reduces the burden of compliance by automating and streamlining the processes involved in data collection and helping to ensure that they adhere to regulatory standards.
With a CMP, businesses can efficiently establish whether they’re compliant with the CCPA and identify specific actions for achieving compliance. This significantly reduces the hassle and risk associated with adhering to this complex regulation.
Usercentrics for CCPA peace of mind
Complying with the CCPA requires a thorough understanding of the law’s detailed provisions around data collection, storage, and processing. What’s more, growing demands from consumers for the respect for and protection of their data mean that compliance is no longer just a legal requirement but a necessity for business success and longevity.
The recent introduction of the CPRA has further elevated these challenges, building on the CCPA’s requirements. As these laws continue to evolve, businesses need to remain agile and in the know in order to adapt to new guidelines and avoid costly financial and reputational damage.
Usercentrics’ CMP is designed to enable businesses to collect and manage user data in a transparent manner in order to meet the requirements of the CCPA and CPRA. Our Google-certified tool features an extensive library of more than 2,200 legal templates, a best-in-class DPS Scanner, and robust analytics for informed decision-making.
By integrating Usercentrics CMP into your tech stack, privacy compliance can be as seamless as it is robust, and you can align with current regulations, prepare for future changes, and protect your operations and your reputation.
The information presented in this article is accurate based on publicly available sources as of the date of publication. Details about products, features, pricing, etc. may change over time.
Usercentrics does not provide legal advice, and information is provided for educational purposes only. We always recommend engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations.
The ever expanding number of data privacy laws — and their often lengthy and varied lists of requirements — means that a manual approach to meeting and monitoring compliance outcomes is virtually impossible.
To stay ahead of the curve and avoid potential consequences of breaching these regulations, you need effective compliance management software. These tools are key to building privacy compliance into your day to day business practices and managing risk.
We’ve reviewed six tools that can help you streamline your compliance efforts and optimize your data privacy outcomes, so you can select the ideal compliance management software for your business.
When making our selection, we’ve considered factors like consent management features, analytics, and reporting capabilities.
Our top picks for compliance management:
| Compliance management software | Key features | Usability score* | Pricing |
|---|---|---|---|
| Usercentrics |
|
4.7 (Capterra) | From USD 60/month |
| consentmanager |
|
4.2 (Capterra) | Free version available, paid tiers from USD 21/month |
| iubenda |
|
4.5 (Capterra) | From USD 5.99/month |
| Didomi |
|
4.6 (Capterra) | Pricing available on request |
| Osano |
|
4.5 (G2) | Free plan available, Plus plan priced at USD 199/month |
| Cookie Information |
|
4.2 | From EUR 15/month |
*Ease of use scores found via Capterra and/or G2 user reviews
Why are compliance management tools a must in 2024?
Compliance management software enables businesses to comply with data privacy laws by automating tasks once implemented and monitoring regulatory changes. These tools help ensure the process is seamless, requires limited resources, and enable organizations to offer granular consent management options to users.
Failure to adhere to the rules set by various data privacy laws can result in fines. What’s more, the reputational damage that results from noncompliance can lead to a loss of customer trust that can be even more damaging in the long term.
However, you need access to consented data to launch successful marketing initiatives, improve products, and provide the kinds of personalized experiences customers expect. A compliance management solution provides users with the transparency and control they require while meeting compliance criteria and securely storing data according to regulatory requirements.
By automating and streamlining compliance tasks, these specialized tools make compliance easier while reducing the risk of human error.
Our picks for 6 top compliance software solutions
Collating a cookies checklist or data privacy to-do list are just two requirements for companies seeking to become privacy-compliant with relevant regulations. This can be extra challenging for smaller organizations with limited resources. Fit-for-purpose software can help you minimize the burden of achieving and maintaining compliance.
1. Usercentrics
Usercentrics CMP is an industry-leading consent management tool that equips businesses to manage both website and application consent via one interface.
Easily customized consent banners enable granular consent management, which helps organizations stay compliant while delivering a consistent and branded user experience. Interaction Analytics enable businesses to see how users are engaging with consent banners so they can optimize opt-in rates.
Usercentrics is a powerful platform, so there may be a bit of a learning curve for non-technical teams looking to master its more advanced features. That said, there are plenty of useful resources online, and the customer support team is always available to help with troubleshooting.
Key features
- Granular consent management: Give users complete control over the data they share across domains and devices in just a few clicks.
- Robust analytics and reporting: Get detailed information about cookie acceptance rates to enable informed decision-making.
- A/B testing tools: Gain valuable insights into user behavior to optimize your CMP and consent rates.
- Data Processing Service (DPS) Scanner: Identify all third-party technologies that are collecting customer data from your website.
- Google-certified CMP: Comply with Google’s EU user consent policy requirements and integrate with Google Consent Mode v2 by default.
- Geolocation: Serve users consent notices that meet the requirements of their jurisdiction’s data privacy laws based on their location.
Usercentrics pricing
Usercentrics offers a free 30-day trial, after which users can sign up for one of the following paid plans.
- Starter: USD 60/month for up to 50,000 sessions
- Advanced: USD 175–1,150/month for 50,000+ sessions
- Premium: Custom pricing

| 2,200+ legal templates | Analytics data only available for 90 days |
| Full UI customization | |
| 60+ languages supported |
2. consentmanager

consentmanager promises to help businesses increase their cookie acceptance rates by giving users access to in-depth reporting and intelligent A/B testing tools. However, with its main focus on the GDPR, the platform may not be the best option for businesses with global operations.
Key features
- EU servers: Store user consent records on servers located in the EU.
- Automatic cookie deletion: Remove cookies when users reject tracking.
- Time-adjustable re-consent: Set intervals for users to reconfirm tracking consent.
consentmanager pricing
- Basic: USD 0 for up to 5,000 pageviews/month on 1 website.
- Beginner: USD 21/month for up to 100,000 pageviews/month on 1 website.
- Standard: USD 53/month for up to 1 million pageviews/month on 3 websites.
- Agency: USD 211/month for up to 20 million pageviews/month on 20 websites.
- Enterprise: Custom pricing based on demand.
| Consent management for website, mobile apps, connected TVs | No geolocation capabilities |
| GDPR-compliant servers | |
| Integrated cookie checker |
3. Iubenda
iubenda provides a complete set of what they refer to as attorney-level privacy and consent management tools to help ensure your website and apps are compliant with laws across multiple jurisdictions. While it’s a Google-certified CMP partner, not all GDPR and CCPA compliance features are available in every plan.
Key features
- Consent Database: Access and review consent records via a user-friendly database.
- Data processing activities register: Document how you store and use the data you collect from your website and app visitors.
- Policy generators: Easily generate and manage privacy and cookie policies that comply with main international laws.
iubenda pricing
- Essentials: USD 5.99/month per site or app
- Advanced: USD 24.99/month per site or app
- Ultimate: USD 99.99/month per site or app
| Attorney-level compliance solutions | Only 11 languages available on consent banners |
| Customizable cookie and privacy policies | |
| Automatic cookie classification |
4. Didomi
Didomi is a cloud-based CMP that the company touts as seamlessly integrating into businesses’ existing tech stacks to make it easier to achieve compliance with major data privacy laws. Unfortunately, the platform doesn’t offer ready to use solutions, so you’ll need to go through a consultation process to establish which tools will meet your needs.
Key features
- Multi-regulation CMP: Geotargeted consent banners tailored to user location.
- Global privacy control: Implement appropriate data collection measures based on users’ previous consent choices.
- Consent versions and proofs: Track consent history across various versions of notices to see what users agreed to at any point in time.
Didomi pricing
Contact Didomi for pricing for Content Essentials, Core Privacy UX, and Privacy UX Plus plans.
| APIs and SDKs for seamless integration with existing infrastructure | Opaque pricing |
| Granular consent controls | |
| Customer support via live chat and email |
5. Osano

Osano supports compliance for more than 11,000 organizations worldwide with its unified consent and preference hub. Although it has some powerful features, some users note that customization options are limited.
Key features
- Cookie Consent: CMP for complying with regulations in over 50 countries.
- Data mapping: Generate visualizations of your data collection and processing practices to help identify potential risks and opportunities.
- Regulatory updates: Receive notifications about changes to the data privacy laws and regulations applicable to your business.
Osano pricing
Osano has two self-service cookie consent packages:
- Free: USD 0/month for 1 user, 1 domain, and up to 5,000 visitors/month
- Plus: USD 199/month for 2 users, 3 domains, and up to 30,000/month
Contact Osano for pricing for the Privacy & Trust Assurance, Privacy Essentials, and Privacy Operations & Government plans.
| “No Fines, No Penalties” Pledge | Free plan only supports 5,000 monthly visitors |
| Free tier | |
| Data stored on blockchain |
6. Cookie Information

Cookie Information equips businesses with the tools they need to deploy cookie banners and privacy notices that comply with the GDPR, CCPA, and other data privacy laws. However, some users note they would like more customization options.
Key features
- Data discovery: Find and flag data management practices that don’t comply with your organization’s policies.
- Compliance dashboard: Mitigate risks by tracking compliance with the GDPR and ePrivacy Directive across your entire digital portfolio from one place.
- Customer data platform: Segment data to create custom audiences and serve personalized adverts to data subjects.
Cookie Information pricing
- Essential: From EUR 15/month/domain
- Professional: From EUR 34/month/domain
| Free 30-day trial | No geotargeting |
| Robust analytics | |
| Daily and weekly website scans |
Choosing the right compliance management tool
Whether you need to achieve GDPR or CCPA compliance, selecting the right compliance management tool is crucial.
A reliable solution will help you continuously meet the requirements of applicable laws while avoiding the risks associated with noncompliance.
Compliance processes you should consider
The actions your business will need to take in relation to data collection and processing will depend on the jurisdictions where your audiences are located.
Here are a few of the most important regulations to keep in mind, along with their main requirements.
- General Data Protection Regulation (GDPR): Obtain explicit consent for collecting and processing data from users in the EU, no matter where your business is located.
- California Consumer Privacy Act (CCPA): Enforce California users’ right to know what data you’re collecting, as well as the right to delete data and opt out of data sales.
- Virginia Consumer Data Protection Act (VCDPA): Provide data subjects in Virginia with the right to access, correct, and delete data.
- Lei Geral de Proteção de Dados (LGPD): Obtain Brazilian users’ explicit consent for data collection and enforce their rights to access, correct, and delete that information.
- Protection of Personal Information Act (POPIA): Secure South African data subjects’ consent for data processing and provide transparency about data usage.
- Federal Act on Data Protection (FADP): Ensure transparent, lawful, and purpose limited collection and processing of Swiss users’ data.
- Transparency & Consent Framework (TCF v2.2): Provide clear consent management frameworks and ensure that data subjects can easily manage their consent choices.
Factors to consider when choosing a compliance management solution
Compliance management tools make it easier to adhere to multiple data privacy laws simultaneously. The platform you choose should enable you to:
- Obtain explicit, informed consent
- Enable multi-jurisdictional compliance
- Maintain detailed records of consent and data processing activities
- Protect user data from being transferred to unauthorized third-party recipients
- Ensure audit preparedness
Usercentrics CMP is a robust data compliance management solution that enables you to offer your users location-driven and granular consent management options. The platform comes with functionality to streamline compliance processes by reducing the amount of manual input required to increase opt-ins, maintain consented data, and meet rigorous compliance requirements.
In addition to enabling compliance with international regulations and frameworks, Usercentrics is Google-certified and comes integrated with Google Consent Mode v2, so you can continue with digital advertising in the EU, UK, and Switzerland uninterrupted. This helps you to ensure your users can effectively signal and manage their consent in a way that complies with Google’s requirements under the Digital Markets Act (DMA) and the updated EU user consent policy.
Potential compliance risks
Data management and compliance are becoming increasingly important, and not just because of the financial risks that come from falling short of legal requirements.
- Fines and penalties: Most data privacy regulations impose hefty fines on businesses that don’t comply. For example, under the GDPR, businesses can be fined up to EUR 20 million or 4 percent of the global annual turnover, whichever is higher, for repeat or more serious offenses.
- Loss of market share: Consumers are increasingly aware of their data privacy rights and prefer to engage with businesses that prioritize and enforce them. Failure to comply with data privacy laws can reduce customer trust and result in a loss of market share.
- Legal actions: Individuals and groups affected by incidents that flow from noncompliance, such as data breaches, can decide to take legal action against a business under some laws.
- Regulatory scrutiny: Persistent failure to adhere to data privacy regulations or severe violations of these laws may attract increased scrutiny from regulatory bodies. This can result in closer monitoring and more frequent audits and documentation requirements, which may inflate ongoing compliance costs and resource demands.
- Operational disruptions: Audits, investigations, and other adverse events that result from noncompliance can disrupt your business operations, including orders to cease certain operations and/or delete data. This can make it difficult to do business effectively and to grow.
Who should be responsible for compliance operations within an organization?
Data privacy laws affect every department in your organization. From the importance of consent management for digital marketers to compliance-related tasks for human resources and customer service, dedicated compliance officers, like a Data Protection Officer (DPO) or management teams should oversee compliance across the company.
However, if you want to minimize manual effort — and the risk of errors that comes along with it — these individuals shouldn’t be left to manage compliance operations on their own. Equip them with a robust compliance management tool to help teams to stay up to date with evolving laws and business requirements and reduce the complexity involved.
Using compliance management software to consolidate activities and automate tasks can optimize your team’s output and enable your organization to remain proactive while minimizing the risks associated with noncompliance.
Usercentrics CMP for streamlined compliance processes
Failing to comply with data privacy laws can lead to hefty fines, reputational damage, and legal actions that can negatively affect your organization’s bottom line.
When it comes to achieving and maintaining compliance, Usercentrics’ CMP offers dynamic and comprehensive consent management tools that help you adhere to the numerous data privacy regulations in effect across the globe.
By streamlining the collection and management of user consent and making it easier to track regulatory changes, Usercentrics helps businesses in 195 countries to achieve and maintain privacy compliance.
The information presented in this article is provided for educational purposes only. Engaging qualified legal counsel or privacy specialists regarding data privacy and protection issues and operations when evaluating solutions is always recommended. This information is accurate based on these publicly available sources as of the date of publication. Details about products, features, pricing, etc. may change over time.